- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: VPN ISE - corporate devices
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN ISE - corporate devices
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2017 06:31 PM
Hi,
Is there a way to differentiate corporate assets (joined to domain, or certificate) on the VPN (ASA+ISE posture).
I have seen alot of people ask this question but no real answers.
The idea is that I want to allow specific access when AD users are on their corporate laptops vs on their personal devices.
thanks
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2017 07:44 PM
You can check a certificate on the attaching devices with the ASA. I would setup a group URL for each type of connection:
www.mycompany.com/employee (Tunnel Group Name- Employee)
- Cert + AAA
- Check for Computer Cert
- In order to check for computer cert you need to have the XML file rolled out ahead of time otherwise AnyConnect can't use the computer certificate.
www.mycompany.com/employeebyod (Tunnel Group Name- Employee_BYOD)
- AAA only
In ISE you can setup policy sets based on the Tunnel group name (VPN 3000 Tunnel Group Name attribute). The Employee Policy Set would control access from corporate assets and check AD groups as appropriate. The Employee_BYOD Policy Set would control access from non-corporate assets and check AD groups as appropriate. Push DACLs to control access.
I usually don't allow VPN access for employees from non-corporate assets but that is how I would look to handle it. It is very similar to how I handle Employees vs. Vendor connections.
None of this requires posturing and only consumes a base license in ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2017 05:14 AM
Thank you for your reply.
That seems quite a manual process when there are more then 100k devices.
Its a pity that with such an expensive solution we can’t do something as simple as certificate check, the thing can check if your USB is attached but nothing useful like cert or domain join.
Sent from my iPhone
On Jul 19, 2017, at 10:45 PM,paul@berbee <community@cisco.com<mailto:community@cisco.com>> wrote
Cisco Communities <https://communities.cisco.com/>
VPN ISE - corporate devices
reply from paul@berbee<https://communities.cisco.com/people/paul%40berbee> in Technology > Security > Policy and Access > Identity Services Engine (ISE) - View the full discussion<https://communities.cisco.com/message/263234#263234>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2017 05:23 AM
Well if you want to do posturing you can do any checks you want. I prefer to keep it simple. If the only requirement is to check corporate owned vs. BYOD that is easy to do with cert check on the ASA. If you go the full posturing route and want to consume APEX licenses, then check for registry settings to ensure it is domain joined computer.
Group URLs are very simple to implement which is why I usually go that route and avoid consuming APEX license just to answer the corporate vs. BYOD question.
Paul Haferman
Office- 920.996.3011
Cell- 920.284.9250
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2017 06:05 AM
I agree on the license part, tunnel group is complex to implement, the difficult part is distributing the xml file to users.
We have people that never come to the office so if we roll that out they'd basically never be able to get onto the network to actually receive the xml file if we were to distribute it via GPO.
Im going to check what I need to do in order to find the registry key that indicates that PC is joined to the domain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2017 06:59 AM
You could also do a User cert check as well that wouldn’t require you to do an XML file ahead of time. You just need to make the assumption that the only way a user cert would get on the device is through autoenrollment.
Paul Haferman
Office- 920.996.3011
Cell- 920.284.9250
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2017 04:46 PM
You could deploy the xml file from the ASA. If there is already an xml file on the remote devices they could login using regular credentials to the “legacy” url. That url could authenticate them, push the new xml file and present a post login message saying “log back in using the “corporate certificate vpn server.” Another thing you could do is have the users redirected to a custom portal in ISE that gives them the same instructions.
George
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2017 04:53 PM
I was able to identify a corporate asset using full posture by looking up if:
registry:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Domain
Value=your.domain.name is your.domain.name
Here is the registry created once you join the PC to the domain
***IM not sure why the regedit pic is not being copied over***

It works pretty well on win7 and win10 (I have to try to join win10 to the domain)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
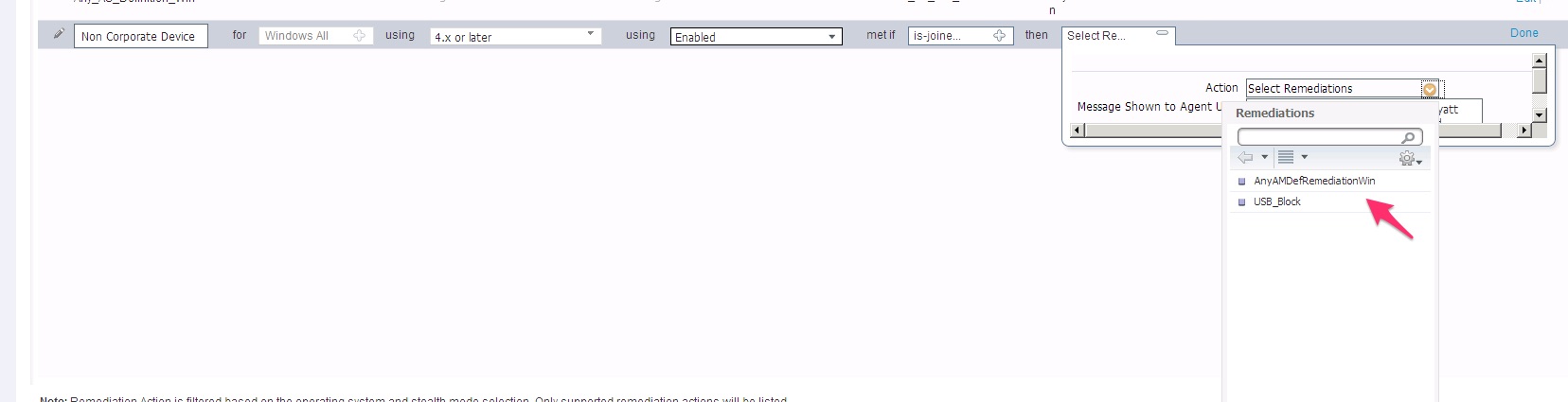
07-21-2017 07:06 AM
Now if I could only remove the remediation message.
I tried the stealth mode but once I enable the stealth mode (under posture requirements) - the only remediation actions are "usb lock and xxx"
Any ideas?

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2017 01:38 PM
Try posting a separate question about the remediation message in the AnyConnect community.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2017 11:07 AM
Any responses to this? I am having the same EXACT issue. I am posturing based on registry, but the remediation popup is super misleading. Stealth mode breaks it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2017 11:32 AM
You have the action on the requirement set to message text only?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2017 11:40 AM
Yes, it is set to "message text only". The remediation timer still pops up, and includes the text I configured in the "message text only" section.
That timer and popup confuses users.
I have setup the profile the stealth mode, but as Edon suggested, this doesn't work for file or registry remediation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2017 11:48 AM
I haven’t played around with stealth mode much, but the remediation timer makes sense even for message text stuff. Say it is something that the user could fix. Like when I am demoing Posture I will use something that is easy to fix/break like running notepad.exe. When they aren’t running Notepad.exe the pop-up comes up that says “You must be running Notepad to be compliant, please start Notepad to continue.” If the users bring up Notepad and clicks start before the remediation timer is finished they will be reported as compliant.
Now I know in this case the user can’t fix the problem, but you could change the message to say “Your machine does not meet the requirements to be on VPN. Please contact the help desk at (xxx) xxx-xxxx for further troubleshooting. You VPN session will be terminated in 5 minutes.” (or whatever the remediation timer is).
The device is not supposed to be on VPN and you told them to call the help desk. What more do you need to do?
Paul Haferman
Office- 920.996.3011
Cell- 920.284.9250
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2017 11:46 AM
I wasnt able to find a solution to this. I opted doing profiling based on AD probe. It is the easiest. For macOS I ended up integrating MDM Airwatch.
Sent from my iPhone
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: