- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Problems with Identity PSK Manager and Assisted Onboarding
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2021 11:26 AM
Hi there,
I have been extensively testing the IPSK Manager tool and everything is working well except for the assisted onboarding captive portal feature. I am aware of bug CSCvs46399 and I am running ISE 2.6 Patch 8 (assuming the fix from Patch 7 is also included in Patch 8).
Here's the issue. I have two test clients, that are NOT defined/registered in the IPSK Manager database. I connect the clients to my IPSK wireless network using the default WPA2 passphrase, and that triggers the ISE authorization rule to redirect the client to the captive page. Both clients get a DHCP address, detect that a login is needed, and the browser opens up to try to load the page. The loading attempt times out.
In my ISE Authorization result for the redirect, I've tried using the URL of the IPSK manager and the IP address of the server to rule out a DNS issue. Both cases yield an unreachable captive portal page. Here is the authorization result that I have configured in ISE:
It appears that the clients are not even getting outside their local subnet. My clients can't even ping the gateway in this pre-captive-portal limbo stage, so it follows that they won't be able to reach the portal that is on a different network.
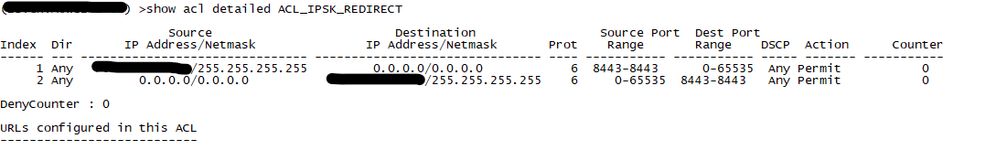
I don't know what is stopping the communication from a client in this stage. I configured the ACL on my 8510 WLCs according to the guide. The blacked out lines are the IPSK Manager's IP address in the ACL config below:
None of the counters have incremented, oddly enough, so I don't think it's the WLC that is stopping the traffic.
If the clients join a different Wi-Fi network (with standard internet access), they can reach the IPSK captive portal. Even if they join a non-ipsk WLAN that's handing out the same IPs that the IPSK wlan is handing out, the clients can reach the captive portal. The only time the captive portal is not reachable is when connecting to the IPSK wlan and going through the redirect.
Thanks,
David
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2021 01:00 PM - edited 02-09-2021 01:01 PM
David, I am not sure if the screenshot is cut off, but you are missing the AVP 'url-redirect-acl=ACL_NAME' which is needed along with 'url-redirect'. Also, when sending IPSK value, you also need to send the format AVP 'psk-mode=ascii'
I understand the table in the link above isn't that clear due to formatting, but you need both AVPs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2021 01:00 PM - edited 02-09-2021 01:01 PM
David, I am not sure if the screenshot is cut off, but you are missing the AVP 'url-redirect-acl=ACL_NAME' which is needed along with 'url-redirect'. Also, when sending IPSK value, you also need to send the format AVP 'psk-mode=ascii'
I understand the table in the link above isn't that clear due to formatting, but you need both AVPs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2021 01:25 PM
Howon,
Thanks so much for your quick attention to my post. I was stuck on this all morning. I found the setup guide a little bit unclear on this step which is why I missed the psk-mode and url-redirect-acl av-pairs. Now that I added these, the client is able to load the captive page.
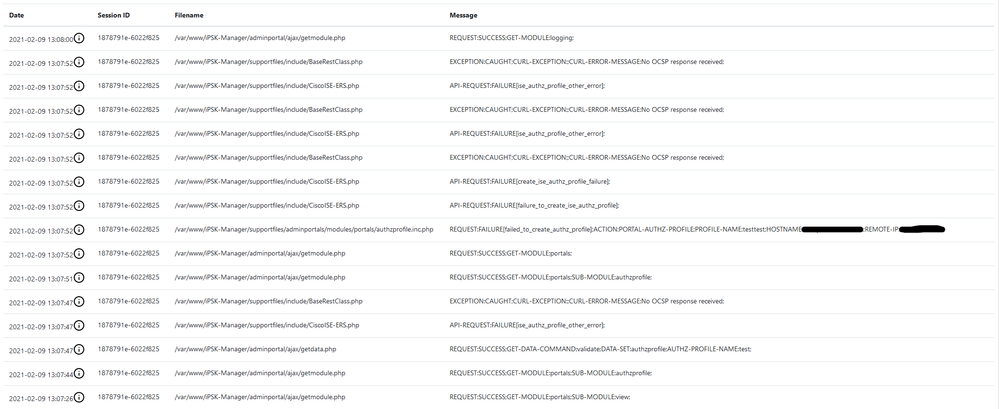
On a related note - I still can't get the IPSK Manager portal to create the ISE Authorization Profile. I am running ISE 2.6 Patch 8. In the IPSK Manager logs, I see the following after trying to "test" the authorization profile name and then click create:
Is there something I can look at that will give me more detail about the "failed_to_create_authz_profile" messages? Or do you have any suggestions about things to try?
Thanks again,
David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2021 06:55 AM
You will need to troubleshoot the ISE API calls. If it is not much trouble, I suggest manually creating the authz profile instead. This is just needed one time per portal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-10-2021 01:25 PM
Howon, thanks. It's no trouble at all to create it manually. At least the portal redirect is working now with 2.6 patch 8 unlike last year when I was trying it on an earlier patch and hitting the related bug.
On another related note - are pull requests welcome on the Github repo? I will be adding things to my personal deployment of the utility that I think would benefit the project - to start, I'll be adding some table interactivity (filter, search, etc) to the endpoint list, and also some additional interactivity to the captive portal registration process.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: