- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE - AD & Internal User Access for the same device
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2021 11:18 PM
Hi Team,
I'm having some issue that I'm almost sure that I've succeeded with it in the past.
We have a device type "x", and we want the following thing :
1. Admins user [an AD group] - will have privilege 15
2. Internal User "user" - will be able to run only specific command [we've created the command set "command"]
I can't find/think on a way, that in the same "Device Admin Policy Set"
What Am I doing wrong ? and how can I solve it please
Thanks in advance
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2021 09:18 AM
Hello,
From my understanding you want on the same policy to authenticate and differentiate the authorization between AD Users and ISE Internal Users.(The AD User should not be the same as the ISE internal User).
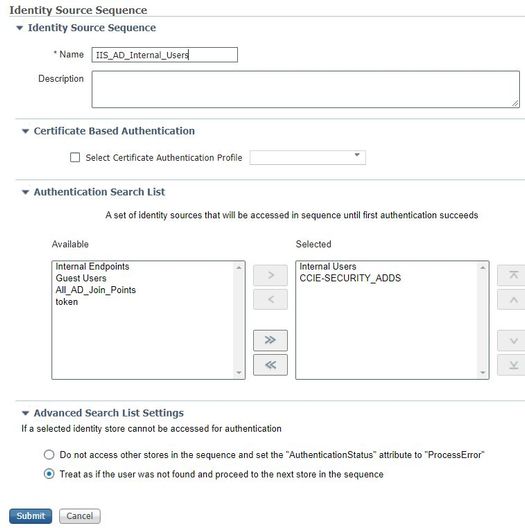
First you need to create an Identity Source Sequence (Administration Identity -> Identity Management -> Identity Source Sequences)
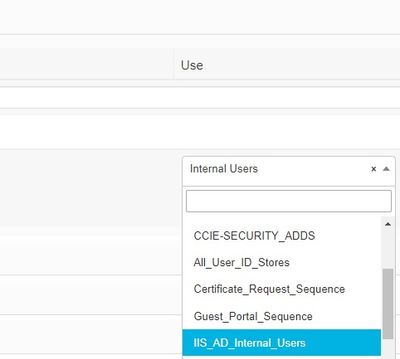
Under the Authentication Policy choose the Identity sequence you have created :
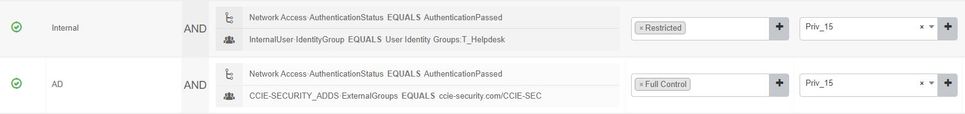
And under Authorization policy should be like this :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2021 03:33 AM
You need to look command set :
Work Centers > Device Administration > Policy Results > TACACS Command Sets
below document help you : (Let us know if this is not the case or am I miss understood your requirement ?)
https://ciscocustomer.lookbookhq.com/iseguidedjourney/ISE-device-admin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2021 04:36 AM
Hi, and thanks for your reply.
But, It's not what I've asked for.
We already have a command set for the internal user.
We need that for the same device, there will be an option the users from External ID Source [AD] and Internal ISE Users will be able to login.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2021 05:25 AM
Personally, I do not believe that Device can do both, there is only Option First one, and if that fails to the second one.
Identity Source Sequence that will contain AD groups and if needed any local accounts on ISE (in the event that AD can’t be reachable or failed, you have a local ISE account to log into your equipment).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2021 09:18 AM
Hello,
From my understanding you want on the same policy to authenticate and differentiate the authorization between AD Users and ISE Internal Users.(The AD User should not be the same as the ISE internal User).
First you need to create an Identity Source Sequence (Administration Identity -> Identity Management -> Identity Source Sequences)
Under the Authentication Policy choose the Identity sequence you have created :
And under Authorization policy should be like this :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
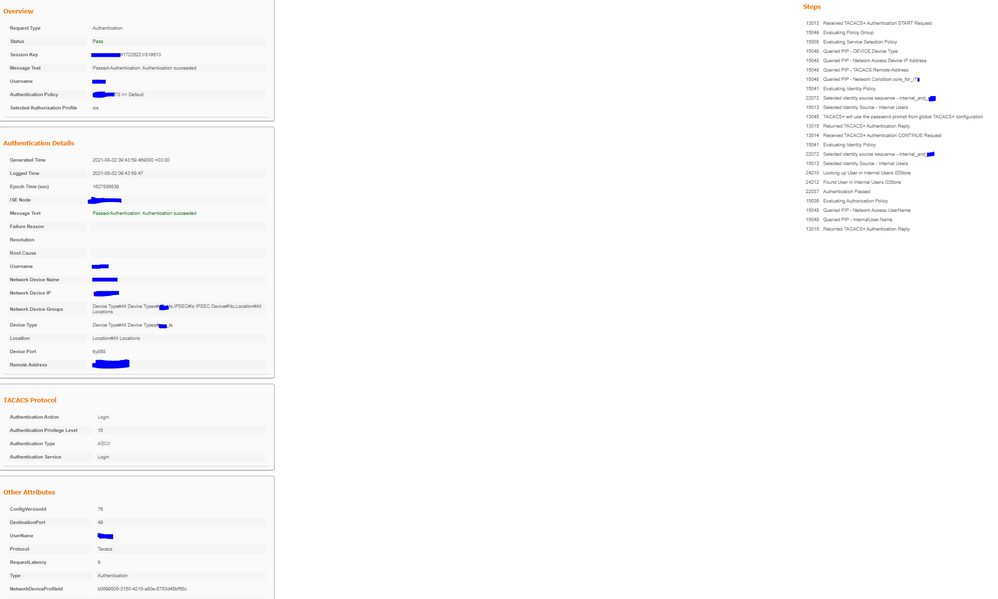
08-02-2021 12:03 AM
Hi Amine
Thanks ! It's getting closer for solution.
Now I'm able to login with both AD user & Internal User
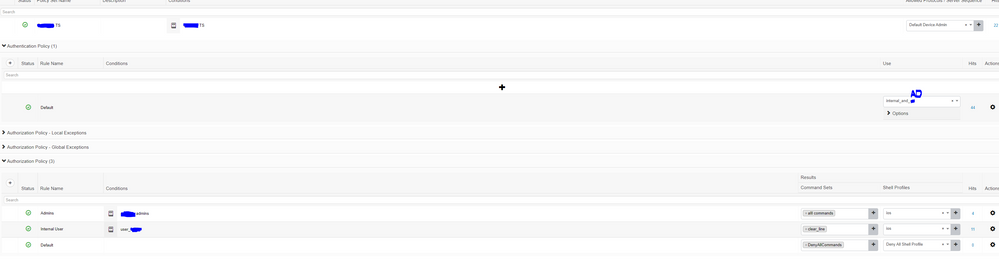
But, for some reason, the Command Sets are not taking any effect. i.e, the users can login but they have priv 15, and not only the "clear line" command set...
Do you have any Idea why ?
BTW -
In other Policy Sets it's working. the "users" can login and get only "clear line" command set, and admins getting all command.
The only change is that in the other Policy Sets, the "users" are from the same Identity Source as the admins [AD].
Attached the Policy Set + The TACACS Log
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2021 12:37 AM
*********
Update
*********
IT IS WORKING !
I've noticed that something is wrong only with a specific Terminal Server.
There was one command that was missing :
aaa authorization commands 15 default local group tacacs+
and that's it now it's working !
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2021 02:43 AM
aaa authorization commands 15 default local group tacacs+
Sure this make sense - this will do first Local and TACACS later.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: