- Cisco Community
- Technology and Support
- Networking
- Network Management
- Neccessity to use Catalyst 2960 to connect Aironet CAPs 1552SA through ASA5525X to connect a PC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2018 08:54 AM - edited 03-01-2019 06:20 PM
Hi everyone,
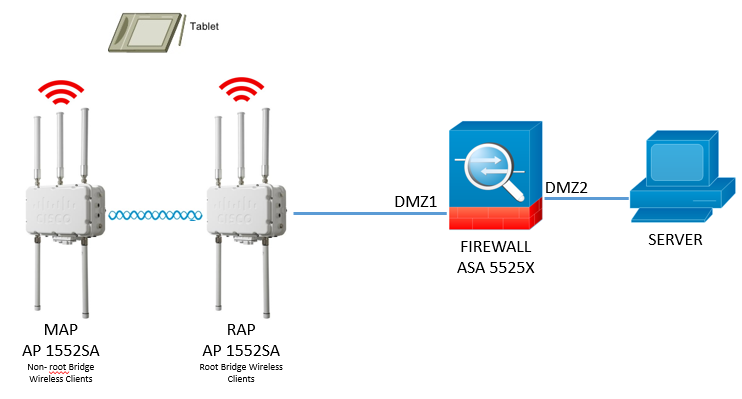
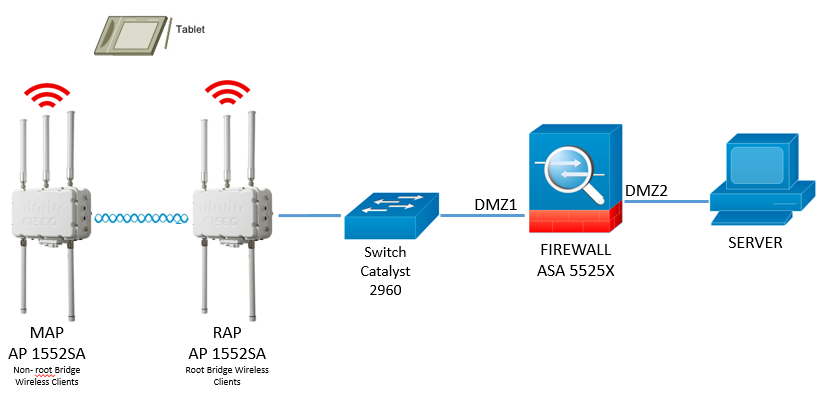
I have to connect the tablet to the server with Remote Access through my APs (CAP1552SA) and Firewall ASA5525X. The question is if it´s neccessary to implement a Switch between RAP and ASA5525X or not.
The CAPs are in Autonomus Mode because we don´t have WLC.
Please see the pictures and tell me what´s correct and how to configure:
Picture 1:
Picture 2:
Thank you guys!
Hope to see any help.
Regards.
German Molina
Solved! Go to Solution.
- Labels:
-
Network Management
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2018 01:55 AM
Hello,
By default ASA5525-X supports subinterfaces to act "like a trunk" to connect to other switches or APs (in your case). First you need to ensure what VLANs you need to pass to the firewall: is it only VLANs for SSIDs or BVI interface as well? Lets assume you want to pass VLAN 10 and 11. One for SSID, another for BVI.
Second you need to configure subinterfaces on ASA:
interface GigabitEthernetX/X
description ** To AP **
no nameif
no security-level
no ip address
no shutdown
!
interface GigabitEthernetX/X.10
vlan 10
nameif vlan_10
security-level XX
ip address XXX.XXX.XXX.XXX YYY.YYY.YYY.YYY
no shutdown
!
interface GigabitEthernetX/X.20
vlan 10
nameif vlan_10
security-level XX
ip address XXX.XXX.XXX.XXX YYY.YYY.YYY.YYY
no shutdown
You can also use VLAN secondary option if both of your VLANs requires same security-level. By default ASA5525-X is using dot11q encapsulation, same as AP.
More information could be found here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2018 12:06 PM
It is not necessary to add a switch between the firewall and AP, it only matters if you plan on adding more APs to that firewall interface zone.
The switch really add much it would just extend that area off of the firewall so if you only require the one root bridge you can go directly into the firewall.
If you feel like you might require more root bridge APs connected to that firewall zone in the future then you should put a switch in there.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2018 01:29 PM
Well, I thought the neccessity of the Switch in there is because I had to configure the following lines in the port where AP is connected,
Switchport mode trunk
Switchport trunk encapsulation dot1q
Switchport trunk native vlan 1
Switchport trunk allowed vlan 1
I believe ASA 5525X can´t receive those commands. Don´t know.
All the connection has been made through VLAN 1.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2018 01:55 AM
Hello,
By default ASA5525-X supports subinterfaces to act "like a trunk" to connect to other switches or APs (in your case). First you need to ensure what VLANs you need to pass to the firewall: is it only VLANs for SSIDs or BVI interface as well? Lets assume you want to pass VLAN 10 and 11. One for SSID, another for BVI.
Second you need to configure subinterfaces on ASA:
interface GigabitEthernetX/X
description ** To AP **
no nameif
no security-level
no ip address
no shutdown
!
interface GigabitEthernetX/X.10
vlan 10
nameif vlan_10
security-level XX
ip address XXX.XXX.XXX.XXX YYY.YYY.YYY.YYY
no shutdown
!
interface GigabitEthernetX/X.20
vlan 10
nameif vlan_10
security-level XX
ip address XXX.XXX.XXX.XXX YYY.YYY.YYY.YYY
no shutdown
You can also use VLAN secondary option if both of your VLANs requires same security-level. By default ASA5525-X is using dot11q encapsulation, same as AP.
More information could be found here:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide