- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE is not accepting newly added swtiches
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2020 07:56 AM - edited 01-10-2020 07:57 AM
Hello guys,
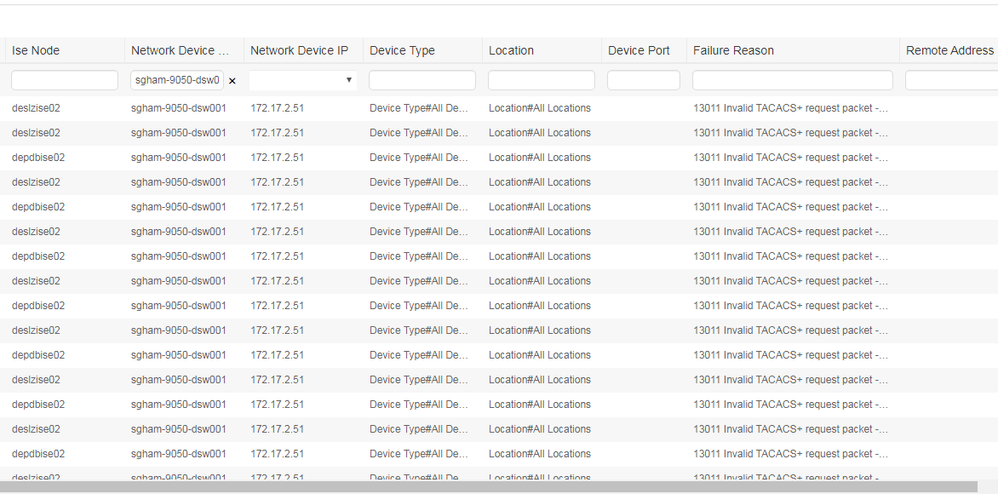
is there anything else what I can check when I getting error: 13011 Invalid TACACS+ request packet than key? (I tried to changed few times)
It look like there is some misconfiguration.
ISE:
Version 2.4.0.357 Installed Patches 9,10 Product Identifier (PID) SNS-3595-K9 Version Identifier (VID) A0 Serial Number (SN) FCH2209V02N ADE-OS Version 3.0.4.070
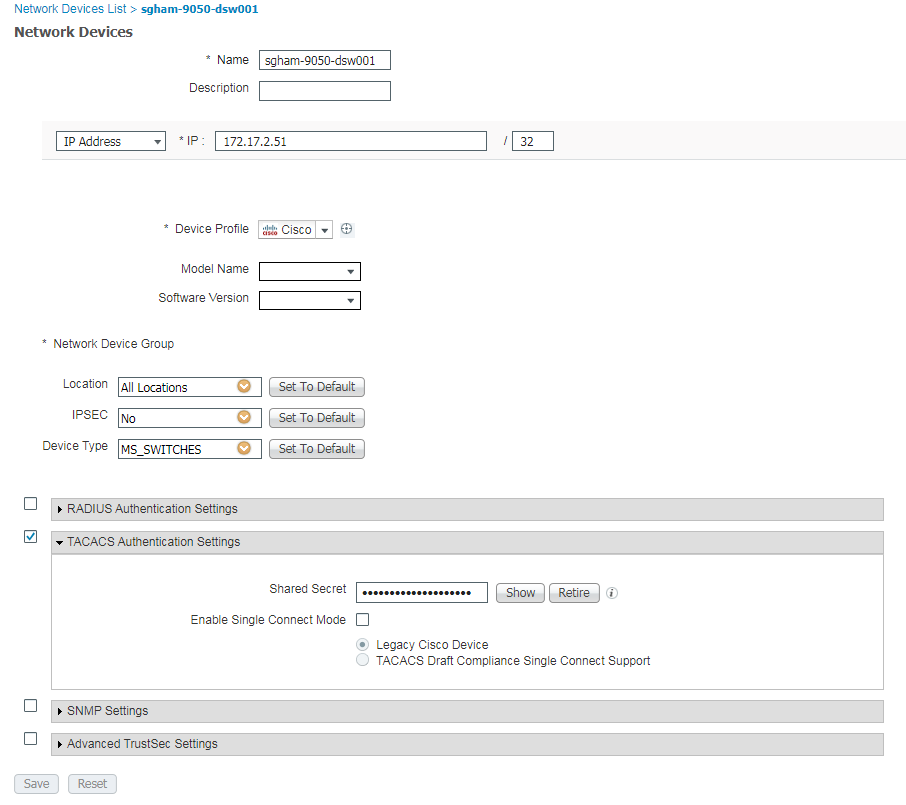
tacacs-server host 10.52.60.50 key 7 "XXX" timeout 4
tacacs-server host 10.52.188.50 key 7 "XXX" timeout 4
aaa group server tacacs+ DN_AUTH
server 10.52.60.50
server 10.52.188.50
deadtime 5
source-interface Vlan2Thank you very much.Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2020 07:16 AM
That is correct! Any device, Cisco or third-party, that adheres to the TACACS+ protocol standards will work with ISE. The compatibility matrix for ISE addresses the non-TACACS+ features of ISE, such as 802.1x, URL Redirect, TrustSec, etc.
Double check your configuration on the switch. Specifically, check the shared secret that you have setup on the switch and in ISE for that device. I would recommend entering it again manually and do not copy/paste. Sometimes you can have an extra space when copying/pasting or it may look like it pasted fine but you actually pasted something different that was copied previously. Manually type it in on ISE and then use the show secret button to show what is actually there. Then manually type it into the Nexus.
I have integrated many Nexus switches with ISE for TACACS+ and it works just fine. The error you reference points to a mismatched shared secret.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2020 08:20 AM
- Good thing to 'initially verify' is your switch-model + software version compared to ise version compatibility :
M.
-- ' 'Good body every evening' ' this sentence was once spotted on a logo at the entrance of a Weight Watchers Club !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2020 01:34 AM
Dear Concern,
Can you try changing shared key. I think shared key mismatch hepping there.
Thaks,
Zunaid
Skype: mzunaidbhuiyan
whatsapp: +8801962400050
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2020 12:45 AM
Hello guys,
I checked page for ISE 2.4: https://www.cisco.com/c/en/us/td/docs/security/ise/2-4/compatibility/b_ise_sdt_24.html
but I do not see there Nexus 9000. I checked higher version, but still the same result.
Do you know why is that please?
Switch:
Software BIOS: version 07.56 NXOS: version 7.0(3)I5(1) BIOS compile time: 06/08/2016 NXOS image file is: bootflash:///nxos.7.0.3.I5.1.bin NXOS compile time: 10/29/2016 6:00:00 [10/29/2016 13:46:41] Hardware cisco Nexus9000 93180YC-EX chassis Intel(R) Xeon(R) CPU @ 1.80GHz with 24633936 kB of memory. Processor Board ID FDO210314NL Device name: sgham-9050-dsw001 bootflash: 53298520 kB Kernel uptime is 990 day(s), 22 hour(s), 14 minute(s), 19 second(s)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2020 02:25 AM
Ref : no ISE support for nexus 9000
>Do you know why is that please?
I think it's primarily because ISE focuses on access layer switches , not on data-center switches.
M.
-- ' 'Good body every evening' ' this sentence was once spotted on a logo at the entrance of a Weight Watchers Club !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2020 03:31 AM
Thank you for explanation. Tacacs can be used, but not with ISE? This is current configuration which is working on Tacacs. Only servers 151 and 153 are in use.
ip domain-name XXX
tacacs-server host 172.24.191.151 key 7 "XXX" timeout 10
tacacs-server host 172.24.191.153 key 7 "XXX" timeout 10
tacacs-server host 172.24.191.131
tacacs-server host 10.52.60.50 key 7 "XXX" timeout 10
aaa group server tacacs+ DN_AUTH
server 172.24.191.151
server 172.24.191.153
deadtime 5
use-vrf ham
source-interface Vlan1504
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2020 03:41 AM
Hi - have you seen the thread below regarding nexus 9k tacacs with ISE?
hth
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2020 04:29 AM
Hi,
thank you for additional info. I will check it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2020 08:40 AM
When you look at the compatibility matrix, you have to keep in mind that it is referring to the other services beyond TACACS+, such as 802.1x, Posture, SGT, etc. TACACS+ with ISE should be supported by all Cisco devices that support TACACS+.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2020 10:44 PM
Hi,
I am not sure if I understand it correctly. Does it mean that Nexus line should be kompatibilite? As you know, I tried and it is not working. I am not able to authenticated on the switch.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2020 07:09 AM
= If we are using about TACACS-only for ISE-involvment , that should work as mentioned by other user. As far as the original error-code is concerned double check the shared secret and try for instance with a simple phrase to make sure that no obvious authentication error is the cause. If problem persists one may try another brand of TACACS server then ISE to check for compatibility. But that requires more elaborate testing and setups (indeed).
M.
-- ' 'Good body every evening' ' this sentence was once spotted on a logo at the entrance of a Weight Watchers Club !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2020 07:16 AM
That is correct! Any device, Cisco or third-party, that adheres to the TACACS+ protocol standards will work with ISE. The compatibility matrix for ISE addresses the non-TACACS+ features of ISE, such as 802.1x, URL Redirect, TrustSec, etc.
Double check your configuration on the switch. Specifically, check the shared secret that you have setup on the switch and in ISE for that device. I would recommend entering it again manually and do not copy/paste. Sometimes you can have an extra space when copying/pasting or it may look like it pasted fine but you actually pasted something different that was copied previously. Manually type it in on ISE and then use the show secret button to show what is actually there. Then manually type it into the Nexus.
I have integrated many Nexus switches with ISE for TACACS+ and it works just fine. The error you reference points to a mismatched shared secret.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2020 10:42 PM
Hello all,
I found out, that I made stupid mistake with the shared key. I did not realized, that if I wrote command:
tacacs-server host 10.52.188.50 key 7 "XXX" timeout 4
I just can not simply copy the text in " " because it is already hashed. So, then I wrote it as key 0, and I used exactly what I wrote in ISE conf.. Then then Nexus changed to key 7 (hashed key) automatically and I realized, that is still mix of characters, but it is little different, so it was hashed.
>>> Now is working.
I am really sorry that I bothered you with this question. I did not realized, that could be a issue, because I got this case after one experienced colleague who did not see it as a problem.
Thank you again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2020 02:29 PM
Is authentication not working? Or are you only seeing this in the reports? There is a recent bug filed for TACACS+ accounting packet issues:
https://quickview.cloudapps.cisco.com/quickview/bug/CSCvq23549
Only other thing I can think of is to double check your shared secrets.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



