- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Remote Access VPN NAD IP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 08:18 AM - edited 02-02-2021 08:19 AM
Hi Experts,
We've RA VPN configured on ASA and forwarding the Authentication request to Radius server-ISE (DMZ). Instead of showing the IP address of ASA as the NAS device, it's showing me with the default gateway of the interface on ASA where are the ISE servers are residing behind.
Also, this IP is being added as the NAD device under Device groups. Any idea, why the default interface configured on ASA for DMZ zone is showing as the NAS device IPV4 address? Is this expected behavior?
Thanks in advance.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2021 01:21 PM
Take pcap captures of RADIUS exchanges among ISE, DMZ interface gateway IP and ASA. If the RADIUS packets show the gateway IP, then ASA is NAT by the gateway and correct it in the gateway as needed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 08:32 AM
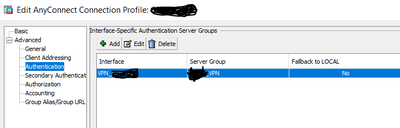
Have you attempted to add/test interface-specific aaa server group configuration within the respective tunnel-group under authentication? AFAIK this will use/change your sourced NAS/IP. See below:
I suggest testing via a test tunnel-group.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 08:48 AM
Hi Mike
Under the tunnel-group, authentication and accounting server group is configured as the PSN IP. But in the live logs, I see the NAS device IP as the interface IP and not of the ASA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2021 10:38 PM
The gateway might be doing NAT?!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2021 10:53 PM - edited 02-03-2021 11:19 PM
Hi @hslai
I've verified there is no NAT/PAT translating to the DMZ interface gateway IP.
As mentioned earlier, its being added as the NAD device as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2021 01:21 PM
Take pcap captures of RADIUS exchanges among ISE, DMZ interface gateway IP and ASA. If the RADIUS packets show the gateway IP, then ASA is NAT by the gateway and correct it in the gateway as needed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2021 09:49 PM - edited 02-04-2021 09:50 PM
Hi @hslai
I've generated Pcaps and noticed ASA uses default gateway IP of the interface when reaching the ISE for Radius Authorization and Accounting. Final one, Is it default behavior of the ASA to change its address while passing radius Authentication /Accounting info to ISE?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2021 10:04 PM
If your capture was done between ISE and the ASA's default gateway, then please also do it between ASA and the gateway. I still think it's the gateway somehow NAT the ASA RADIUS requests, but not ASA sourcing its RADIUS traffic using someone's IP address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 05:47 AM
Thanks for your assistance. I'm not able to see any Radius (UDP/1812 and 1813) between the ASA and the DG of the DMZ IP. But I do see the traffic traversing between the DG of DMZ and the ISE PSN (DMZ) which is Intrazone traffic and no NAT is also seen.
As you said, ASA doesn't source the IP address, let me take a look at the config. Thanks for the support mate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2021 04:39 AM
AFAIK this is normal behavior. The NAS device IP will depict the ASA sourced interface IP that is configured in screenshot I shared earlier.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2021 06:16 AM - edited 02-04-2021 06:17 AM
The aaa servers (ISE) are residing behind the DMZ interfaces and I don't see any interface is being specified in Tunnel-group under the 'Authentication' tab (as shared by you) and I didn't try changing it as it's a Prod network. I'm wondering how ISE sees the NAS device IP as the DG of that interface rather marking the ASA IP.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide