- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE EAP-TLS authentication of devices from two different domains
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE EAP-TLS authentication of devices from two different domains
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2020 07:44 AM
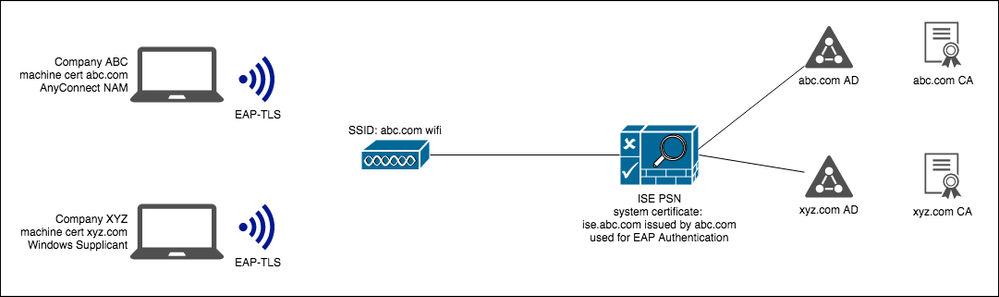
Currently ISE is deployed at company abc and is joined to abc.com Active Directory and Certificate Authority. abc SoE machines are using AnyConnect NAM with machine certificates issued by the abc.com CA and doing EAP-TLS. They connect to abc's wifi. The system certificate on the ISE nodes for EAP Authentication is issued by abc CA.
Another company (xyz) has recently merged with abc. xyz employees have SoE's in xyz.com domain and machine certificates issued by their own CA. Is it possible for xyz SoE machines to connect to abc's wifi and utilize EAP-TLS with abc's ISE? This question has come up before in the support forum, and discussed about how the ISE needs to have xyz CA/root certificate imported and trusted and the xyz SoE machine will need to have abc's CA/root certificate in its trusted store along with ISE also joined to xyz.com AD. But I am confused about the part where ISE's system certificate used for EAP Authentication is issued by abc CA. EAP authentication can only be linked to one certificate in ISE (unlike portal's). Will this cause problems and will it work? If not is the alternative to have xyz SoE machines use PEAP?
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2020 07:58 AM
Hi,
This is no different than for example an IPsec tunnel with Certificate based authentication, where the two VPN gateways have their certificates issued by different CA's. As long as each side has its own certificate valid (valid dates and the root CA/Subordinate CA's certificates imported in order to recurse/validate its own certificate) and trusts the CA that issued the certificate for the other side, it's gonna work.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2020 09:00 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2020 05:27 PM
Hi @Cristian Matei @Mike.Cifelli thanks for your responses, but what about this discussion - https://community.cisco.com/t5/network-access-control/ise-two-end-user-certificates/td-p/3529859
where Cisco have said its not possible? For EAP-TLS ISE will present a certificate to the client, in this setup ISE will present the abc certificate to the xyz client, and xyz will present its xyz machine certificate - hence a certificate mismatch?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2020 03:43 AM
Hi,
The discussion is tailored towards the fact that ISE can't use for more than one system certificate for EAP. But this does not mean that if the remote endpoint's certificate is issued by another CA than the ISE certificate, EAP will fail. There could be specific EAP clients/supplicants which are hardware coded so that the NAS certificate needs to be issued by a specific CA or the same CA that issue the certificate for the EAP client, in which case, EAP fails for xyz domain, if xyz are such EAP clients. I'm not aware of such EAP clients, though.
It's also true that depending on the EAP client/supplicant functionalities, you may be able to configure restrictions, so that the NAS certificate is issued by the same CA as the EAP client CA, but these are optional, not defaults and not hardcoded.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2020 07:40 AM
So essentially a client could issue themselves a certificate from one of the well known public CA's by default that's included in the trusted store of ISE and can authenticate using EAP-TLS if the ISE policy conditions isn't locked down specifically to a particular CA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2020 09:09 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2020 09:15 AM
Hi,
If certificate chain is trusted both ways, yes. But as i stated, this behaviour is expected, as it's not specific to ISE/EAP, but to any certificate-to-certificate based authentication, where no additional constraints are specified.
Regards,
Cristian Matei.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide