- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.7 CLI access using Active Directory credentials
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-08-2020 10:00 PM - edited 03-08-2020 10:06 PM
Hello ISE 2.7 users
I was so excited when I heard that in ISE 2.7 I could finally SSH into my nodes using AD credentials.
This should have been a simple 5 minute job for me.
According to the ISE 2.7 Admin Guide on how to configure the node to allow AD credentials for CLI logins this should be simple.
There is documentation bug on that page because it asks to "run" the identity store command - instead of saying that this is a configuration option under conf t.
Connect to the Cisco ISE CLI, run the identity-store command, and assign the Admin user to the ID store. For example, to map the CLI admin user to the Active Directory defined in ISE as adpool1, run identity-store active-directory domain-name adpool1 user admincliuser.
The first thing that threw me off is that I now have to edit my AD Admin User(s) - the UI equivalent never required any manual tuning of this user. Anyway - minor gripe ... I edited my AD user as indicated
Assign uidNumber greater than 60000, and make sure that the number is unique. Assign gidNumber as 110 (admin user) or 111 (read-only)
I then ran the CLI command to join the Domain. This is where I shook my head again. This node is already joined to the AD. Why am I having to do this again ? I tried the identity-store command once, and then I opened a new SSH window, but the AD credentials were not accepted. I even left and re-joined the AD via CLI, but it doesn't allow me to login with the user shown below.
ise03/admin(config)# no identity-store active-directory domain-name somedomain.com.au user admin-biera Left the domain somedomain.com.au successfully ise03/admin(config)# identity-store active-directory domain-name somedomain.com.au user admin-biera If the domain somedomain.com.au is already joined via UI, then you must rejoin the domain somedomain.com.au from UI after this configuration. Until the rejoin happens, authentications to somedomain.com.au will fail Do you want to proceed? Y/N [N]: Y Password for admin-biera: Joined to domain somedomain.com.au successfully ise03/admin(config)# end ise03/admin#
As the message above indicated, after I did the CLI "AD Join", it breaks the GUI AD Join Point (which is not great - I had to leave the AD Join int he GUI and then re-join ... then all was ok again).
What am I doing wrong regarding the CLI login. Is there a missing step?
In general:
- Do I have to re-join the domain with all of my admin users? Surely not ...
- If I have more than one ISE node, do I have to go through this "weird AD join on the CLI" on every node?
Any hints welcome
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2020 02:42 PM
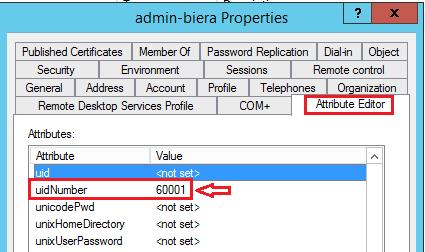
Update: I changed the wrong AD attribute - I was searching for "uid" by pressing "u" to search through the list - and I edited the first search result that came back - uid. Which was a mistake, because I needed to edit uidNumber. At least I won't forget that next time ;-) - the AD login on CLI now works after changing the uidNumber to a value > 60000.
If anyone has insights/answer to the other questions I'd be happy to hear from you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2020 02:42 PM
Update: I changed the wrong AD attribute - I was searching for "uid" by pressing "u" to search through the list - and I edited the first search result that came back - uid. Which was a mistake, because I needed to edit uidNumber. At least I won't forget that next time ;-) - the AD login on CLI now works after changing the uidNumber to a value > 60000.
If anyone has insights/answer to the other questions I'd be happy to hear from you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2020 11:10 AM
Hi,
I'm glad someone tested this before me :) I looked at the documentation myself couple of days ago, and the steps need to be followed in a specific order, I'm not sure exactly why, most probably it has to do with behind the scenes functionality and order of operation). One of the things which it states is exactly that if you use the same join point as defined in the GUI, you would have to rejoin from the GUI; doesn't sound like the perfect outcome for a customer, but probably/hopefully it will improve with future versions, so there will be no more need to loose AD access for a while.
Did you make it work in the end?
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2020 04:41 PM
yeah I got it working - in my first attempt I assigned a value to the wrong AD attribute - I then realised my mistake and updated the correct attribute. It works like a charm. I only have two AD users configured and tested with this.
I would have preferred a solution that just copied the same behaviour as the GUI Admin AD Integration ... it seems that CLI and GUI use completely different code to authenticate the admin users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 01:25 PM
Arne,
Thank you for your insights on this. I have passed this on to PM/Engineering to look.
Thanks
Krishnan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2020 04:58 PM
So the process you have described is exactly the same as I had to undertake in ISE 2.6 and I agree, why is the CLI auth process (domain join and user properties etc) different between CLI and GUI? I guess it is due to the GUI being a separate application on the appliance vs the host OS process.
It is a pain having to do the CLI first and then leave and join the GUI if it was already joined.
So good to know the process is still the same in 2.7
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 02:29 PM
Hi,
If you ask me, the feature came out on a rush, as most customers would want to use the same AD in the CLI as in the GUI, but they don't want that when the process is done, the GUI needs to rejoin the AD, thus leaving a window when news users will not be able to get authenticated/authorized.
Initially i thought the same, that indeed because the CLI and GUI are two different entities (even though run as OS/RHEL and ISE application on top of it), the integration of CLI and GUI with AD are two different process, but than how come that if you use in the CLI the same Join Point as in the GUI, it breaks the GUI attachment and you would need to rejoin?
If you ask me, this is gonna get fixed on next releases in one of two ways:
- either CLI can make use of the same Join Point as the GUI with no need to rejoin the GUI or join at all from CLI
- either CLI joining the AD will no longer break the GUI AD Join; like now, but without sacrificing anything
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2020 01:03 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2020 11:02 PM
CSCvs60879 is a known issue on this feature.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2021 02:01 AM
Hi Arne
u would probably want to disable it again because of https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ise-priv-esc-fNZX8hHj
otherwise upgrade to 3.0 :0)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2021 03:04 AM
Thanks for that little heads up;-) I deleted 2.7 months ago. For some reason my 2.4 -> 2.7 upgrade ended up being a disaster (had to reboot once a week). I was put off by this bad experience. But I think it’s ok for others. I think the whole ISE CLI AD integration is a bit of a shambles. I don’t care much for it now. If they can implement it probably I might consider it again in future.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2021 12:21 PM
Hi All,
I am trying to achieve the ISE CLI Integration with AD, I was able to successfully add the user using identity store and it works fine on all nodes after I added manually to all ISE nodes.
It seems like documentation is not clear or there is some kind of issue as if I need to add another user from same AD group it does not give me an option add the password for that user , generally it should ask the admin user who we want to integrate with CLI as a manual option.
It only works with the first user and since then the AD is already added we cannot add another user from the same group, is it a BUG or configuration issue.
Regards,
Meh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2021 03:44 AM
@net87 - not sure what you mean. Can you rephrase the last two sentences please.
I have given up on this feature because it's so badly implemented. I'll wait and see if it improves. It took Cisco 7 years to add authenticated SMTP to ISE. Fingers crossed ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2021 07:51 AM
Hi Arne,
Let us say I have 4 users in ciscoadmin group in AD.
I performed following steps as per cisco documentation
1) I added the identity store command and it asked for the password for the first user and then it worked well after joining back the ISE nodes.
Now since the CLI already has the domain added with the first user, I am unable to add the second user as it must ask for a password to sync it back to CLI ( the way document explains). It only says domain is already added.
Regards,
Meh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2022 08:31 AM
Hi, we are running into this same issue regarding adding multiple ad users as admins to ISE CLI. Did you find a solution?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: