- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE + Red Hat IdM (FreeIPA) for centralized authentication and TrustSec?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE + Red Hat IdM (FreeIPA) for centralized authentication and TrustSec?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2016 07:29 AM
I've started deploying Red Hat IdM to replace legacy NIS (YP) in my Linux environment. I would like to use the IdM LDAP server to authenticate users on Cisco ASA and Catalyst switches using either TACACS+ or RADIUS. Can ISE use Red Hat IdM as the external LDAP store? How would I go about configuring ISE External Identity Source to use the Red Hat IdM LDAP schema? Thanks.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2016 10:49 AM
I do not have personal experience with Redhat IdM so I would suggest you to confirm it with RedHat.
From my read of Identity Management or Red Hat Directory Server – Which One Should I Use? – Red Hat Enterprise Linux Blog, RedHat IdM appears to be the same as FreeIPA. About - FreeIPA shows it includes 389 Directory Server to provide LDAPv3 directory. As ISE supports LDAPv3, ISE should be able to work with the 389 DS there.
Configure the ISE for Integration with an LDAP Server - Cisco may help you to get started.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2016 12:47 PM
Hey Brian. I'm working on doing similar. I'm trying to get the Cisco ASA 5525 to authenticate against FreeIPA. I've managed to accomplish the authentication but have not been able to bind LDAP attributes effectively. So this enables any/all LDAP members to authenticate which is undesirable.
Have you had any further luck on your end?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2016 12:53 PM
Eric, I got ISE passing through a Catalyst 3750-X authentication to the Red Hat IDM / FreeIPA server; however, I've not gone any further. I also need to be able to restrict using LDAP attributes and haven't had the chance to flesh it out yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2016 01:03 PM
From the best I can tell the ASA on my end is not effectively querying the LDAP environment.
<code>
[-2147483623] Session Start
[-2147483623] New request Session, context 0x00002aaac56f0e20, reqType = Other
[-2147483623] Fiber started
[-2147483623] Creating LDAP context with uri=ldaps://1.1.1.1:636
[-2147483623] Connect to LDAP server: ldaps://1.1.1.1:636, status = Successful
[-2147483623] supportedLDAPVersion: value = 2
[-2147483623] supportedLDAPVersion: value = 3
[-2147483623] Binding as ldap_bind
[-2147483623] Performing Simple authentication for ldap_bind to
[-2147483623] LDAP Search:
Base DN = [dc=my, dc=com]
Filter = [uid=myuser]
Scope = [SUBTREE]
[-2147483623] User DN = [uid=myuser,cn=users,cn=compat,dc=my,dc=com]
[-2147483623] Talking to iPlanet server 1.1.1.1
[-2147483623] LDAP Search:
Base DN = [dc=my, dc=com]
Filter = [uid=myuser]
Scope = [SUBTREE]
[-2147483623] Retrieved User Attributes:
[-2147483623] cn: value = Eric Hart
[-2147483623] objectClass: value = posixAccount
[-2147483623] objectClass: value = ipaOverrideTarget
[-2147483623] objectClass: value = top
[-2147483623] loginShell: value = /bin/bash
[-2147483623] gidNumber: value = 777777
[-2147483623] gecos: value = Eric Hart
[-2147483623] uidNumber: value = 777777
[-2147483623] ipaAnchorUUID: value = :IPA:my.com:17e37436-17de-71e5-acc7-0021f7013089
[-2147483623] homeDirectory: value = /home/myuser
[-2147483623] uid: value = myuser
[-2147483623] Fiber exit Tx=336 bytes Rx=7681 bytes, status=1
[-2147483623] Session End
</code>
When I look at online examples of the type of return I should be expecting:
<code>
ciscoasa#debug ldap 255
debug ldap enabled at level 255
ciscoasa#
[105] Session Start
[105] New request Session, context 0xd5481808, reqType = 1
[105] Fiber started
[105] Creating LDAP context with uri=ldap://192.168.1.2:389
[105] Connect to LDAP server: ldap://192.168.1.2:389, status = Successful
[105] defaultNamingContext: value = DC=ftwsecurity,DC=cisco,DC=com
[105] supportedLDAPVersion: value = 3
[105] supportedLDAPVersion: value = 2
[105] supportedSASLMechanisms: value = GSSAPI
[105] supportedSASLMechanisms: value = GSS-SPNEGO
[105] supportedSASLMechanisms: value = EXTERNAL
[105] supportedSASLMechanisms: value = DIGEST-MD5
[105] Binding as administrator
[105] Performing Simple authentication for admin to 192.168.1.2
[105] LDAP Search:
Base DN = [dc=ftwsecurity, dc=cisco, dc=com]
Filter = [sAMAccountName=kate]
Scope = [SUBTREE]
[105] User DN = [CN=Kate Austen,CN=Users,DC=ftwsecurity,DC=cisco,DC=com]
[105] Talking to Active Directory server 192.168.1.2
[105] Reading password policy for kate, dn:CN=Kate Austen,CN=Users,
DC=ftwsecurity,DC=cisco,DC=com
[105] Read bad password count 0
[105] Binding as user
[105] Performing Simple authentication for kate to 192.168.1.2
[105] Checking password policy for user kate
[105] Binding as administrator
[105] Performing Simple authentication for admin to 192.168.1.2
[105] Authentication successful for kate to 192.168.1.2
[105] Retrieving user attributes from server 192.168.1.2
[105] Retrieved Attributes:
[105] objectClass: value = top
[105] objectClass: value = person
[105] objectClass: value = organizationalPerson
[105] objectClass: value = user
[105] cn: value = Kate Austen
[105] sn: value = Austen
[105] givenName: value = Kate
[105] distinguishedName: value = CN=Kate Austen,CN=Users,DC=ftwsecurity,
DC=cisco,DC=com
[105] instanceType: value = 4
[105] whenCreated: value = 20070815155224.0Z
[105] whenChanged: value = 20070815195813.0Z
[105] displayName: value = Kate Austen
[105] uSNCreated: value = 16430
[105] memberOf: value = CN=Castaways,CN=Users,DC=ftwsecurity,DC=cisco,DC=com
[105] mapped to IETF-Radius-Class: value = CN=Castaways,CN=Users,
DC=ftwsecurity,DC=cisco,DC=com
[105] memberOf: value = CN=Employees,CN=Users,DC=ftwsecurity,DC=cisco,DC=com
[105] mapped to IETF-Radius-Class: value = ExamplePolicy1
[105] uSNChanged: value = 20500
[105] name: value = Kate Austen
[105] objectGUID: value = ..z...yC.q0.....
[105] userAccountControl: value = 66048
[105] badPwdCount: value = 0
[105] codePage: value = 0
[105] countryCode: value = 0
[105] badPasswordTime: value = 128316837694687500
[105] lastLogoff: value = 0
[105] lastLogon: value = 128316837785000000
[105] pwdLastSet: value = 128316667442656250
[105] primaryGroupID: value = 513
[105] objectSid: value = ............Q..p..*.p?E.Z...
[105] accountExpires: value = 9223372036854775807
[105] logonCount: value = 0
[105] sAMAccountName: value = kate
[105] sAMAccountType: value = 805306368
[105] userPrincipalName: value = kate@ftwsecurity.cisco.com
[105] objectCategory: value = CN=Person,CN=Schema,CN=Configuration,
DC=ftwsecurity,DC=cisco,DC=com
[105] dSCorePropagationData: value = 20070815195237.0Z
[105] dSCorePropagationData: value = 20070815195237.0Z
[105] dSCorePropagationData: value = 20070815195237.0Z
[105] dSCorePropagationData: value = 16010108151056.0Z
[105] Fiber exit Tx=685 bytes Rx=2690 bytes, status=1
[105] Session End
</code>
Getting close, but not complete.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2016 11:39 AM
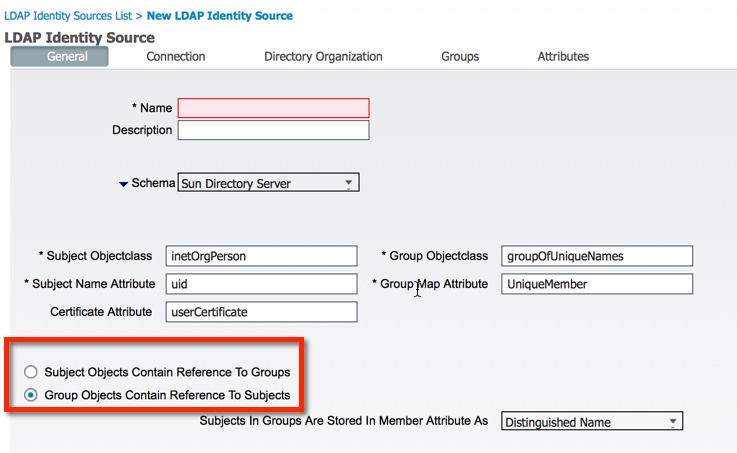
In Microsoft AD, user objects contain a reference to groups in memberOf attribute and groups have list of assigned users in member attribute.
The successful debug in your example shows the ASA retrieving the memberOf attribute and using LDAP maps to send the user to the specific group policy.
In debugs from the redhat server, i don't see any group attributes being retrieved. It's possible that in that system, only groups contain references to users. ASA does not support such layout. All LDAP decisions have to be based on what's retrieved on the user object.
ISE does support the ability to retrieve users belonging to a group even when those users don't attributes identifying which groups they belong to.
If you have the option of pointing ASA at ISE and then ISE at LDAP, you should be able to make it work.
This is the screenshot from ISE where this is configured:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2016 05:04 AM
Hey Viktor,
Thank you for the information. I found the issue with a little more digging. I inspected the Red Hat IdM LDAP structure and found that users do contain their memberOf relations within their branch so the ASA should be able to retrieve the users's group assignments. This led me to investigate what the ASA was managing to retrieve and led me to this string:
[-2147483623] User DN = [uid=myuser,cn=users,cn=compat,dc=my,dc=com]
So the ASA was being served a compatibility branch of the Red Hat IdM. While I haven't found a way to locally browse this compatibility branch, it's a safe bet it doesn't contain any memberOf information. From Red Hat IdM I disabled the compat module for a simple test and voila!
[-2147483619] User DN = [uid=myuser,cn=users,cn=accounts,dc=my,dc=com]
~
~
[-2147483619] Retrieved User Attributes:
[-2147483619] memberOf: value = cn=admins,cn=groups,cn=accounts,dc=my,dc=com
[-2147483619] mapped to Group-Policy: value = cn=admins,cn=groups,cn=accounts,dc=my,dc=com
So now I just need to work out the appropriate mappings.
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2016 09:51 AM
Gentlemen, were you able to succeed in this endeavor? I am battling with the Cisco ASA and FreeIPA as well.
I can get it to bind, but it is not finding my users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2016 09:58 AM
Hey Alexander,
My solution above worked going direct from the ASA to the IdM server, I do not have an ISE in my environment to test that. The ASA was able to identify authenticated user's group associations and they can be mapped to ASA group policy.
Hope that helps,
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-22-2016 06:14 AM
Any chance we could talk offline about this? I would like to get this done at my company. kgp@gasoc.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2018 06:37 AM
Hi Brian,
Do you have further insight and/or guidance into configuring IdM, ISE, and the Catalyst switch? Is ISE required to use IdM accounts on the switch?
Thanks,
Chris
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: