- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE Passive ID AD Requirements
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE Passive ID AD Requirements
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2017 09:26 AM
In the 2.1 beta I voiced my opinions on Passive ID and the lack of ease of integration with AD or the requirements to integrate with AD as opposed to other established products that do the same thing (ForeScout, OpenDNS, Palo Alto, etc.).
The process has been automated as long as the account used to join the ISE nodes to AD is a domain admin which of course is a non-starter for many customers. I believe the only reason the account needs to be a domain admin is so ISE can automatically run a script to configure the DCs for ISE integration.
Is this script made available to do this manually?
If you look at the Umbrella (OpenDNS) setup the integration is very simple.
- You download the script from the Umbrella dashboard.
- You run the script on each of the DCs.
- You create a service account whose only requirement is that it is a member of Event Log Readers, Distributed COM Users, Enterprise Read-only Domain Controllers.
Alternatively, I am testing out this method that seems to work:
- Create a service account and set the primary group to a Service Account AD group which has no rights on the domain
- Remove the service account from Domain Users.
- Add the service account to Event Log Readers AD Group.
- Add the service account temporarily to Domain Admins.
- Join ISE nodes to AD using the service account clicking the box to save credentials.
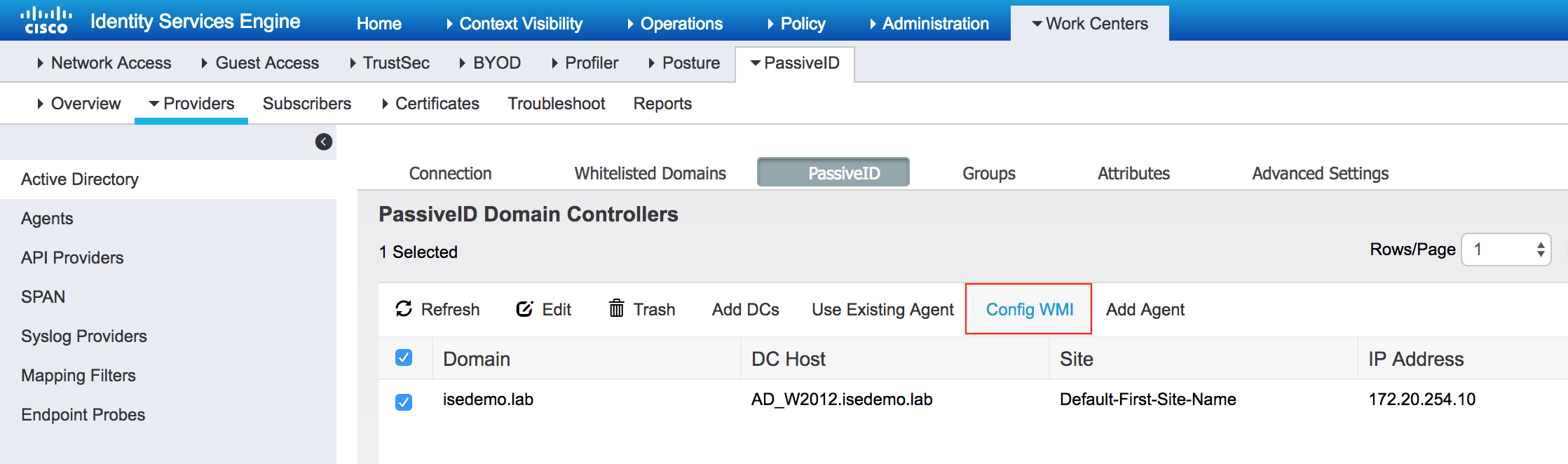
- Add each DC to the Passive ID screen and configure WMI on them.
- Remove service account from Domain Admins.
After Config WMI function has been run I don't think there is a need to be a member of Domain Admins. Is that true?
Thanks.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2017 10:07 AM
Hi Paul, I am not sure if you have got an opportunity to try this with ISE 2.2. We have automated the WMI configuration from ISE UI.
-Hari
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2017 10:12 AM
Hari,
That is what I am talking about. In order to do Config WMI you need to be a member of Domain Admins which is a problem. Are the steps at the bottom of my post acceptable to be able to utilize the Config WMI and remove the service account from Domain Admins when finised?
Paul Haferman
Office- 920.996.3011
Cell- 920.284.9250
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2017 11:33 AM
Hi Paul,
You need an admin account to config WMI on the DC (yes its one time), however there needs to be a service account that has adequate rights to pull the WMI logs, as and when end users do domain logins.
The other option we introduced in ISE 2.2 is to push an agent* from ISE, that runs as a trusted service on the DC. This too requires admin rights to install once, but no need for a service account to get login events.
(* WMI under the hood)
Hope this helps.
-Hari
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2017 12:15 PM
Hari,
Thanks for the response. After you run the WMI Config and remove the Domain Admin group from the service account is the only group it needs to be in is the Event Log Readers group?
Other solutions require membership in Distributed COM Users and Enterprise Read-only Domain Controllers but I think the Config WMI tasks make those groups unnecessary.
Paul Haferman
Office- 920.996.3011
Cell- 920.284.9250
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2017 04:06 PM
If you do not want to use AD domain admins, then the requirements of WMI providers for ISE passive ID remain the same as in CDA and ISE 2.1.
I believe you have a copy of my batch file(s) and helper binaries that used in the ISE Easy Connect lab exercise.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2018 02:43 AM
Hi Hari. We have a 2.3 ISE deployment, with Passive-ID enabled only on the PAN node, we cannot successfully integrate with AD. Username used is domain admin, i also did all the requirement settings from the 2.1 documentation on the AD side. Errors are as following:
If i do a test of the connection, the error is: "Exception when connecting to Isendity Mapping service to fetch DC connection status"
It i click on Configure, the error is: Unable to run executables on DC... The IseExec remote execution functionality failed to delete svc and cmd executables.
Can you please guide me?
Ionut
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2018 06:01 AM
This might help -- Configure WMI
If needed, please engage Cisco TAC to troubleshoot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2018 01:29 AM
I've seen the same thing.
Just confirming you have a standalone admin node, and another node with passive id persona?
If you try the 'download agent', do you get a blank page?
it seems the passive id persona is somehow still associated with the admin node, so any passive id interaction gets rejected (because the passive id personal isnt actually enabled!)
Fresh installs do not show this issue. I did wonder if enabling the passive id persona, then disabling it, might fix the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2018 01:44 AM
Hello Quentin,
I solved my problem somehow reading the Patch3 documentation, for the ver2.3 of ISE. Found a bug that's been fixed and looking at my logs which said constantly that PassiveID connector keeps starting and shutting down gave it a try. So problem was fixed after installing the update.
This is the bug:
CSCvh66228 The PassiveID probe connection drops and attempts to re-connect infinitely.
Give it a try!
Best of luck ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2017 05:34 AM
Good Morning Hariprasad, any chance you can share what "configure WMI" is doing under the covers? I am working with our Administrators to make the PassiveID connection but it keeps locking the account.
I know this is a vague question but the admin is asking me what ISE is trying to do. We are running version 2.2 connecting to a 2012 DC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2020 09:07 AM - edited 05-07-2020 08:13 AM
Adding my experience with a similar problem and frustration with vague responses from ISE. I'm adding this here as it's one of the top results when you search for my ISE error. Especially related to AD Requirements.
Environment:
2012 r2 and 2016 DC's
ISE v2.6.0.156 patch 3
Errors:
"Failed to run executable on <2016 DC FQDN>, Error: unknown root cause, iseExec execution failed."
At first I was able to 'Configure' and 'Test' the 2012R2 DC's but the WMI deployment would fail with the same error as the 2016's.
On the 2012r2 DC's i saw IDs 7045 and 7036 in Event Viewer that the iseExec service installed, started then stopped OK. But ISE would fail with the above error.
I opened a TAC case, was told to run through more manual pre-reqs from earlier versions of ISE. Before i did that, i tried one last thing.
All I did was reset the password for the service account I had created for this task with no special characters .
So, say the pw was: Example$P@55Word^Here
I changed it to: ExamplePa55WordHere
and everything started working. Hope this helps someone.
*EDIT: Apparently this stemmed from having a $ in the password and outlined in this bug https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvs14297
This has be resolved as of 2.6.0.156-Patch5, though i haven't personally tested it.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide