- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE has not confirmed locally previous successful machine authentication for user in Active Dire...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2018 08:04 AM - edited 02-21-2020 11:01 AM
ISE 2.3.0.298
External Sources: AD
Mode: Monitor
MAR: On (12hrs)
Cisco Phones-EAP
Switches: Correctly Configured per Interface
Policy:
Authentication:
EAP-TLS - Network Access·EapTunnel Equals TTLS - Use Sequence (Internal Endpoints, AD) [hit=0]
Wired_MAB - Wired_MAB - Use Sequence (Internal Endpoint) [hit=9907]
Authorization Policy
hit=0
Printers:
Network Access - EapAuthentication EQUALS EAP-TLS
IdentityGroup-Name EQUALS Endpoint Identity
Groups: HP_Printers
[Printers MAC Addresses are in there]
hit=54
Cisco_Phones:
IdentityGroup-Name EQUALS Endpoint Identity
Groups: Switch_Devices: Cisco_Phones
[Switch is in there and so is the Cisco Phone MAC Addresses]
Okay, So I am brand new with ISE so bare with me. However, I noticed they keep getting rejected with typically the following stages:
| 11001 | Received RADIUS Access-Request | |
| 11017 | RADIUS created a new session | |
| 11027 | Detected Host Lookup UseCase (Service-Type = Call Check (10)) | |
| 15049 | Evaluating Policy Group | |
| 15008 | Evaluating Service Selection Policy | |
| 15048 | Queried PIP | |
| 15048 | Queried PIP | |
| 15041 | Evaluating Identity Policy | |
| 15048 | Queried PIP | |
| 15048 | Queried PIP | |
| 15048 | Queried PIP | |
| 15048 | Queried PIP | |
| 22072 | Selected identity source sequence | |
| 15013 | Selected Identity Source - Internal Endpoints | |
| 24209 | Looking up Endpoint in Internal Endpoints IDStore - 48:BA:4E:**:**:** | |
| 24211 | Found Endpoint in Internal Endpoints IDStore | |
| 22037 | Authentication Passed | |
| 24715 | ISE has not confirmed locally previous successful machine authentication for user in Active Directory | |
| 15036 | Evaluating Authorization Policy | |
| 15048 | Queried PIP | |
| 24432 | Looking up user in Active Directory - 48:BA:4E:**:**:** | |
| 24325 | Resolving identity | |
| 24313 | Search for matching accounts at join point | |
| 24318 | No matching account found in forest | |
| 24322 | Identity resolution detected no matching account | |
| 24352 | Identity resolution failed | |
| 24412 | User not found in Active Directory | |
| 15048 | Queried PIP | |
| 15048 | Queried PIP | |
| 15016 | Selected Authorization Profile - DenyAccess | |
| 15039 | Rejected per authorization profile | |
| 11003 | Returned RADIUS Access-Reject | |
| 5434 |
Endpoint conducted several failed authentications of the same scenario |
Authentication Policy Wired Monitor Mode >> Wired_MAB
Authorization Policy Wired Monitor Mode >> Default
Authorization Result DenyAccess
StepData 5= DEVICE.Device Type
StepData 6= DEVICE.Mode
StepData 8= Network Access.EapTunnel
StepData 9= Network Access.EapAuthentication
StepData 10= Network Access.EapTunnel
StepData 11= Normalised Radius.RadiusFlowType
StepData 12=Internal_Endpoint_Sequence
StepData 13=Internal Endpoints
StepData 19= Network Access.EapTunnel
StepData 20= *.ad
This is similar to the phones and everything else every time when there is authentication rejected. I notice half the phones are authenticated and other half is not when checking on the switches. So what am I doing wrong?
Can cisco phones be placed in AD? How do I have it where for now it only views in the Internal_Endpoint? All I'm trying to do is to correctly have them authenticated now and THEN set up the complicated stuff.
Solved! Go to Solution.
- Labels:
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2018 11:01 AM
... ... 15036 Evaluating Authorization Policy 15048 Queried PIP 24432 Looking up user in Active Directory - 48:BA:4E:**:**:** ... ... 5434 Endpoint conducted several failed authentications of the same scenario
...
This is similar to the phones and everything else every time when there is authentication rejected. I notice half the phones are authenticated and other half is not when checking on the switches. So what am I doing wrong?
Can cisco phones be placed in AD? How do I have it where for now it only views in the Internal_Endpoint? All I'm trying to do is to correctly have them authenticated now and THEN set up the complicated stuff.
Configuring MAB with LDAP User Device Binding - Cisco shows how to perform MAB against an AD/LDAP store.
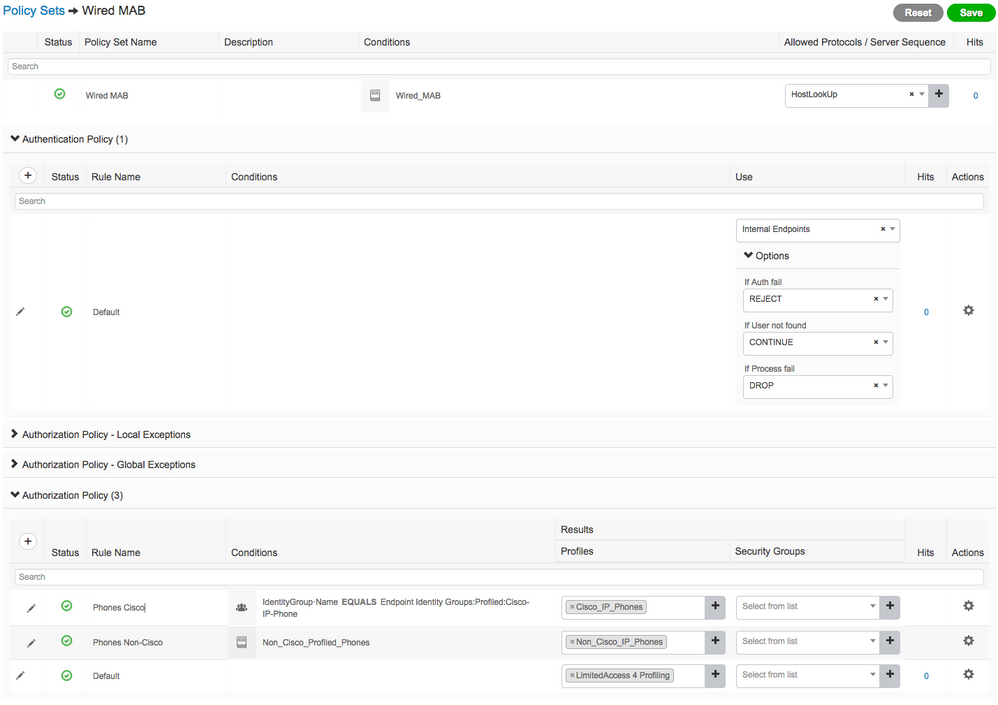
Your case seems to use Internal Endpoints only, so it's not optimal to query AD for phones. Ideally, you would want to create a policy set to separate Wired MAB from the others. For example,
Additionally, I would suggest you to check out Advanced ISE Services, Tips and Tricks - BRKSEC-3697
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2018 05:43 AM
Can you post up some screenshots of your configs and a concise description of what it is you're trying to do? If you can, we can help... there's not enough detail in the original post to guide you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2018 05:47 AM
Configurations is what was posted as I am looking at the GUI. Could you be specific as to what configs you are needing to look at?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2018 05:53 AM
Screenshots of your Authentication and Authorisation Policies - they're much easier to interpret as screenhots than text and it removes the chance you've mis-typed or mis-represented something when you converted it all to text.
It's also not clear what the actual problem is - which of your printers or phones does / does not work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2018 11:01 AM
... ... 15036 Evaluating Authorization Policy 15048 Queried PIP 24432 Looking up user in Active Directory - 48:BA:4E:**:**:** ... ... 5434 Endpoint conducted several failed authentications of the same scenario
...
This is similar to the phones and everything else every time when there is authentication rejected. I notice half the phones are authenticated and other half is not when checking on the switches. So what am I doing wrong?
Can cisco phones be placed in AD? How do I have it where for now it only views in the Internal_Endpoint? All I'm trying to do is to correctly have them authenticated now and THEN set up the complicated stuff.
Configuring MAB with LDAP User Device Binding - Cisco shows how to perform MAB against an AD/LDAP store.
Your case seems to use Internal Endpoints only, so it's not optimal to query AD for phones. Ideally, you would want to create a policy set to separate Wired MAB from the others. For example,
Additionally, I would suggest you to check out Advanced ISE Services, Tips and Tricks - BRKSEC-3697
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide