- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE as an Intermediate CA for BYOD
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2016 08:23 PM
Anyone out there experienced with using ISE as an Intermediate CA for BYOD?
When using ISE as an intermediate CA we seem to get odd results in the windows client certificate issued by the BYOD process. We have observed the same in ISE 1.3 and 2.0 patch 3. Although the cert works, certificate information seems to be missing info we normally see as you can see in the screen captures below.
I would have thought the certification path (in the second picture) would show the root CA, intermediate CA and finally the user cert. Is it because the client doesn’t have the Intermediate CA certificate? If so how can you get this from ISE and why doesn’t it push it automatically along with the root certificate?
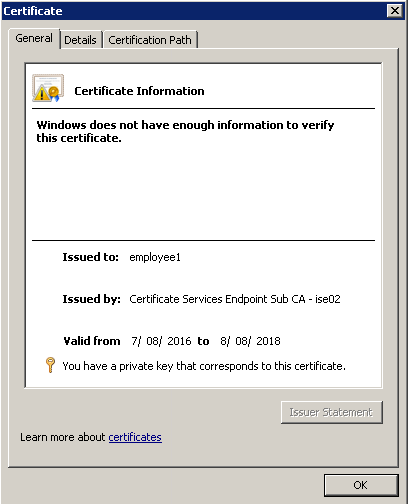
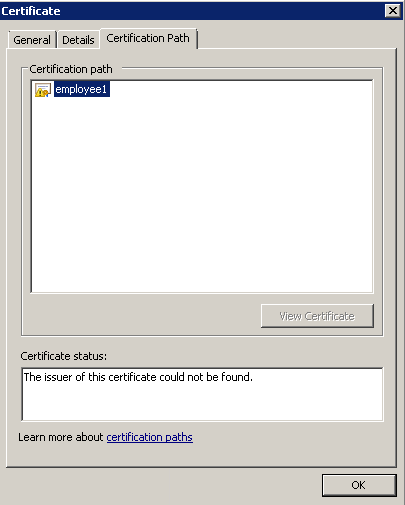
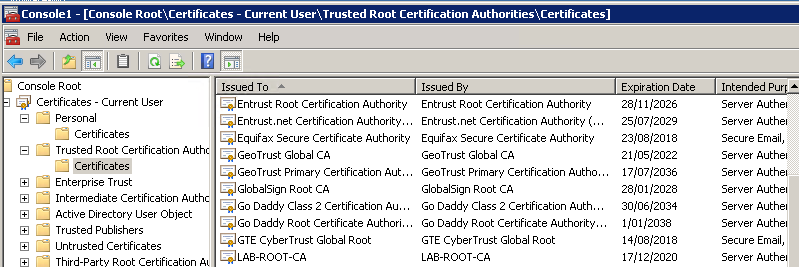
Root CA is installed:
ISE Auth is successful:
![]()
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2016 11:14 PM
This is expected. ISE itself has the certificate chain in its trusted store so ISE can authenticate the endpoints with their TLS certificates. Normally, the clients only need to trust ISE server certificate(s) so no need to install the full certificate chain for the client on the endpoints.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2016 11:14 PM
This is expected. ISE itself has the certificate chain in its trusted store so ISE can authenticate the endpoints with their TLS certificates. Normally, the clients only need to trust ISE server certificate(s) so no need to install the full certificate chain for the client on the endpoints.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2017 03:34 PM
HI, I think this might be true for a windows client. EAP-TLS runs like a charm on our wind clients, apple devices always complaining about the untrusted certificate chain. any suggestions how to solve this on apple devices?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2017 07:00 AM
Apple devices always ask you to trust valid certificates when first connecting, make sure to use wilidcard in the san for your PSNs so that clients only need to accept RADIUS nodes 1x
See the following posts
http://www.cisco.com/c/en/us/td/docs/security/ise/2-0/admin_guide/b_ise_admin_guide_20/b_ise_admin_guide_20_chapter_0111.html#concept_8ECCCAF1252E40DDB9A786C0AC7BC3B2
https://communities.cisco.com/docs/DOC-71398
https://discussions.apple.com/thread/7381797?start=0&tstart=0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2016 03:04 PM
Thanks hslai. That makes sense and is what I thought was happening but doesn't confirm to me why windows certificate manager show's what it does. Is it because windows doesn't have the ISE intermediate certificate that certificate manager is unable to display the full certificate hierachy?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

