- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE Prime integration superuser admin
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 02:16 AM
Hi,
didn't find the answer anywhere so would like to ask if someone knows why the Prime needs a superuser admin for the integration. The Prime server should only read some data from ISE, so I thought a Read-only admin would be enough.
Many customers have problem to add the superuser rights to such a user so a good explanation would be great.
Thanks a lot.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2020 01:16 PM
Since ISE 2.0, the user could be one of the following ISE admin user roles:
SUPER_ADMIN,SYSTEM_ADMIN,MNT_ADMIN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 03:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 05:08 AM
Hi Marvin,
thanks for the reply. I am talking about the integration of Cisco ISE with the Prime infrastructure.
A local admin account in ISE is required and that admin has to be superuser. I do not understand why such privileges are needed.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 05:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 06:16 AM
Thanks Marvin, that's what I thought.
That's not good and I understand that the customers don't like it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2020 01:16 PM
Since ISE 2.0, the user could be one of the following ISE admin user roles:
SUPER_ADMIN,SYSTEM_ADMIN,MNT_ADMIN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2020 12:32 AM - edited 04-09-2020 12:37 AM
Hello @hslai ,
Cisco TAC says that it is not possible:
Please be advised that the credentials should be superuser credentials local to ISE. Otherwise, ISE integration does not work.
May you please give any screenshots to proof it works? We have a ssh issue connecting PI to ISE(the reason to ask TAC for help) and we can't test it ourselves.
Thanks a lot!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2020 09:57 AM
... We have a ssh issue connecting PI to ISE(the reason to ask TAC for help) and we can't test it ourselves....
PI does not connect to ISE via SSH AFAIK. Only Cisco DNA Center requires ssh to ISE.
Introduction to the Monitoring REST APIs is where we documented the admin role requirements due to CSCur87193, which is not customer visible due to lack of a release-note-enclosure. We were supposed to be documented in ISE compatibility matrix but somehow the info lost and our BE is not regularly testing ISE integration with PI.
IIRC we tested it successfully with ISE 2.0/2.1 and PI 3.1 in CY2016. As that is 4 years ago, the setup is no longer available.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2020 10:10 AM
@hslai Thank you for clarification! That's inspiring. Will post what we'll be able to do.
SSH - my fault, I meant TLS of course.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2020 04:56 AM
Hi hslai,
We made it work, thanks to you!
We have added ISE to PI using MnT Admin user role instead of Super Admin.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2020 06:13 AM
Have same question here.
Customer with highly secure environment doesn't want to allow any unnecessary superuser access to ISE . Especially since there is no explict documentation neither in ISE configuration guides or PI configuration guides...
Also there is no explanation, how does PI interacts with ISE - ports or protocols we should open on firewalls seems to be investigated by packet capture...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2020 06:29 AM
Ports and protocols I can answer - it is tcp/443 transporting TLS 1.2 (unless you have some really old unsupported releases in which case it's TLS 1.1).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2020 06:34 AM
Thanks a lot for that!
Is there any references in documentation? Unfortunately, we can't just refer to Cisco community, customer's security department need a proof for every ACL created...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2020 07:50 AM
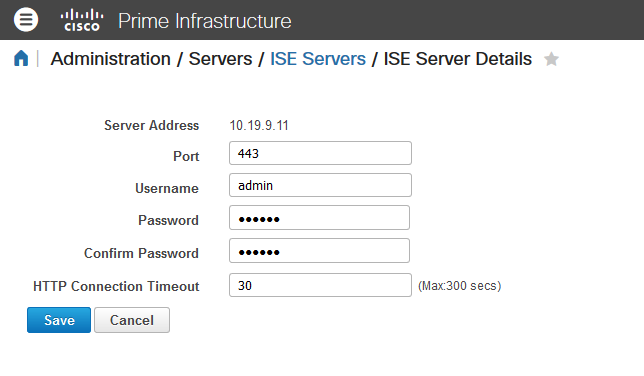
The ISE server is added from the PI side. When you do that, the port is shown in the GUI:
Additionally you can easily run tcpdump on the ISE node (Operations > Troubleshoot > Diagnostic Tools) and see the traffic. Packet capture doesn't lie, no matter what the guides show (or don't show).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2020 11:28 AM
Marvin, thank you very much!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: