- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 2.4 internal CA issues two certs for each client onboarded
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2018 02:59 PM
Hello
I was testing Wireless BYOD in my lab ISE 2.4 patch 3 and I noticed that each time I on-boarded my iPhone, ISE issued two certs for the device. Is this normal?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2018 04:28 AM
This is by design. The iOS flow utilizes two certificates and the one shown with proper x.509 fields that matches the EAP certificate template is the one the endpoint uses for authentication. It was decided to show both certificates in the ISE UI as both are related to the flow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2018 05:57 AM
Arne how many profiles do you have assigned to the endpoint?
I am thinking you might have the default profile and another profile for NSP enabled at same time
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2018 05:58 PM
Hi Jason
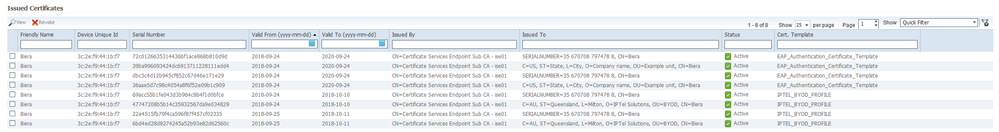
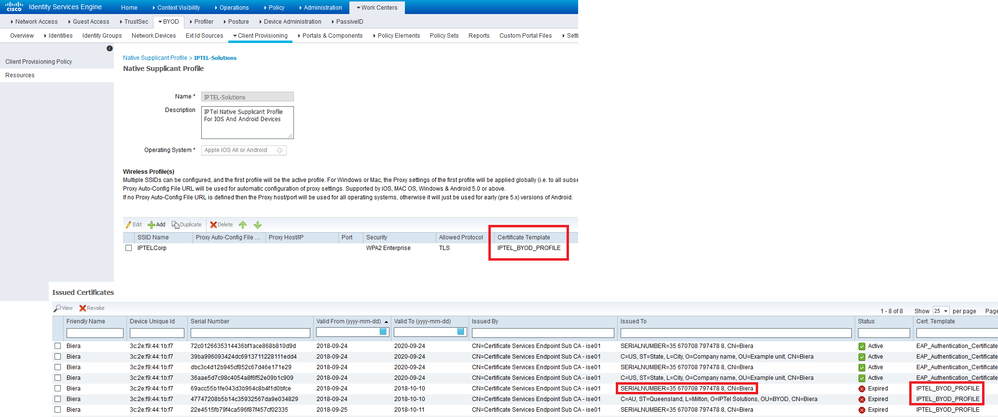
We definitely only have one profile associated as shown below. I can't figure out where ISE populates the Issued To "SERIALNUMBER...." stuff. What is that? I don't know how I would even configure that in ISE because it's not part of the standard certificate profile.
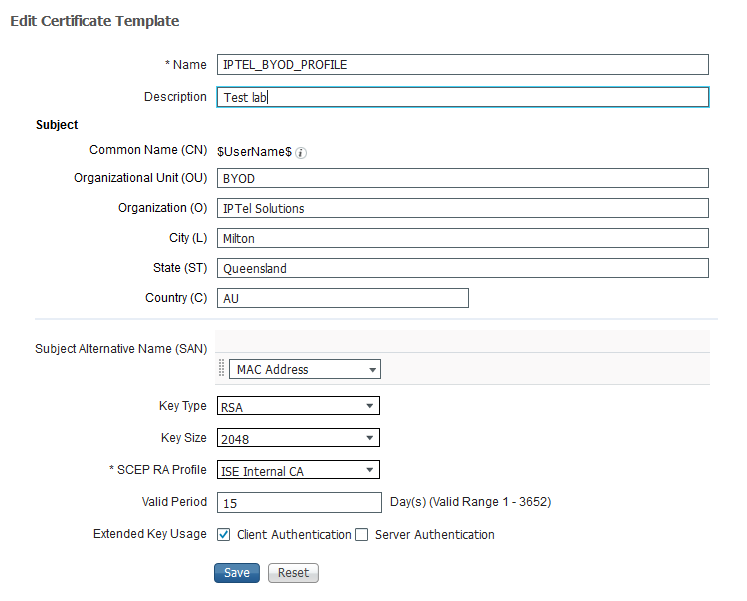
And this is the cert profile we use in the lab - the Subject is always hard code to include username and all the usual organisational stuff. I have no option to include a SERIALNUMBER here. It seems like a bug because ISE should not be creating certs with such a Subject (unless there is a bug in the supplicant provisioning code)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2018 06:30 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2018 08:56 PM
I'll see if I can get around to that. It's a lab and I don't have a support contract for ISE. I was hoping someone in the forum could confirm whether they see the same thing?
I tested with Windows 10 and it's not a problem. It's an issue with iOS or the iOS onboarding. iOS 12.0.x
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2018 04:28 AM
This is by design. The iOS flow utilizes two certificates and the one shown with proper x.509 fields that matches the EAP certificate template is the one the endpoint uses for authentication. It was decided to show both certificates in the ISE UI as both are related to the flow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2018 06:06 AM
@howon Is this by Apple design? Weird because on the iOS device i can not find the other weird looking cert. Where does it live? I don’t understand what this second cert is used for.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2018 03:47 PM
Yes, this is by Apple's design. It is not visible from the profile screen but it is required to establish trust and for ISE to be able to push WiFi settings and actual signed certificate for network authentication.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide