- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE Machine Authentication Failure
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE Machine Authentication Failure
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 02:22 PM
We updated our ISE 2.4 instance to patch 12 over the weekend. After the update, ISE cannot properly authenticate machine accounts in AD. User accounts are unaffected.
Running the 'Test User Authentication' for a machine produces a failed result.
This was working before the patch update. The configuration hasn't changed.
We do have a case open with support but I'm curious if anyone has seen this before.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 02:27 PM
When are doing a test user are you doing the proper format:
host/<computername> or computername.mycompany.com$
If so what does ISE show when you run the test? Could be something got messed up if you were doing AD rewrites of some sort on the advanced screen. Also the details of the authentication record should should show any rewrites or what the exact identity ISE is trying to lookup in AD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 02:38 PM
Interesting results. I hadn't thought to test with host/name, only the fqdn.
host/name is successful while the fqdn fails.
There are no re-writes happening.
When it fails, it provides pretty generic output, no user found.
Test Username : host.domain.com
ISE NODE : <node>
Scope : <scope>
Instance : <domain>
Authentication Result : FAILED
Error : No such user, please refer to Test user option to get further information
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 02:51 PM
host.domain.com shouldn't work. That is not a proper computer account lookup. host.domain.com$ should work. Is this failing on Windows machines? The Windows supplicant passes the computer name in host/<computer name> format.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 03:08 PM
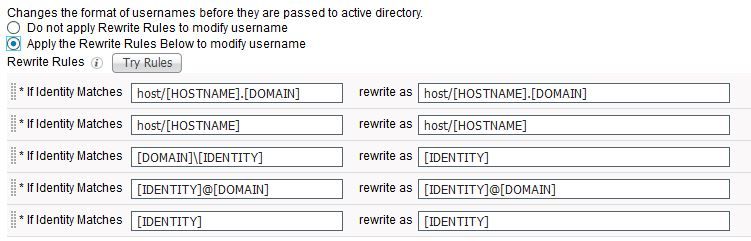
Just to show you what the acceptable formats are for AD lookup, you can look on the Advanced tab and enable rewrites to see the defaults:
[HOSTNAME].[DOMAIN] is not in the list. In my experience I have always had to add a rewrite rule for this:
if [HOSTNAME].[DOMAIN] rewrite as host/[HOSTNAME].[DOMAIN]
or
if [HOSTNAME].[DOMAIN] rewrite as host/[HOSTNAME]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 03:52 PM
After going through more logs, it looks like the username that's pulled from the endpoint is in the format host/fqdn. When I run the test on this naming format, it is successful.
The failure detail in ISE and the logs output to Splunk both show that format.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-12-2020 04:21 PM
When you run the tests you get to pick what ISE node to run it from. Make sure you test it from each PSN to ensure one of the PSNs is not having issues with AD authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2020 02:28 AM
In my environment I see that bevore patch 12 ISE look up machine in AD for authorization,
after patch 12 ISE look up user instead of machine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2020 08:43 AM
TAC provide me with this workaround: issue is due to bug CSCvr51940
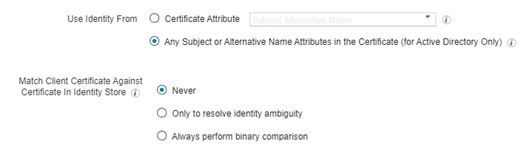
Or use this Certificate Authentication Profile settings:
I resolved my issue changing the cert.authen. profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2021 06:33 PM
The bug tool states this has been fixed. I am sorry to report that this has not been fixed in 3.7 patch 4. Our setup was configured using "Only resolve identity ambiguity" and tried chaining it to use "Always perform binary comparison". We also have the cert profile to use "Subject - Common Name". Once that change was done, the cert auth failed as it was looking for username@domain.com. We had to roll back and use "Only resolve identity ambiguity". Once that was done everything started working again. Our machine auth is looking for host/fqdn. Once changed to binary, it wants to look for username@domain.com.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2020 04:10 AM
If you are using certificate based machine authentication with binary comparison enabled under Certificate Authentication profile.
Attach the detailed failed authentication report for the failing machine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2020 03:06 PM
Hi,
I had the same issue also when upgraded from ISE 2.4 Patch 11 to Patch 12...Opened a case too, we tried everything including configuring rewrite rule but this didn't help. Had a support case opened and we fell back to patch 11...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2020 08:05 AM
Like @yasser.aljamil, TAC has asked me to try the work-arounds and rewrites mentioned in other posts. Nothing has worked to fix the issue. My guess is that we'll have to rollback the patch also. The case is being escalated now and I will update if there's a different outcome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2020 08:20 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2020 10:26 PM
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvu39890
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: