- Cisco Community
- Technology and Support
- Networking
- Network Management
- Re: Firewall config sanity check? Issue with Internet based Security A
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Firewall config sanity check? Issue with Internet based Security Alarm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2021 08:57 PM
TLDR:
Kindly verify that based upon the shared config from our ASA 5506-X, and based upon documentation for our "FlexIP" security alarm, that our firewall is not blocking traffic from
the alarm system, and causing it to go haywire.
I'll post a copy of the config and a screenshot of the alarm's purported network specs in a post to follow this one.
The Longer:
Our issue is that every few days or so ,our "FlexIP" internet based alarm system, that our alarm company (Sonitrol) put in, stops communicating with what they call the "receiver".
(According to the documentation they provided, the FlexIP alarm communicates outbound, to a few public ip addresses, associated with their "receiver" system(s). And it does so on a few different UDP ports.)
The end result of our problem is that the alarm panel beeps incessantly, and we're unable to arm the security alarm as well. When it can no longer communicate.
Sonitrol has purportedly replaced the alarm panel and what not, but the problem still happens.
Sonitrol has also come out a few times and put the alarm panel on a cradle point for its Internet access, rather than use our Internet ( AT&T Fiber), and the alarm works fine. So they say that the problem is "something" on our end. And they're blaming our firewall.
However, the alarm *will* work on our Internet too. In fact, it's worked for 5+ days at a time. It's just that it suddenly stops working. For no known reason, and haven't been able to devise any pattern to when it will happen either.
In fact, every time Sonitrol has come back out to retrieve their cradle point, they put the alarm panel back on our network/Internet. And magically, the alarm panel works fine again for a while. I've found that if I disconnect the Ethernet cable from the alarm panel for 10-20 minutes, it'll start communicating again.
I've requested to be able to get with the people "above" the tech who gets sent out. Ones that actually manage the server(s) that is their "receiver" system, and I'm told that's not possible.
So again, kindly give me a sanity check here and at least help me verify what I'd say I'm 99.99% sure is true. And that is that it's *not* our firewall blocking the alarm panel from communicating with their "receiver". At least, based upon the documentation that I've been given.
config and documentation to follow.
Thanks!!
- Labels:
-
Network Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2021 09:05 PM
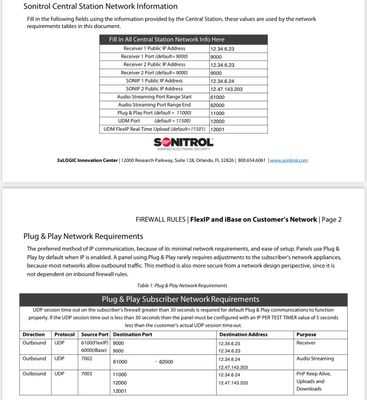
Ok...here's screenshots of the network requirements documentation they've given me. And the config of our firewall. With personally identifiable stuff redacted, of course.
One last note is that I believe based upon their documentation, our firewall was never blocking the traffic the alarm panel purportedly uses to begin with. However, since going back and forth with them, I created firewall rules that explicitly allows their required traffic to flow outbound. Even though that was redundant. It was to try to eliminate even the remote possibility it was the firewall blocking the traffic. Problem still persists though.
documentation of panel's network requirements
Our firewall's config
: Serial Number: XXXXXXX
: Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cor
:
ASA Version 9.14(2)
!
hostname FIREWALL
domain-name XXX.local
enable password ***** pbkdf2
service-module 1 keepalive-timeout 4
service-module 1 keepalive-counter 6
service-module sfr keepalive-timeout 4
service-module sfr keepalive-counter 6
names
mac-address auto prefix 56824
ip local pool SSLVPN_DHCP 10.11.11.2-10.11.11.100 mask 255.255.255.0
!
interface GigabitEthernet1/1
speed 1000
duplex full
nameif outside
security-level 0
ip address X.X.X.X 255.255.255.248
!
interface GigabitEthernet1/2
nameif backupisp
security-level 0
ip address X.X.X.X 255.255.255.248
!
interface GigabitEthernet1/3
nameif DMZ
security-level 75
ip address X.X.X.X 255.255.255.0
!
interface GigabitEthernet1/4
bridge-group 1
nameif inside_3
security-level 100
!
interface GigabitEthernet1/5
bridge-group 1
nameif inside_4
security-level 100
!
interface GigabitEthernet1/6
bridge-group 1
nameif inside_5
security-level 100
!
interface GigabitEthernet1/7
bridge-group 1
nameif inside_6
security-level 100
!
interface GigabitEthernet1/8
duplex full
bridge-group 1
nameif inside_7
security-level 100
!
interface GigabitEthernet1/8.12
vlan 12
nameif Internal_WIFI
security-level 100
ip address 172.16.16.1 255.255.255.0
!
interface GigabitEthernet1/8.13
vlan 13
nameif GuestWifi
security-level 50
ip address 172.17.17.1 255.255.255.0
!
interface GigabitEthernet1/8.14
shutdown
vlan 14
bridge-group 1
nameif Shop_Wired
security-level 100
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
interface BVI1
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
boot system disk0:/asa9-14-2-lfbff-k8.SPA
boot system disk0:/asa9-14-1-lfbff-k8.SPA
boot system disk0:/asa9-13-1-lfbff-k8.SPA
ftp mode passive
clock timezone EST -5
clock summer-time EDT recurring
dns server-group DefaultDNS
domain-name XXX.local
same-security-traffic permit inter-interface
object network obj_any1
subnet 0.0.0.0 0.0.0.0
object network obj_any2
subnet 0.0.0.0 0.0.0.0
object network obj_any3
subnet 0.0.0.0 0.0.0.0
object network obj_any4
subnet 0.0.0.0 0.0.0.0
object network obj_any5
subnet 0.0.0.0 0.0.0.0
object network obj_any6
subnet 0.0.0.0 0.0.0.0
object network obj_any7
subnet 0.0.0.0 0.0.0.0
object network NAT_INSIDE
subnet 0.0.0.0 0.0.0.0
object network MAILSERVER_INSIDE
host 192.168.0.14
description Private IP of MAILSERVEF
object network AppRiverNetwork1
subnet 5.152.185.128 255.255.255.192
object network AppRiverNetwork2
subnet 8.19.118.0 255.255.255.0
object network AppRiverNetwork3
subnet 8.31.233.0 255.255.255.0
object network AppRiverNetwork4
subnet 72.32.252.0 255.255.255.0
object network AppRiverNetwork5
subnet 74.205.4.0 255.255.255.0
object network AppRiverNetwork6
subnet 207.97.230.0 255.255.255.0
object network AppRiverNetwork7
subnet 207.97.242.0 255.255.255.0
object network AppRiverHost1
host 69.20.58.226
description server45.appriver.com
object network AppRiverHost2
host 69.20.68.133
description server55.appriver.com
object network AppRiverHost3
host 207.97.224.142
description server75.appriver.com
object network AppRiverHost4
host 207.97.229.125
description server101.appriver.com
object network AppRiverHost5
host 8.31.233.196
description server215.appriver.com
object network AppRiverHost6
host 92.52.89.74
description server305.appriver.com
object network AppRiverHost7
host 72.32.253.10
description server510.appriver.com
object network AppRiverHost8
host 72.32.252.97
description server520.appriver.com
object network AppRiverHost9
host 69.20.60.122
description Appriver Load Balancer
object network AppRiverHost10
host 69.20.58.234
description Appriver Backup Server
object network AppRiverLDAP1
subnet 67.192.226.128 255.255.255.192
object network AppRiverLdap2
subnet 174.143.49.64 255.255.255.192
object network MAILSERVER_SMTP_NAT
host 192.168.0.14
object network MAILSERVRT_HTTPS_NAT
host 192.168.0.14
object network DVR_NAT_OUTSIDE
host 172.18.18.254
object network DVR_INSIDE
host 172.18.18.254
object network Guest_Wifi_Outside
host X.X.X.X
description Guest_Wifi_Outside
object network NETWORK_OBJ_10.11.11.0_25
subnet 10.11.11.0 255.255.255.128
object network NETWORK_OBJ_192.168.0.0_24
subnet 192.168.0.0 255.255.255.0
object network REMOTESITE_Internal
subnet 10.199.4.0 255.255.255.0
description REMOTE SITE Internal Network
object network OpenDNS1
host 208.67.222.222
object network OpenDNS2
host 208.67.220.220
object service DVR_MOBILE_TCP
service tcp source eq 8000 destination eq 8000
description DVR HIK CONNECT MOBILE APP
object network DVR_HTTP_NAT
host 172.18.18.254
object service DVR_Mobile_UDP
service udp source eq 8000 destination eq 8000
object network SERVER_IDRAC
host 192.168.0.120
object network eth1.8
subnet 0.0.0.0 0.0.0.0
object network objany_7
subnet 0.0.0.0 0.0.0.0
object network shop_nat
subnet 0.0.0.0 0.0.0.0
object network SHOP_WIRED_NAT
subnet 192.168.0.0 255.255.255.0
object network obj_any6_backup_isp
subnet 0.0.0.0 0.0.0.0
object network Exchange_SMTP_BackupISP_NAT
host 192.168.0.14
object network EXHANGE_HTTPS_BACKUPISP_NAT
host 192.168.0.14
object network Shop_NAT
subnet 0.0.0.0 0.0.0.0
object network IT_TestServer
host 66.113.234.70
object network Shop_Sonitrol_Alarm
host 192.168.0.127
object network Sonitrol1
host 12.34.6.23
object network Sonitrol3
host 12.47.143.203
object network Sonitrol2
host 12.34.6.24
object service SonitrolUDP1
service udp destination eq 9000
object-group network AppRiver
network-object object AppRiverHost1
network-object object AppRiverHost10
network-object object AppRiverHost2
network-object object AppRiverHost3
network-object object AppRiverHost4
network-object object AppRiverHost5
network-object object AppRiverHost6
network-object object AppRiverHost7
network-object object AppRiverHost8
network-object object AppRiverHost9
network-object object AppRiverNetwork1
network-object object AppRiverNetwork2
network-object object AppRiverNetwork3
network-object object AppRiverNetwork4
network-object object AppRiverNetwork5
network-object object AppRiverNetwork6
network-object object AppRiverNetwork7
network-object object IT_TestServer
object-group protocol DM_INLINE_PROTOCOL_1
protocol-object ip
protocol-object udp
object-group network OpenDNS
network-object object OpenDNS1
network-object object OpenDNS2
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group service DVR_Mobile
service-object object DVR_MOBILE_TCP
service-object object DVR_Mobile_UDP
service-object tcp destination eq www
object-group network DM_INLINE_NETWORK_2
network-object object SERVER_IDRAC
network-object object SMSEXCH1_SMTP_NAT
object-group network Sonitrol_HQ
network-object object Sonitrol1
network-object object Sonitrol2
network-object object Sonitrol3
object-group protocol SonitrolUDPProGrp
protocol-object udp
access-list inside_access_in extended permit object-group DM_INLINE_PROTOCOL_1 o
access-list inside_access_in extended permit icmp any any
access-list inside_access_in extended permit ip any object-group OpenDNS
access-list inside_access_in extended deny object-group TCPUDP any any eq domain
access-list inside_access_in extended permit ip object REMOTESITE_Internal any
access-list inside_access_in extended permit icmp object REMOTESITE_Internal any
access-list inside_access_in extended permit tcp object-group DM_INLINE_NETWORK_
access-list inside_access_in extended deny ip host 192.168.0.6 host 192.168.0.1
access-list inside_access_in extended deny tcp any any eq smtp
access-list inside_access_in extended permit ip any any
access-list inside_access_in extended deny ip any6 any6 log
access-list outside_access_in extended permit icmp any any
access-list outside_access_in extended permit tcp any object MAILSERVRF_INSIDE eq
access-list outside_access_in extended permit tcp object-group AppRiver object S
access-list outside_access_in extended permit ip any object DVR_NAT_OUTSIDE
access-list outside_access_in extended permit icmp any object MAILSERVER_INSIDE lo
access-list inside_7_access_in extended permit icmp any any
access-list inside_7_access_in extended permit ip any any
access-list backupisp_access_in extended permit icmp any any
access-list backupisp_access_in extended permit tcp any object SMSEXCH1_INSIDE e
access-list backupisp_access_in extended permit tcp object-group AppRiver object
access-list SPLIT_TUNNEL standard permit 192.168.0.0 255.255.255.0
access-list SPLIT_TUNNEL standard permit 10.11.11.0 255.255.255.0
access-list outside_cryptomap extended permit ip object NETWORK_OBJ_192.168.0.0_
access-list DMZ_access_in extended permit object-group DVR_Mobile any any
access-list DMZ_access_in extended permit ip any any
pager lines 24
logging enable
logging trap informational
logging asdm debugging
logging host inside 192.168.0.119 17/51402
logging permit-hostdown
no logging message 106015
no logging message 313001
no logging message 313008
no logging message 106023
no logging message 710003
no logging message 106100
no logging message 302015
no logging message 302014
no logging message 302013
no logging message 302018
no logging message 302017
no logging message 302016
no logging message 302021
no logging message 302020
flow-export destination inside 192.168.0.198 2055
flow-export delay flow-create 15
mtu outside 1500
mtu backupisp 1500
mtu DMZ 1500
mtu inside_3 1500
mtu inside_4 1500
mtu inside_5 1500
mtu inside_6 1500
mtu inside_7 1500
mtu Internal_WIFI 1500
mtu GuestWifi 1500
mtu Shop_Wired 1500
no failover
no failover wait-disable
no monitor-interface Internal_WIFI
no monitor-interface GuestWifi
no monitor-interface Shop_Wired
no monitor-interface inside
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-openjre-7151.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (inside_6,any) source static NETWORK_OBJ_192.168.0.0_24 NETWORK_OBJ_192.168.-proxy-arp route-lookup
nat (any,outside) source static NETWORK_OBJ_192.168.0.0_24 NETWORK_OBJ_192.168.0ute-lookup
!
object network obj_any3
nat (inside_3,outside) dynamic interface
object network obj_any4
nat (inside_4,outside) dynamic interface
object network obj_any5
nat (inside_5,outside) dynamic interface
object network obj_any6
nat (inside_6,outside) dynamic interface
object network SMSEXCH1_SMTP_NAT
nat (inside_6,outside) static X.X.X.X service tcp smtp smtp
object network SMSEXCH1_HTTPS_NAT
nat (inside_6,outside) static X.X.X.X service tcp https https
object network DVR_NAT_OUTSIDE
nat (DMZ,outside) static X.X.X.X
object network obj_any6_backup_isp
nat (inside_6,backupisp) dynamic interface
object network Exchange_SMTP_BackupISP_NAT
nat (inside_6,backupisp) static X.X.X.X service tcp smtp smtp
object network EXHANGE_HTTPS_BACKUPISP_NAT
nat (inside_6,backupisp) static X.X.X.X service tcp https https
object network Shop_NAT
nat (inside_7,outside) dynamic interface
!
nat (Internal_WIFI,outside) after-auto source dynamic any interface
nat (GuestWifi,outside) after-auto source dynamic any Guest_Wifi_Outside
access-group outside_access_in in interface outside
access-group backupisp_access_in in interface backupisp
access-group DMZ_access_in in interface DMZ
access-group inside_access_in in interface inside
route outside 0.0.0.0 0.0.0.0 X.X.X.X 1 track 1
route backupisp 0.0.0.0 0.0.0.0 X.X.X.X
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
aaa-server SSLVPN protocol ldap
aaa-server SSLVPN (inside) host 192.168.0.11
timeout 30
ldap-base-dn dc=sms,dc=local
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn CN=ldapaccess,DC=xxx,DC=local
server-type auto-detect
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication telnet console LOCAL
aaa authentication login-history
http server enable
http 0.0.0.0 0.0.0.0 outside
http 192.168.0.0 255.255.255.0 inside_3
http 192.168.0.0 255.255.255.0 inside_6
http 192.168.0.0 255.255.255.0 inside_4
http 192.168.0.0 255.255.255.0 inside_5
http 0.0.0.0 0.0.0.0 backupisp
no snmp-server location
no snmp-server contact
sla monitor 10
type echo protocol ipIcmpEcho X.X.X.X interface outside
frequency 120
sla monitor schedule 10 life forever start-time now
service sw-reset-button
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto map outside_map 1 match address outside_cryptomap
crypto map outside_map 1 set peer X.X.X.X
crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5P-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 1 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map outside_map interface outside
crypto ca trustpoint ASDM_TrustPoint0
keypair ASDM_TrustPoint0
crl configure
crypto ca trustpoint ASDM_TrustPoint1
enrollment terminal
subject-name CN=vpn.XXXXX.com
keypair ASDM_TrustPoint0
crl configure
crypto ca trustpool policy
crypto ca certificate chain ASDM_TrustPoint0
certificate 00af511ad01d822fd1
3082068c 30820574 a0030201 02020900 af511ad0 1d822fd1 300d0609 2a864886
f70d0101 0b050030 81c6310b 30090603 55040613 02555331 10300e06 03550408
13074172 697a6f6e 61311330 11060355 0407130a 53636f74 74736461 6c653125
30230603 55040a13 1c537461 72666965 6c642054 6563686e 6f6c6f67 6965732c
20496e63 2e313330 31060355 040b132a 68747470 3a2f2f63 65727473 2e737461
72666965 6c647465 63682e63 6f6d2f72 65706f73 69746f72 792f3134 30320603
55040313 2b537461 72666965 6c642053 65637572 65204365 72746966 69636174
65204175 74686f72 69747920 2d204732 301e170d 31393034 32303138 33343133
5a170d32 30303631 39313532 3530305a 30483121 301f0603 55040b13 18446f6d
61696e20 436f6e74 726f6c20 56616c69 64617465 64312330 21060355 0403131a
76706e2e 73616665 7761796c 6f676973 74696373 75732e63 6f6d3082 0122300d
06092a86 4886f70d 01010105 00038201 0f003082 010a0282 010100b4 040624f7
7fed0707 8eb5210b 169f75e6 74f9a779 fc169533 54f0a6b8 bb2a5022 d86ee1e6
a4305ef4 e1a89309 44900743 21879afe 99260e96 a05233f5 8c645a14 1860f8a7
67ef4947 8d7b93f6 5d48367d cc3398da f0cbad50 d5f9f406 a465a097 0e9488c3
475aea65 de68d26f 97ea2242 1fe0073d b06b34b6 fe2e1bba c4574a9b 14eb0d73
ecb42108 f6e7e95b 39c202ba e81de6f7 4c8921cf 456d7904 3ac5522e 10deccdc
d935acba b87571f6 db489f62 753aef11 ae8f63a3 8e426b9a 743662fe ea94e9ce
8f2406e6 c3270265 2e78104e 57397281 fe6f62dc 78a18724 394305aa c874e7db
55d6ba49 266dcbbf 2ec45034 c765daaf 8734fc43 875a5069 23325302 03010001
a38202f8 308202f4 300c0603 551d1301 01ff0402 3000301d 0603551d 25041630
1406082b 06010505 07030106 082b0601 05050703 02300e06 03551d0f 0101ff04
04030205 a0303d06 03551d1f 04363034 3032a030 a02e862c 68747470 3a2f2f63
726c2e73 74617266 69656c64 74656368 2e636f6d 2f736669 67327331 2d313439
2e63726c 30630603 551d2004 5c305a30 4e060b60 86480186 fd6e0107 1701303f
303d0608 2b060105 05070201 16316874 74703a2f 2f636572 74696669 63617465
732e7374 61726669 656c6474 6563682e 636f6d2f 7265706f 7369746f 72792f30
08060667 810c0102 01308182 06082b06 01050507 01010476 3074302a 06082b06
01050507 3001861e 68747470 3a2f2f6f 6373702e 73746172 6669656c 64746563
682e636f 6d2f3046 06082b06 01050507 3002863a 68747470 3a2f2f63 65727469
66696361 7465732e 73746172 6669656c 64746563 682e636f 6d2f7265 706f7369
746f7279 2f736669 67322e63 7274301f 0603551d 23041830 16801425 45816850
26383d3b 2d2cbecd 6ad9b63d b3666330 45060355 1d11043e 303c821a 76706e2e
73616665 7761796c 6f676973 74696373 75732e63 6f6d821e 7777772e 76706e2e
73616665 7761796c 6f676973 74696373 75732e63 6f6d301d 0603551d 0e041604
14df2ade 3eb53d9a 93cd6c9a aab09be5 931f071c 51308201 03060a2b 06010401
d6790204 020481f4 0481f100 ef007600 a4b90990 b4185814 87bb13a2 cc67700a
3c359804 f91bdfb8 e377cd0e c80ddc10 0000016a 3c070859 00000403 00473045
022055bb 445e32b5 6b4cf93a 21537724 aba16d39 3b782c2c ca2d22e1 a653d50c
50c90221 00dcc15d 703f6b43 822566b5 d1eb6d36 e89dc844 360bd744 eba1dbdf
42f0b60d 57007500 5ea773f9 df56c0e7 b536487d d049e032 7a919a0c 84a11212
84187596 81714558 0000016a 3c070ce3 00000403 00463044 02201172 3c1c4adc
df46b073 e8da56de c358aa58 4fd79924 efe98fd1 d7d4e2f0 d86b0220 464dd12b
1d852426 da572814 351baaac 177a177d 1ed2ca51 51fcb518 2145a79e 300d0609
2a864886 f70d0101 0b050003 82010100 9eef1cde 16bb7285 515b7788 97c8b191
86619c28 755dea4a ef536198 2714f4fd 7a3e5a96 cb00ddf0 e15ed4f9 12f0a732
2614e606 16448322 1aa31e54 513f58bd 2cf8804e b94c5146 9443a169 aa0eb989
c7a89390 d2919065 844e9912 7c5d3592 48482ea5 80d3eef8 43de7f9c ef18daa0
87c694f0 37ba14b8 50cb9a2a 37bc0284 50ab68f4 b514d382 6bc414da 14308016
8269556b 349f34d7 6cf3206c d54c78e4 e44560c4 a2b08497 708ab730 8887856f
896fd490 f56dd924 2044a074 fe0b2559 d3f469af 40e250cc fcb3dd2d 260f6474
0876bf75 2c046d07 b68d3cdc 50bad94b ba5bf5ea b1a7904d d839ecbd c914aee3
492f38ae 75919bd7 63fb3ea0 10dfc0b9
quit
crypto ca certificate chain ASDM_TrustPoint1
certificate 6c40244ecbe64b46
3082068a 30820572 a0030201 0202086c 40244ecb e64b4630 0d06092a 864886f7
0d01010b 05003081 c6310b30 09060355 04061302 55533110 300e0603 55040813
07417269 7a6f6e61 31133011 06035504 07130a53 636f7474 7364616c 65312530
23060355 040a131c 53746172 6669656c 64205465 63686e6f 6c6f6769 65732c20
496e632e 31333031 06035504 0b132a68 7474703a 2f2f6365 7274732e 73746172
6669656c 64746563 682e636f 6d2f7265 706f7369 746f7279 2f313430 32060355
0403132b 53746172 6669656c 64205365 63757265 20436572 74696669 63617465
20417574 686f7269 7479202d 20473230 1e170d32 30303432 30313535 3432355a
170d3231 30363139 31353235 30305a30 48312130 1f060355 040b1318 446f6d61
696e2043 6f6e7472 6f6c2056 616c6964 61746564 31233021 06035504 03131a76
706e2e73 61666577 61796c6f 67697374 69637375 732e636f 6d308201 22300d06
092a8648 86f70d01 01010500 0382010f 00308201 0a028201 0100b404 0624f77f
ed07078e b5210b16 9f75e674 f9a779fc 16953354 f0a6b8bb 2a5022d8 6ee1e6a4
305ef4e1 a8930944 90074321 879afe99 260e96a0 5233f58c 645a1418 60f8a767
ef49478d 7b93f65d 48367dcc 3398daf0 cbad50d5 f9f406a4 65a0970e 9488c347
5aea65de 68d26f97 ea22421f e0073db0 6b34b6fe 2e1bbac4 574a9b14 eb0d73ec
b42108f6 e7e95b39 c202bae8 1de6f74c 8921cf45 6d79043a c5522e10 deccdcd9
35acbab8 7571f6db 489f6275 3aef11ae 8f63a38e 426b9a74 3662feea 94e9ce8f
2406e6c3 2702652e 78104e57 397281fe 6f62dc78 a1872439 4305aac8 74e7db55
d6ba4926 6dcbbf2e c45034c7 65daaf87 34fc4387 5a506923 32530203 010001a3
8202f730 8202f330 0c060355 1d130101 ff040230 00301d06 03551d25 04163014
06082b06 01050507 03010608 2b060105 05070302 300e0603 551d0f01 01ff0404
030205a0 303d0603 551d1f04 36303430 32a030a0 2e862c68 7474703a 2f2f6372
6c2e7374 61726669 656c6474 6563682e 636f6d2f 73666967 3273312d 3139362e
63726c30 63060355 1d20045c 305a304e 060b6086 480186fd 6e010717 01303f30
3d06082b 06010505 07020116 31687474 703a2f2f 63657274 69666963 61746573
2e737461 72666965 6c647465 63682e63 6f6d2f72 65706f73 69746f72 792f3008
06066781 0c010201 30818206 082b0601 05050701 01047630 74302a06 082b0601
05050730 01861e68 7474703a 2f2f6f63 73702e73 74617266 69656c64 74656368
2e636f6d 2f304606 082b0601 05050730 02863a68 7474703a 2f2f6365 72746966
69636174 65732e73 74617266 69656c64 74656368 2e636f6d 2f726570 6f736974
6f72792f 73666967 322e6372 74301f06 03551d23 04183016 80142545 81685026
383d3b2d 2cbecd6a d9b63db3 66633045 0603551d 11043e30 3c821a76 706e2e73
61666577 61796c6f 67697374 69637375 732e636f 6d821e77 77772e76 706e2e73
61666577 61796c6f 67697374 69637375 732e636f 6d301d06 03551d0e 04160414
df2ade3e b53d9a93 cd6c9aaa b09be593 1f071c51 30820102 060a2b06 010401d6
79020402 0481f304 81f000ee 007500a4 b90990b4 18581487 bb13a2cc 67700a3c
359804f9 1bdfb8e3 77cd0ec8 0ddc1000 00017198 4c5b6400 00040300 46304402
205f7389 2a75ea95 84bc9315 f1f12808 fcdeffa7 0615feb0 ab3c5351 808eca23
6e022021 7ebc2709 f6bdf4d8 781821c2 ab7223cf 0d3680a5 2f732b64 92cc9a0a
3dc62d00 75004494 652eb0ee ceafc440 07d8a8fe 28c0dae6 82bed8cb 31b53fd3
3396b5b6 81a80000 0171984c 5ce60000 04030046 30440220 67a82da8 83c3b9e6
49206c66 3372225a 44e386e6 8af7fcab 9b043f8a a415358f 02206f10 9d1504a9
e22c7eff b9a8112a 83d6f156 76f3b391 acf96459 8360b890 39e0300d 06092a86
4886f70d 01010b05 00038201 0100be89 e00e9522 1b49830f 61a90f23 5389ae8a
f82ad7c5 abcc983c fe5f5dad 3458e7ad a02cc77b d71741aa 595a3d37 7fae38b8
fca67a82 744d3adc d4f53617 de2db02d 199d21a4 2919d9bb 52fa6997 dec6cb93
8da7b2f3 240b620b e9d86ebf e87d3b13 f9172f35 97a0176e 41ad9f7f 4e106488
b8fcf3a4 3059bb9e 6ad9c6e1 59ca9161 95445546 549b13c6 6ff052ff 02fa5dd4
7ece0a89 17073260 ffac4034 6552f60a 34ee1bbb 24483b9d fe1959ca 105062a7
4c885832 11b74386 7b35cdc5 edde6799 82124708 3b38c34f feef9f28 f9a455cd
9d971f48 318a04f4 c64ccae2 e7d8c5bd 5e637932 01cdb482 031d4cb9 47e08e82
016c5baf c85a7fde 04c7cc8a 5c11
quit
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption aes-256
hash sha
group 14
lifetime 86400
crypto ikev1 policy 20
authentication rsa-sig
encryption aes-256
hash sha
group 14
lifetime 86400
crypto ikev1 policy 40
authentication pre-share
encryption aes-192
hash sha
group 14
lifetime 86400
crypto ikev1 policy 50
authentication rsa-sig
encryption aes-192
hash sha
group 14
lifetime 86400
crypto ikev1 policy 70
authentication pre-share
encryption aes
hash sha
group 14
lifetime 86400
crypto ikev1 policy 80
authentication rsa-sig
encryption aes
hash sha
group 14
lifetime 86400
crypto ikev1 policy 130
authentication pre-share
encryption des
hash sha
group 14
lifetime 86400
crypto ikev1 policy 140
authentication rsa-sig
encryption des
hash sha
group 14
lifetime 86400
!
track 1 rtr 10 reachability
telnet 192.168.0.11 255.255.255.255 inside_3
telnet timeout 5
ssh stricthostkeycheck
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group1-sha1
ssh 192.168.0.0 255.255.255.0 inside_3
ssh 192.168.0.0 255.255.255.0 inside_4
ssh 192.168.0.0 255.255.255.0 inside_5
ssh 192.168.0.0 255.255.255.0 inside_6
console timeout 0
dhcpd auto_config outside
!
dhcpd address 172.16.16.100-172.16.16.200 Internal_WIFI
dhcpd dns 192.168.0.11 interface Internal_WIFI
dhcpd wins 192.168.0.11 interface Internal_WIFI
dhcpd lease 28800 interface Internal_WIFI
dhcpd enable Internal_WIFI
!
dhcpd address 172.17.17.100-172.17.17.200 GuestWifi
dhcpd dns 208.67.220.220 208.67.222.222 interface GuestWifi
dhcpd lease 28800 interface GuestWifi
dhcpd domain XXXXGUEST.local interface GuestWifi
dhcpd enable GuestWifi
!
threat-detection basic-threat
threat-detection statistics
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 averag
ntp server 192.168.0.11 source inside prefer
ssl trust-point ASDM_TrustPoint1 outside
ssl trust-point ASDM_TrustPoint1 backupisp
ssl trust-point ASDM_TrustPoint1 DMZ
ssl trust-point ASDM_TrustPoint1 inside_3
ssl trust-point ASDM_TrustPoint1 inside_4
ssl trust-point ASDM_TrustPoint1 inside_5
ssl trust-point ASDM_TrustPoint1 inside_6
ssl trust-point ASDM_TrustPoint1 Internal_WIFI
ssl trust-point ASDM_TrustPoint1 GuestWifi
ssl trust-point ASDM_TrustPoint1 inside
webvpn
port 5000
enable outside
enable backupisp
dtls port 5000
http-headers
hsts-server
enable
max-age 31536000
include-sub-domains
no preload
hsts-client
enable
x-content-type-options
x-xss-protection
content-security-policy
anyconnect image disk0:/anyconnect-win-4.8.02042-webdeploy-k9.pkg 1
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy GroupPolicy_SSLVPN internal
group-policy GroupPolicy_SSLVPN attributes
wins-server value 192.168.0.2
dns-server value 192.168.0.11
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SPLIT_TUNNEL
default-domain value XXX.local
group-policy GroupPolicy_ X.X.X.X internal
group-policy GroupPolicy_ X.X.X.X attributes
vpn-tunnel-protocol ikev1 ikev2
dynamic-access-policy-record DfltAccessPolicy
username XXXX password ***** pbkdf2 privilege 15
tunnel-group SSLVPN type remote-access
tunnel-group SSLVPN general-attributes
address-pool SSLVPN_DHCP
authentication-server-group SSLVPN
default-group-policy GroupPolicy_SSLVPN
tunnel-group SSLVPN webvpn-attributes
group-alias SSLVPN enable
tunnel-group X.X.X.X type ipsec-l2l
tunnel-group X.X.X.X general-attributes
default-group-policy GroupPolicy_X.X.X.X
tunnel-group X.X.X.X ipsec-attributes
ikev1 pre-shared-key *****
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
!
class-map netflow-global-class
match any
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
description NETFlow Policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect rsh
inspect sqlnet
inspect netbios
inspect tftp
class netflow-global-class
flow-export event-type all destination 192.168.0.198
class class-default
user-statistics accounting
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
hpm topN enable
Cryptochecksum:7d9f91e5343f42f9418411f82eb979bd
: end
Thanks again!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2021 09:09 PM
Sorry...one last thing (which might be anecdotal)
The last thing is that even when the alarm panel is known to working and purportedly communicating with their "receiver" successfully, I do not see any outbound traffic coming from
the alarm panel, in the ASDM's real-time log.
I just find that strange because I would expect the alarm panel to be rather chatty. And there's nothing. My gut tells me that maybe the ASDM logging's just not super reliable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2021 12:00 PM
Did you ever sort this out? I am working with Sonitrol now, but with a Meraki firewall. Sonitrol does not speak networking 101 so it is very hard to understand how their equipment operates and what they need. I got the same guide you posted here and makes very little sense and no uses plug & play networking, etc. Same type of issues where sometimes it works and sometimes not, but they are not any help troubleshooting except telling me to open all kinds of ports which I have done.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2021 02:45 PM
Hello,
tough one. Can you find out what (and if at all) the Meraki firewall is blocking (anything) ? Meraki is mainly GUI based, but if you temporarily enable logging for all rules, that should show you if it blocks any Sonitrol related ports...
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: