- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.7 P6 and connections to MS Azure via MDM
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE 2.7 P6 and connections to MS Azure via MDM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2022 04:02 AM - edited 05-04-2022 04:20 AM
Hi, folks.
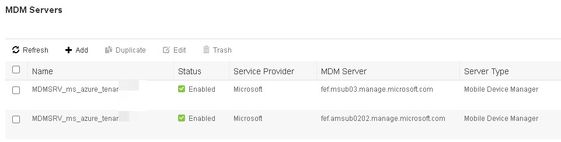
Has anyone run ISE with more than one Azure MDM connection (more than one tenant) successfully ??
A customer has several BusinessAreaUnits, each of them has its own MS Azure tenant .....
ISE is the central authen/autho platform and has MDM connections successfully configured for each of the tenants.
If a client joins any Azure tenant, it receives a certificate and the issuing chain from the tenant.
The idea is to use the certificate it received for 802.1x authentication using EAP-TLS, which works fine.
Problems begin with authorization:
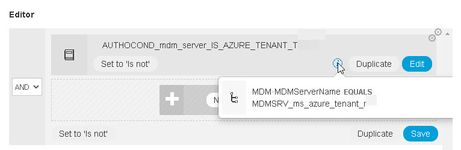
Since clients from both tenants need to be treated differently on the network, an authorization condition has been configured to check for the tenant the client belongs to.
The condition is using the MDMServerName attribute, like this:
The intention is to check if this condition returns "TRUE", if so, then we can be sure that this client is
a member of exactly this tenant, and proceed accordingly.
In addtion to this, the compliance of this client is checked using the MDM attribute DeviceCompliantStatus:
If both of these condition return "TRUE", the client is authorized and permitted onto the network.
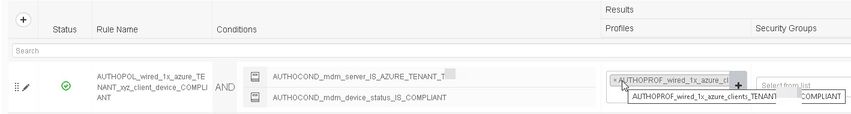
This is what the authorization rule looks like:
Up to this point, this works perfectly .....
Now, if you add another authorization rule directly below this first one, using the exact same structure, only difference being the condition checking if the SECOND MDMServerName attribute is "TRUE", clients from the SECOND tenant will either falsely be associated with the tentant in the FIRST rule, or not associated to any tenant (and rule) at all (hitting the default-DENY rule) !!!!!
The second authorization rule will never get hit !!!!
Seems like ISE has problems differentiating configured MDM tenants ....
How is ISE handling these requests to MS Azure ?? Is this working like it supposed to be ??
Is there another way to differentiate MS Azure Clients from various tenants using 802.1x ???
Any clues will be appreciated......
Rgs
Frank
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2022 05:25 AM - edited 05-04-2022 05:35 AM
Further testing has shown the following:
If the client is NOT KNOWN by ISE (no record in database) and the tenant in the FIRST RULE that is checked is NOT the correct tenant of the device (the second rule would be the correct one), the clients hits the Default-Deny rule ......
The second rule is not checked (because if tenant would be checked, it would match !!!!) ....
Why is the second tenant not checked, when the tenant that is checked first is the "wrong" one ??
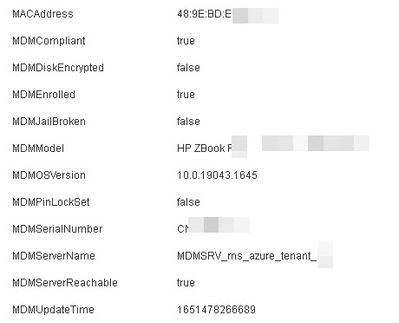
If the "matching-tenant-rule" is moved from the second place to the top (to be checked first), the client is correctly authorized and
the correct MDM parameters show up in the client entry in ISE database
Rgs
Frank
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide