- Cisco Community
- Technology and Support
- Networking
- Network Management
- LMS 3.2.1 cant see device in ciscoview
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
LMS 3.2.1 cant see device in ciscoview
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2012 12:01 AM
Hi Everyone,
I've a strange problem with LMS CiscoView I can't see ONE (its stack of two) device in the CiscoView.
and im getting an error mesg'
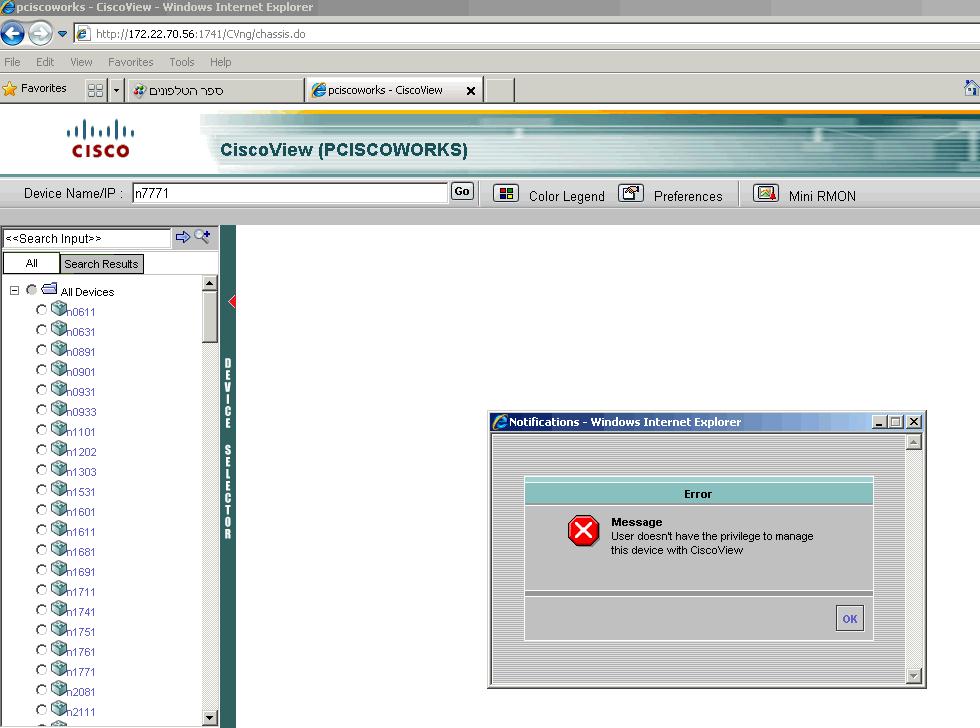
The LMS is connected to ACS and all the I.T Department can't see this specific device in CiscoView
I've tried:
- Deleted the device from the LMS and to discover it again.
- Rest the Demmon
- Erase it from the ACS and configure it again.
it didn't help.
I can use other functional things like back configuration
Details:
- LMS 3.2.1
- Cisco View 6.1.9
- Device Type - C3750V2-24PS
- ACS Version – 4.2
I'm attaching those files:
LMS Version
Show Version of the device
Windows systeminfo and version
error mesges
pdshow
Thanks for the help
- Labels:
-
Network Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2012 01:27 AM
Is LMS integrated with ACS or just for Authentication as PAM? What is the ACS version.
Share the output of NMSROOT/bin/ACSTestTool.pl from command prompt, if the LMS is integrated. Run it as :
NMSROOT/bin/perl NMSROOT/bin/ACSTestTool.pl
Please check if the user who is logged in is in admin group for LMS in ACS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2012 04:51 AM
Hi Vinod,
thanks for the replay,
the ACS version is 4.2, about how is the LMS integrated with the ACS where do I find it?
The user is in the admin group furthermore the I.T can see all the devices in the network expect this one.
I attaching the command output ACSTestTool.pl

thanks again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2012 09:05 AM
Hi
So if everything else from LMS's perspective is working as expected then the issue is most likely on ACS. Are you using Network Groups? The LMS server must be in the same group as the devices it monitors.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2012 03:44 AM
Hi Nqoldwat,
as i says in the Q. above,
we can see all the devices in the network in the CiscoView expect this device
the security team reconfigure the switch in the ACS and it didn't help.
how can I see if we are using a network group in the ACS, its belong to the security team can you please direct me to it,
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2012 01:55 PM
Hi
Please send the sysObjectID of the device.
You can retrieve this from the LMS server by running the command:
Solaris server:
$ /opt/CSCOpx/objects/jt/bin/snmpwalk -v2c -c
Windows server:
> /CSCOpx/objects/jt/bin/snmpwalk -v2c -c
One thing you could try is removing your LMS server from ACS integration and see if you can then manage the device.
Please send the sysObjectID of the device.
You can retrieve this from the LMS server by running the command:
Solaris server:
$ /opt/CSCOpx/objects/jt/bin/snmpwalk -v2c -c
Windows server:
> /CSCOpx/objects/jt/bin/snmpwalk -v2c -c
To address the ACS question:
Network Device Groups (NDGs) are collection of AAA clients such as servers and network devices. You should add the group of servers and network devices only under a NDG. You can use the existing NDGs or you can create a new NDG for this purpose. If you want to use an existing NDG, this step is optional.
--- Add CiscoWorks Server and Network Devices as AAA Clients
* You should configure the following as AAA Clients in ACS Server: *
** CiscoWorks Server
You should manually add the DCR Master server as an AAA client in ACS, before you change the mode to ACS. When you use CiscoWorks Assistant Server Setup workflow, the workflow converts the AAA mode of other servers in the multi-server setup to ACS mode.
** Devices managed by CiscoWorks Server
You should add the devices managed by CiscoWorks in ACS after you have configured the CiscoWorks Server as a AAA client. If you do not configure the devices as AAA clients in ACS, the devices will not be visible in CiscoWorks Server after the integration. If you use CiscoWorks Assistant Server Setup workflow to change the AAA mode to ACS, the missing devices are added to the NDG you specify.
One thing you could try is removing your LMS server from ACS integration and see if you can then manage the device.
Here is the link to Changing ACS Setup
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2012 02:47 AM
Hi Nqoldwat,
first thanks for the help,
I'm attaching the SNMPWLK output,

and here are some workaround that I did:
- I disable the connection between the ACS and CW and yes it help I can see the device.
- when I enable the connection again its back to the same error messages
- I checked with the security team the configuration of the device in the ACS and it's the same like every device
- Finley I restarted the device and the issue are the same we get the same error problem
please advice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2012 06:53 AM
OK so the device is a catalyst37xxStack (.1.3.6.1.4.1.9.1.516)
According to the Supported Device Table the minimum software requirements are 12.2(25)SEC[RME] & 12.2(20)SE3[CM]. However Remote Staging for this device is supported using external FTP server from RME 4.2 onwards. You must download and install the external FTP support patch available at: http://cisco.com/cgi-bin/tablebuild.pl/cw2000-rme
- rme4.2.0-sol-CSCsy338441.0.zip (on Solaris)
- rme4.2.0-win-CSCsy338441.0.zip (on Windows)
But you state that you can manage the device when not integrated with ACS. It does appear that the issue may reside on the ACS side of the house. Here are the instructions for integration. If followed exactly the process wiil be a success.
Before You Begin ACS Integration
Before you integrate the CiscoWorks Server with ACS, ensure that you:
1. Set up a System Identity User in CiscoWorks Server
You can either use the Common Services or the CiscoWorks Assistant Server Setup workflow to configure a System Identity User.
2. Assign all the local user privileges to System Identity User in CiscoWorks Server
You should add the System Identity User as a local user and assign all the privileges in CiscoWorks Server.
See the Setting up Local Users section in User Guide for CiscoWorks Common Services 3.2 to configure System Identity User configured as a local user and assign all privileges in CiscoWorks Server. If System Identity User is not configured with all local user privileges, authorization fails when you try perform certain tasks in CiscoWorks Server.
Setting Up ACS Server
You should perform the tasks in ACS before you change the AAA mode of CiscoWorks Server to ACS.
1. Configure ACS Administrators in ACS Server
You should configure the ACS administrators with all privileges in ACS. The ACS administrator account in ACS is required to:
* Access the ACS server from any remote machine.
* Enter the login details during the AAA mode setup in Common Services.
Only then does authentication occur from the ACS Server. Also, if you do not configure the ACS administrative user with all the privileges, the application registration with ACS will fail.
2. Create a Network Device Group
Network Device Groups (NDGs) are collection of AAA clients such as servers and network devices.
You should add the group of servers and network devices only under a NDG. You can use the existing NDGs or you can create a new NDG for this purpose.
If you want to use an existing NDG, this step is optional.
3. Add CiscoWorks Server and Network Devices as AAA Clients
You should configure the following as AAA Clients in ACS Server:
* CiscoWorks Server
You should manually add the DCR Master server as an AAA client in ACS, before you change the mode to ACS.
When you use CiscoWorks Assistant Server Setup workflow, the workflow converts the AAA mode of other servers in the multi-server setup to ACS mode.
* Devices managed by CiscoWorks Server
You should add the devices managed by CiscoWorks in ACS after you have configured the CiscoWorks Server as a AAA client.
If you do not configure the devices as AAA clients in ACS, the devices will not be visible in CiscoWorks Server after the integration.
If you use CiscoWorks Assistant Server Setup workflow to change the AAA mode to ACS, the missing devices are added to the NDG you specify.
4. Configure the CiscoWorks Administrative Users in ACS
You should add CiscoWorks System Identity User and other CiscoWorks administrators in ACS. Otherwise if you log in as a user configured only in Common Services, authentication will not happen.
You can create a user group in ACS and add all users to that user group.
See the following documents on Cisco.com for details how to perform each of the above tasks:
* User Guide for Cisco Secure Access Control Server 3.x and 4.x - http://www.cisco.com/en/US/products/sw/secursw/ps2086/products_user_guide_list.html
* User Guide for CiscoWorks Common Services 3.2 - http://www.cisco.com/en/US/products/sw/cscowork/ps3996/products_user_guide_list.html
* CiscoWorks LMS Integration with Cisco Secure ACS whitepaper - http://www.cisco.com/en/US/products/sw/cscowork/ps2425/prod_white_papers_list.html
Changing the AAA Mode to ACS Using the Server Setup Workflow
To change the mode to ACS:
Step 1 Select CiscoWorks Assistant > Workflows > Server Setup > Change ACS Setup.
CiscoWorks Assistant checks whether there are pending devices in DFM and RME. If CiscoWorks Assistant finds any pending devices, the Pending Device Count table is displayed with the following details:
* Server—Server name.
* Application—The application that contains pending devices. The values will be DFM or RME.
* Pending Count—Number of pending devices.
* Details—The reason why CiscoWorks Assistant could not fetch the pending device count. This column will be blank if the pending devices count is found.
Along with the table, a Notification pop up window appears with the following message:
Pending devices exist or could not check for pending devices in some LMS applications
Step 2 Click OK.
Step 3 Click Next.
A confirmation pop up appears with the following message:
LMS server(s) ACS configuration will not be proper if there are pending devices in the LMS applications. Make sure there are no pending devices and click OK to continue.
To get further details on pending devices in the applications, go to:
* RME > Devices > Device Management > Pending Devices
* Device Fault Manager > Device Management > Device Summary
See RME and Device Fault Manager User Guides for more information on pending devices.
Step 4 Click OK.
The Change ACS Setup page appears.
Step 5 Select the Change Mode to ACS check box and click Next to go the Configure ACS Mode page.
Note: Ensure that the local server is an AAA client to ACS server.
Step 6 Click OK on the Notification pop-up window to continue with the ACS Mode change.
Step 7 Enter the required information in the ACS Mode Setup table to change the login mode to ACS.
If the DCR Master (local server) is already in ACS mode, the fields other than the passwords and secret keys will be pre-populated.
Step 8 Select Register all installed applications with ACS, if you are registering the applications for the first time.
In case an application is already registered with ACS, the current registration will overwrite the previous registration.
When you select the Register all installed applications with ACS check box, you are prompted to confirm whether you want to continue with the settings.
See Common Services Online Help for details.
Step 9 Select the HTTP or HTTPS radio button under Current ACS Administrative Access Protocol.
Step 10 Click Next to complete the mode change.
The Configure ACS Mode Progress page is displayed. You can view the ACS mode configuration status in this page.
Note: Restart Daemon Manager after you configure ACS Mode for the changes to take effect.
Assigning Roles to Users and User Groups In ACS
After authentication, your authorization is based on the privileges that have been assigned to you. A privilege is a task or an operation defined within the application. The set of privileges assigned to you, defines your role.
You can either:
Assign predefined roles to CiscoWorks Users in ACS Or Create custom roles and assign them to CiscoWorks Users in ACS.
You ensure that the CiscoWorks user or the user group has been assigned the proper privileges in ACS mode. You can assign a desired role to the user or user group, or assign roles on an NDG basis.
See the following topics in User Guide for CiscoWorks Common Services 3.2 for more information:
* Roles in ACS
* Assigning Roles to Users and User Groups in ACS
Impact of Installing CiscoWorks Applications in ACS Mode
We recommend that you integrate CiscoWorks server and Cisco Secure ACS after installing all of the LAN Management Solution applications.
If you install any application on the CiscoWorks Server when AAA mode is set to ACS, you might be prompted with a message to re-register the application with ACS.
For example, if you have integrated CiscoWorks server and Cisco Secure ACS before installing any application, you are prompted with this message at the time of installation of the selected application:
CiscoWorks Server is in ACS mode
The application that you are installing requires new tasks to be registered with ACS. If you have already registered this application with ACS from another server, you do not need to register it again. However if you re-register the application, you will lose any custom roles that you had created earlier for this application in ACS.
Enter (Y)es to Register, (N)o to continue without registering,
(Q)uit: [N]
* If you enter Y, the application gets registered with ACS server.
* If you enter N, the application does not get registered with ACS server.
After installation, you can register RME 4.2 with ACS server, using the AcsRegCli.pl script:
/opt/CSCOpx/bin/perl /opt/CSCOpx/bin/AcsRegCli.pl -register rme
When you re-register, the custom roles you have created may be lost.
* If you have installed your application after configuring the CiscoWorks Login Module to ACS mode, the application users are not granted any permission.
However, the application is registered to the Cisco Secure ACS. On the Cisco Secure ACS server, you must assign the appropriate permissions to the application.
* Multiple instances of same application using same Cisco Secure ACS will share settings. Any changes will affect all instances of that application.
* If application is configured with Cisco Secure ACS and then the application is reinstalled, the application will inherit the old settings.
Verifying LMS Applications and the Cisco Secure ACS Configuration
After performing the above mentioned tasks on Cisco Secure ACS server, login to CiscoWorks with the username as defined in the Cisco Secure ACS.
Based on your privilege on the Cisco Secure ACS, you can perform only certain tasks on the CiscoWorks Server.
For example, if your privilege is of Help Desk, you can only view the Device Summary.
You can view only certain devices in the CiscoWorks Server. This depends on the Network Device setting for the User/Group on the Cisco Secure ACS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2012 01:44 AM
Hi Nqoldwat,
its the weekend so I can try it next week (you know indoor politics ),
but i took a wireshark output from the LMS server, I'd love more pair of eyes on the output
and hopelly to hear some insihgit
Those are the IP address:
LMS server - 172.22.70.56
device ip - 10.121.15.117
thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2012 03:52 AM
Hi Ngoldwat,
did you find or saw something the sniffer output?
please advice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2012 11:39 AM
Hi,
I see MANY checksum errors between 172.22.70.56 & ungrateful.
171 11:36:03.003688 ungrateful.cisco.com 172.22.70.56 TCP [TCP ACKed lost segment] 55625 > ms-wbt-server [ACK] Seq=224 Ack=9139 Win=64240 Len=0
(filter ip.src == 172.22.70.56)
Can you SSH to the device from the LMS server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2012 02:43 AM
Hi,
Yes I can SSH the device from the LMS server, I even shout ports to be sure,
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2012 05:55 AM
I am not sure why you can view the device when not integrated with ACS but you may want to look at this post:
https://supportforums.cisco.com/thread/2025768
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2012 07:43 AM
Hi Ngoldwat,
I solve the problem.
-the when I added a new device to the LMS i didn't fill the DOMAIN Company (and its was on our old domain),
when I try to ping the device from the LMS server I got a different IP address, then I start to query why it gives me the IP D.G.
I deleted the device and add it again and this time I gave him the new domain and everything worked perfectly,
I just wanted to say thanks for you replays and assistance.
have a nice day
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide