- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Need policy set of Cisco ISE CWA ISE 2.4
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2020 11:45 AM
Can anyone share me a screenshot of Wireless Authentication and Authorization policy set in ISE 2.4+ for a user to get Permit all, right after he enters username and password inside the CWA portal?
Lab minute CWA video policy doesn't work with ISE 2.4+ Radius username is not working unless I specify the name which is not practical.
Right now the user gets redirected to CWA portal there he enters username password of AD then CWA portal check with local AD once Auth success shows a new page says "you will get the Internet" but I am not getting internet since I don't have a policy set to give permitall please help me it is Urgent.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2020 02:57 PM
Ok let me share some screenshots.
I will use a user called testcwa member of WiFi AD group.
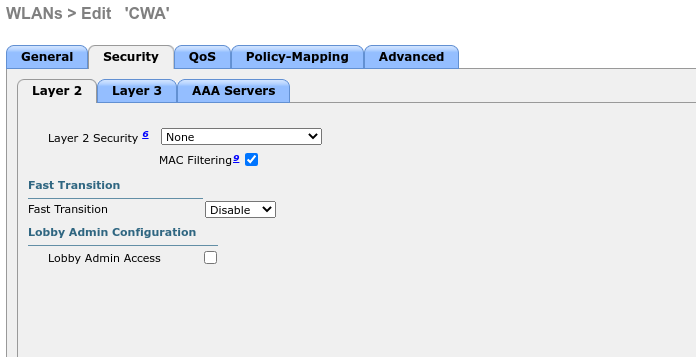
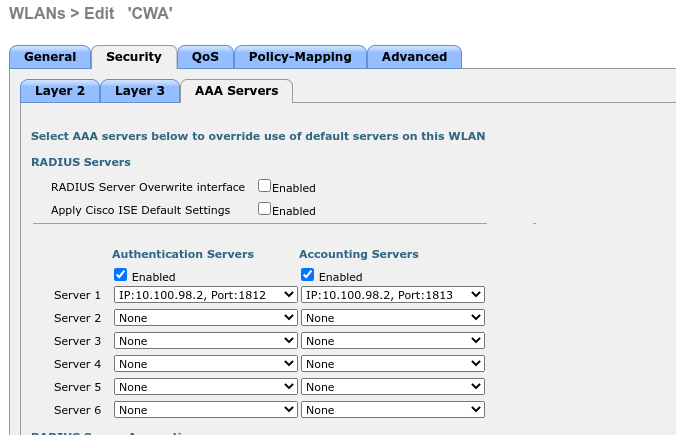
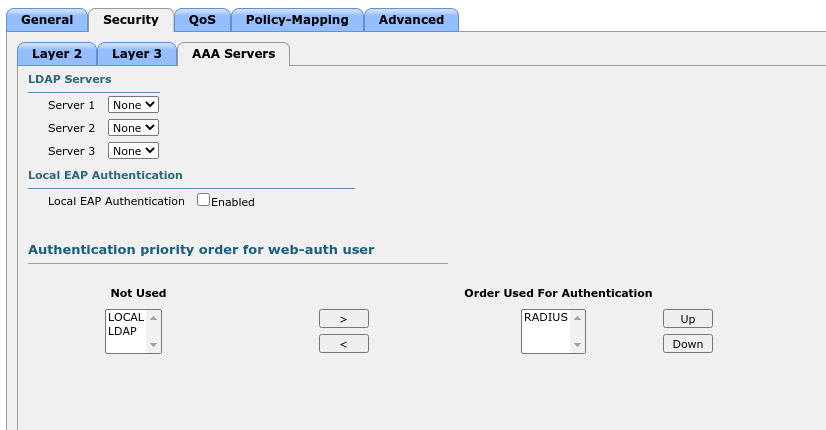
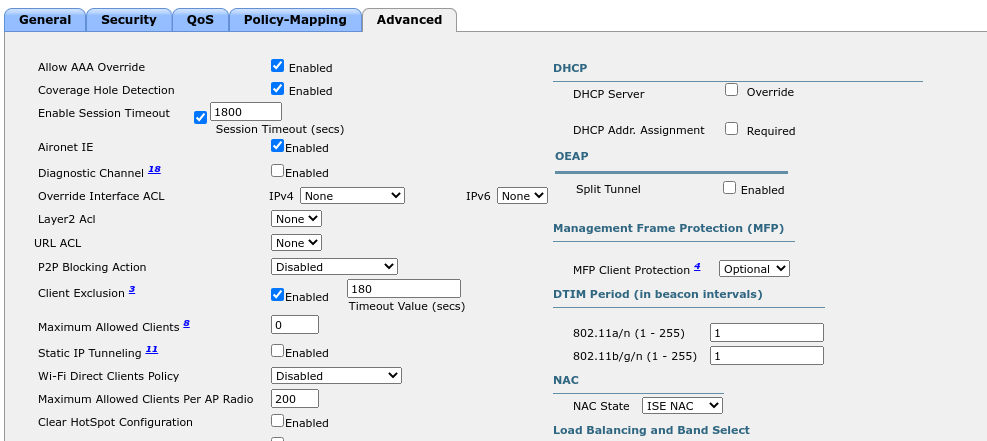
WLC SSID config:
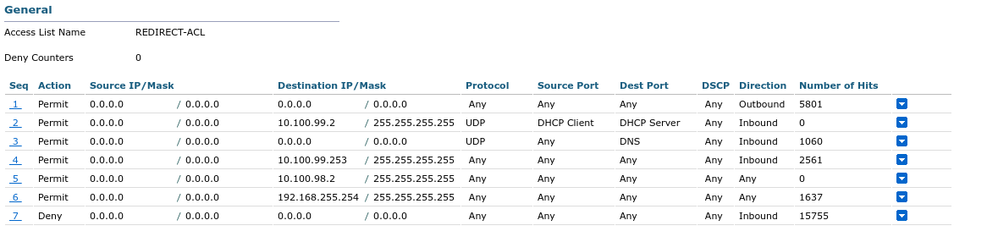
WLC ACL:
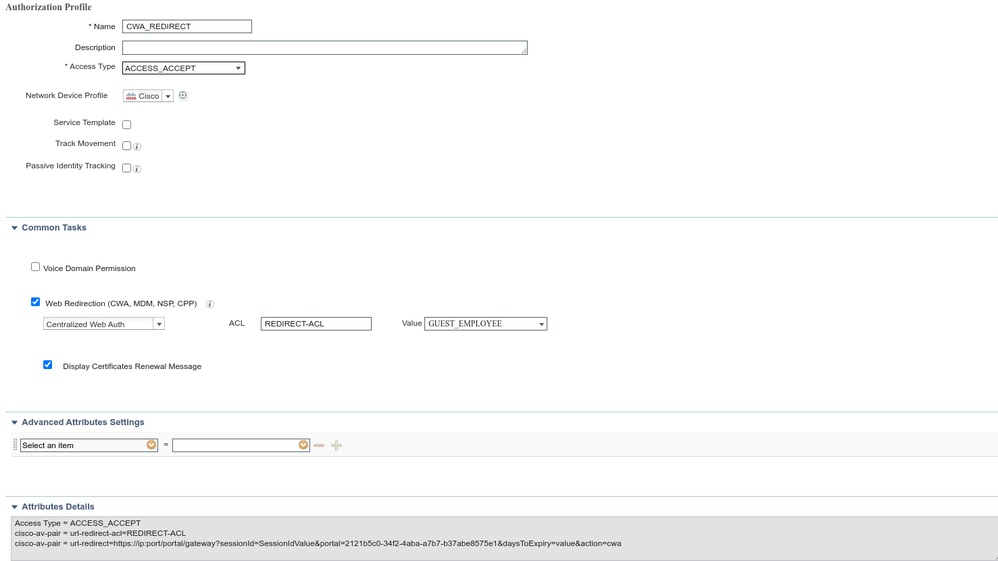
Cisco ISE Authorization Profile Redirect:
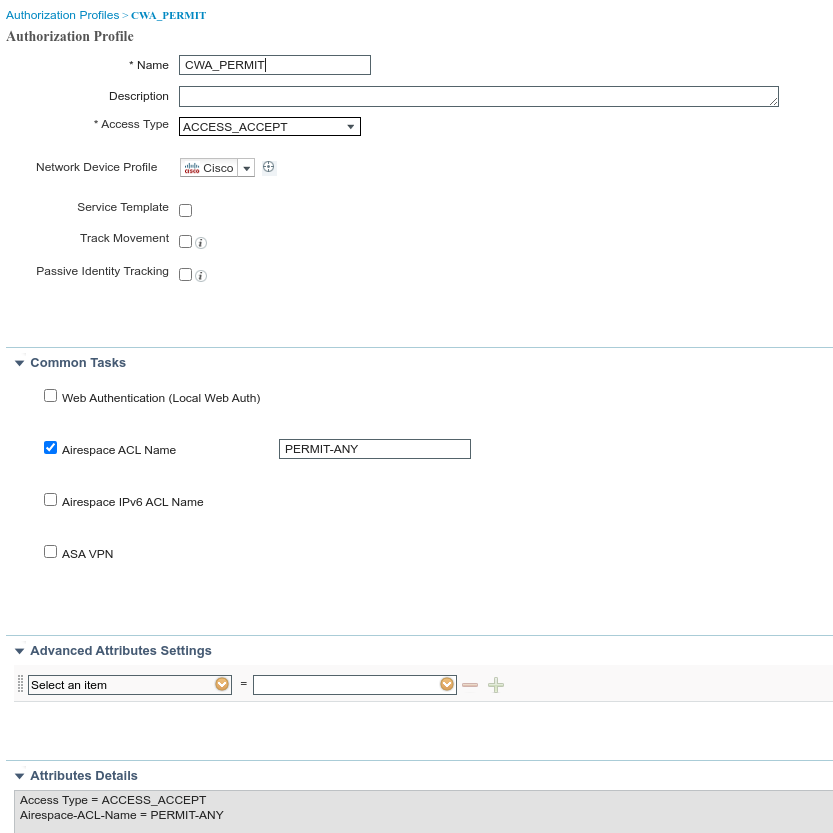
Cisco ISE Authorization Profile Permit:
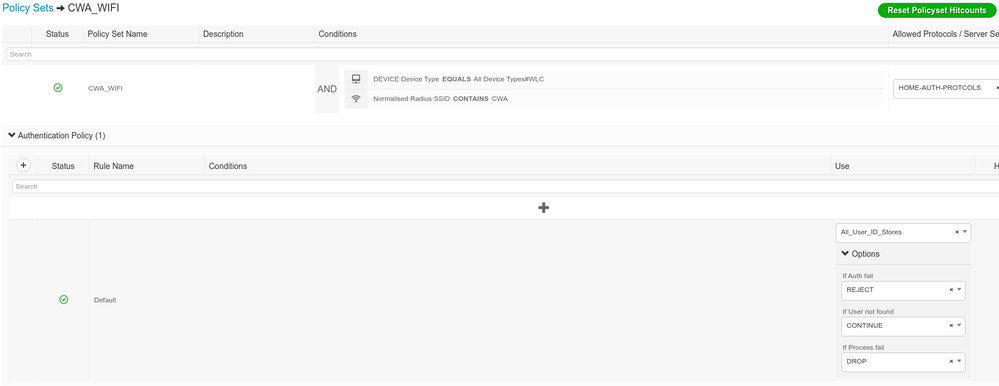
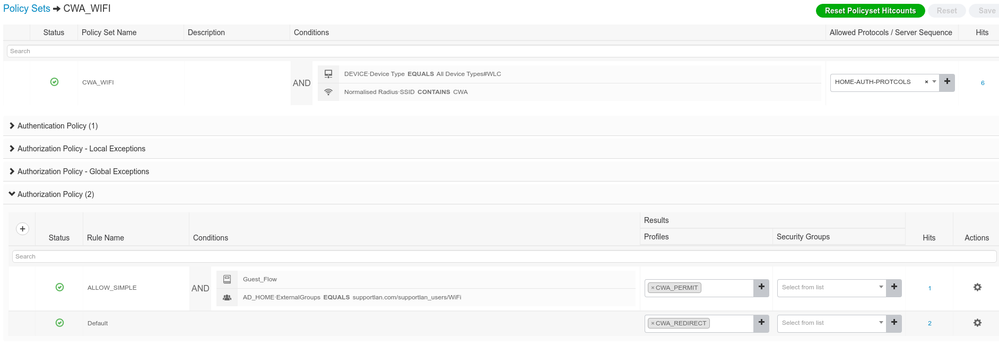
I have a dedicate Policy-set,
Cisco ISE Policy-Set:
Now, I connect to this SSID, my user authenticates and get internet access.
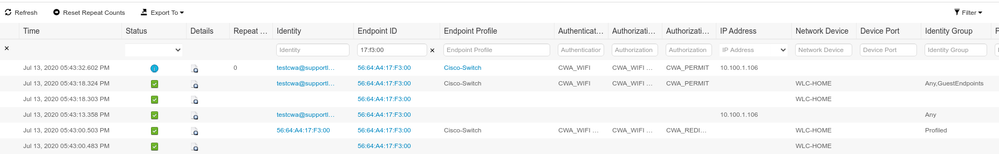
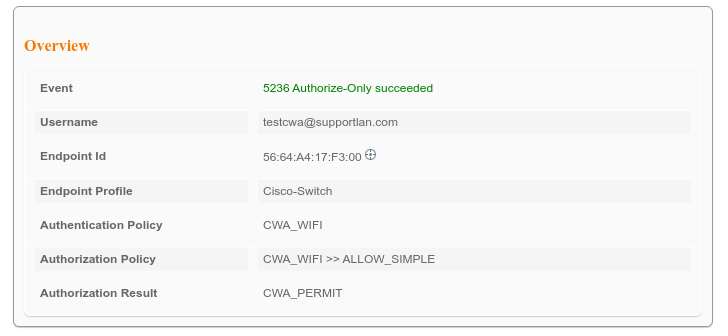
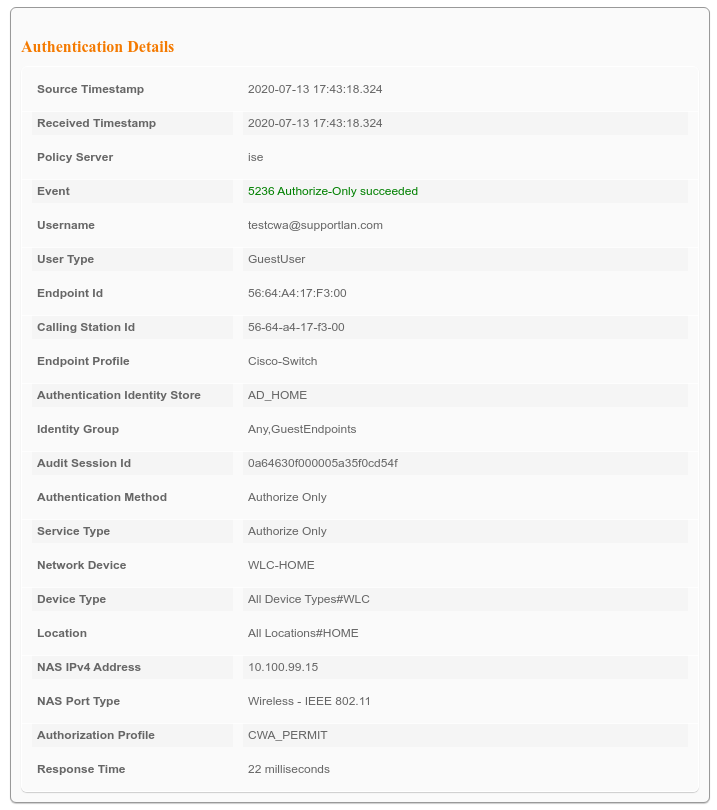
Below results from ISE:
Hope this helps.
Can you reproduce it in a very simple way like I did to make sure your Guest work and then you can start adding attributes to filter user authentication.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2020 08:10 PM
So you're able to authenticate your users over a CWA?
When they get authenticated, what authorization are you pushing?
Can you share your config to see what you're missing?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-02-2020 08:08 AM
Thank you, Francesco, Please check the attached screenshot of my current policy and guest portal details.
Right now redirection works and the user enters their username password in the CWA portal and Authentication is a success with AD also device is registered in the particular group as well. But after all these process users still, doesn't have a permit all access.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2020 11:43 PM
Is there any solution for this ?? It's been more than 4 days.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2020 10:51 AM
Can you share the authentication result please? I believe you have at least a condition not matching from your policies.
To validate this, you can create a simple authorization policy matching only your AD group and see if you get a permit result.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2020 01:11 AM
Thank you, Francesco, we all are busy with Job I do understand the pressure :)
I have tried with a simple AD group as well but it is still not hitting permit all policy.
Once the CWA portal comes and the user enters their user name and password in it then the user gets a prompt saying you have internet access now and then if I type anything in the web portal it took me back to redirect page again where it asks for the username & password it is like a loop.
Please check the attached screenshot of the live log and the policy set (I tried with web auth as well no output).
if possible please send me a screenshot of a policy that is normally used in a CWA method for Portal redirection and Permit all access.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2020 08:14 PM
Please review ISE Guest Access Prescriptive Deployment Guide if not already done and start with simpler authorization policy rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2020 04:58 AM
Hslai, I am able to get redirection which means my WLC, ACL, and ISE redirection policy is correct... Can you tell me where we are specifying Permit access ACL for the user after successful login in the CWA portal?
I tried a lot of policy set as above for permit all but none of them get a Hit.
In portals and components, I can only see Sucess Login: Original URL, no place where I can put a permit all setup.
Is CWA chaining only works with MAB?
Please reply if you have a solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-09-2020 04:22 PM - edited 07-11-2020 04:09 PM
We consider CWA Chaining different from CWA. I found you asked CWA Chaining with Intune earlier and Greg Gibbs provided you the info.
The condition example "CWA:CWA_ExternalGroups= Employee" works only with on-premise AD infrastructure at present. If your user already present there and in the proper AD group, then it's possible you are hitting a bug.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2020 05:27 PM
Have you tried to filter just using an ad group for example and attach a permit to it.
This will work for sure
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2020 11:33 PM
Francesco, I did try by putting a simple policy like external group > corp users>permit all.
No hit for this policy as well, can you share me a screenshot of policy set just to make sure I am doing the same?
Till this day almost 20+ policies are tried but nothing gets any Hit after user enter username and password in CWA portal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2020 02:57 PM
Ok let me share some screenshots.
I will use a user called testcwa member of WiFi AD group.
WLC SSID config:
WLC ACL:
Cisco ISE Authorization Profile Redirect:
Cisco ISE Authorization Profile Permit:
I have a dedicate Policy-set,
Cisco ISE Policy-Set:
Now, I connect to this SSID, my user authenticates and get internet access.
Below results from ISE:
Hope this helps.
Can you reproduce it in a very simple way like I did to make sure your Guest work and then you can start adding attributes to filter user authentication.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2020 03:46 AM
Thank you, Francesco, I did try the same but it didn't give permit access, Today I installed a new ISE with Latest patch and tried the same and it worked looks like some bug. Anyway, Thank you so much for helping me with this. Closing this discussion now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2020 06:53 PM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: