- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.6 CLI Access through External Identity Store
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2019 07:13 AM - edited 12-06-2019 07:15 AM
Hi community,
I want to configure my AD as an external identity source for ISE CLI access. The only documentation I've found so far is this:
Maybe it's just me but in my opinion it doesn't cut it. Can anyone point me to a more comprehensive documentation? If it does not exist, I think we should create it!
Thanks,
Jonathan
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2019 07:58 AM
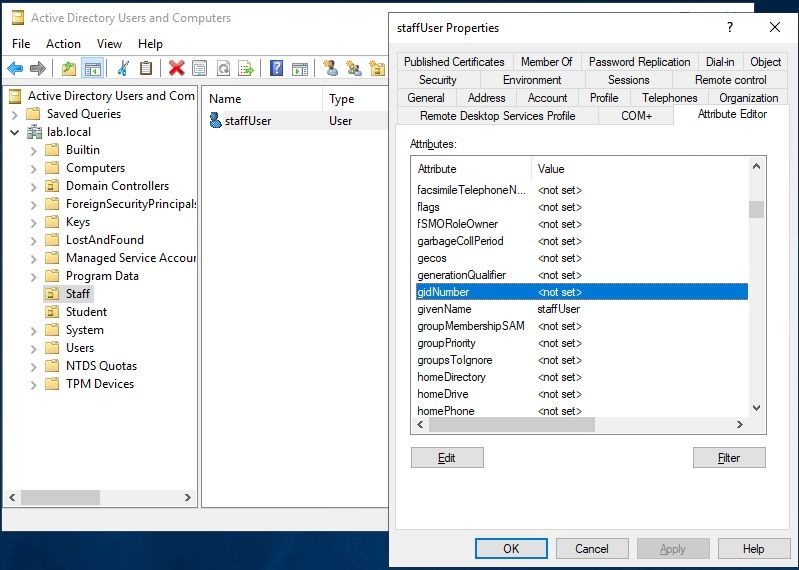
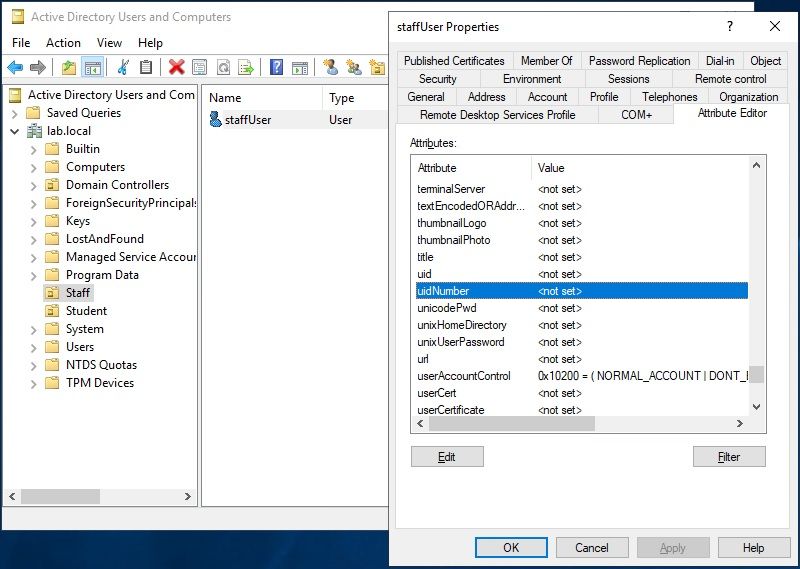
Within Active Directory, you can edit attributes for a particular user account. The documentation is saying to modify the "gidNumber" and "uidNumber" attributes in Active Directory for the account you want to use as the CLI Admin User. ISE will read those attributes to ensure the user is authorized to be a CLI Admin. These attributes are not used by Active Directory and are not set by default. So you can find your user within AD and go to Properties. Then select "Attribute Editor" to see/edit attributes. If you don't see the "Attribute Editor" tab, then you need to go to View and select the option for "Advanced". Then open Properties again and it will be there. Following are screenshots showing you the default settings for a user in AD for "gidNumber" and "uidNumber":
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2019 07:58 AM
Within Active Directory, you can edit attributes for a particular user account. The documentation is saying to modify the "gidNumber" and "uidNumber" attributes in Active Directory for the account you want to use as the CLI Admin User. ISE will read those attributes to ensure the user is authorized to be a CLI Admin. These attributes are not used by Active Directory and are not set by default. So you can find your user within AD and go to Properties. Then select "Attribute Editor" to see/edit attributes. If you don't see the "Attribute Editor" tab, then you need to go to View and select the option for "Advanced". Then open Properties again and it will be there. Following are screenshots showing you the default settings for a user in AD for "gidNumber" and "uidNumber":
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2019 02:54 AM
Super helpful, thanks a lot for this description! I have it now running in my lab...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2019 10:10 AM - edited 12-08-2019 10:22 AM
Colby.LeMaire is correct.
Attached is the section of our ISE 2.6 Update lab guide on this feature.
I also opened a doc bug to ask the admin and cli guides updated. CSCvs37998
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2019 03:04 AM
Thanks a lot for opening the defect. I really appreciate the effort by Product Management on this forum 👍🏻
Some feedback on the feature: I like it and I could make it run in a couple of minutes with this descriptive guide. I just hope we can avoid to rejoin the ISE node from the GUI in the future..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2020 02:54 AM
Hello @hslai ,
Is it not necessary to create any tacacs + rules on the ISE using the "gidNumber" and "uidNumber" parameters configured on the Active Directory side, except for active directory integration from the command line?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2020 08:06 AM - edited 06-03-2020 09:24 AM
Sp@wn ISE CLI Admin access is NOT using ISE T+ so no relationships to ISE T+ rules. I am guessing you are thinking about the admin CLI of Cisco PI, which allows T+.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2020 11:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2020 06:04 PM - edited 07-23-2020 06:05 PM
Assign gidNumber as 110 or 111.
GidNumber 110 denotes an admin user whereas 111 denotes a read-only user.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2020 01:18 AM
I am trying to understand the configuration made on ISE side for the CLI Access through External Identity Store. I read the document you shared. I did not see a configuration example related with GidNumber on the ISE side, but I encountered the following contradictory statement.
Administrators who belong to a Super Admin group, and are configured to authenticate and authorize using an external identity store, can also authenticate with the external identity store for CLI access.
 Note Note | You can configure this method of providing external administrator authentication only via the Admin portal. The Cisco ISE Command Line Interface (CLI) does not feature these functions. |
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide