- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: VPN ISE - corporate devices
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VPN ISE - corporate devices
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2017 06:31 PM
Hi,
Is there a way to differentiate corporate assets (joined to domain, or certificate) on the VPN (ASA+ISE posture).
I have seen alot of people ask this question but no real answers.
The idea is that I want to allow specific access when AD users are on their corporate laptops vs on their personal devices.
thanks
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2017 11:54 AM
Edon, when you have a chance, can you elaborate on what those technologies mean?
Thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2017 12:18 PM
To identify corporate assets I used AD probe, here is a link from Katherine: http://www.network-node.com/blog/2017/2/19/17-the-active-directory-probe she has some great material there. This only works for windows, for macOS my company uses Airwatch to manage macOS, so I integrated that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2017 01:39 PM
Could you show a screenshot of the AuthZ policy?
This is what I currently have:
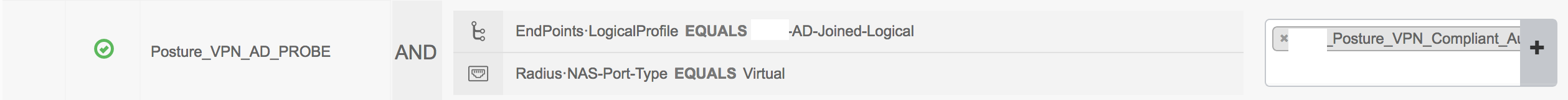
I'm guessing I'll need another line that is like... Endpoints:LogicalProfile NOT-EQUALS to AD-Joined-Logical, that sends non-company machines to a different profile.
I'm guessing I'll also need to add some logic so MAC's get excluded from this.
Any good links or explanations on how the MDM works???
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2017 01:57 PM
First off, your company would need to have some kind of MDM. here's a link for an example, she has a bit more on it, like BYOD and stuff. I've created a policy where it only checks if the device is in MDM (mobile device management - but we manage our MAC devices with it too) Example is Airwatch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2017 06:35 PM
We use JAMF for the MAC side management. I'd be interested in to see how you integrated ISE with your MDM to check it's device inventory.
Did you have separate AuthZ policies for Windows and MAC?
The way I envision it is something like....
---------------------------------
OS=Windows
AND
Endpoints:LogicalProfile EQUALS to AD-Joined
Then assign a compliant profile.
---------------------------------
---------------------------------
OS=Windows
AND
Endpoints:LogicalProfile NOT-EQUALS to AD-Joined
Then assign a non-compliant profile.
---------------------------------
---------------------------------
OS=MAC
AND
Exists-in-MDM = TRUE
Then assign a compliant profile.
---------------------------------
---------------------------------
OS=MAC
AND
Exists-in-MDM NOT-EQUALS TRUE
Then assign a non-compliant profile.
---------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2017 06:45 PM
Yes, but could be done more simple:
Endpoints:LogicalProfile EQUALS to AD-Joined = compliant-windows (macOS wont match this policy)
Exists-in-MDM = TRUE = compliant MAC (windows wont match this policy)
all else = non-compliant profile
Looks like JAMF is supported by ISE: https://www.cisco.com/c/m/en_us/products/security/technical-alliance-partners.html the way it works is that ISE accesses the MDM api, here's a thread: https://www.jamf.com/jamf-nation/discussions/22145/cisco-ise-2-1-integration LEt me know once you get api access (create a local account on JAMF that has API access), then add it from Administration - network resources - external MDM
- « Previous
-
- 1
- 2
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: