- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Anyconnect unable to connect network - inside bvi interface
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2020 01:09 AM
Hello, i have to following problem.
Connected via anyconnect (vpn ip address 10.10.10.239) , i am not able to connect to 10.10.11.10 which is on interface bvi2
ASA# sh version
Cisco Adaptive Security Appliance Software Version 9.8(1)
Firepower Extensible Operating System Version 2.2(1.47)
Device Manager Version 7.8(1)
ASA# sh run
ASA Version 9.8(1)
!
hostname ASA
domain-name rornet.ro
ip local pool Euro 10.10.10.239-10.10.10.254 mask 255.255.255.0
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 89.238.216.40 255.255.255.240
!
interface GigabitEthernet1/2
XXXXXXXX
!
interface GigabitEthernet1/3
bridge-group 1
nameif OsloEth0+modem1+management-oslo_1
security-level 100
!
interface GigabitEthernet1/4
XXXXXXXX
!
interface GigabitEthernet1/5
bridge-group 2
nameif osloEth1+modem2_1
security-level 100
!
interface GigabitEthernet1/6
bridge-group 2
nameif osloEth1+modem2_2
security-level 100
!
interface GigabitEthernet1/7
XXXXXXXXXxx
!
interface GigabitEthernet1/8
bridge-group 1
nameif OsloEth0+modem1+management-oslo_2
security-level 100
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
interface BVI1
nameif OsloEth0+modem1+management-oslo
security-level 100
ip address 10.10.10.1 255.255.255.0
!
interface BVI2
description osloEth1+modem2
nameif OsloEth1+modem2
security-level 100
ip address 10.10.11.1 255.255.255.0
!
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj_any1
subnet 0.0.0.0 0.0.0.0
object network obj_any2
subnet 0.0.0.0 0.0.0.0
object network obj_any3
subnet 0.0.0.0 0.0.0.0
object network obj_any4
subnet 0.0.0.0 0.0.0.0
object network obj_any5
subnet 0.0.0.0 0.0.0.0
object network obj_any6
subnet 0.0.0.0 0.0.0.0
object network obj_any7
subnet 0.0.0.0 0.0.0.0
object network Local-Codecs
subnet 192.168.6.0 255.255.255.0
object network EuroRadio_CGT
subnet 192.168.101.0 255.255.255.0
object network NETWORK_OBJ_10.10.10.96_28
subnet 10.10.10.96 255.255.255.240
object network NETWORK_OBJ_192.168.6.0_24
subnet 192.168.6.0 255.255.255.0
object network 6.6-VNC
host 192.168.6.6
object network 6.2-VNC
host 192.168.6.2
object network SRR_PUBLIC
host 89.238.216.40
object service OBJ-TCP-VNC
service tcp source eq 6000
object network VPN_POOL
subnet 10.10.10.0 255.255.255.0
description VPN_POOL
object-group network PoolLocalCodecs
network-object host 192.168.6.250
network-object host 192.168.6.251
network-object host 192.168.6.252
network-object host 192.168.6.253
network-object host 192.168.6.254
object-group network NO_NAT_VPN_DESTINATION1
network-object 10.10.11.0 255.255.255.0
object-group network NO_NAT_VPN_DESTINATION2
network-object host 10.10.10.10
network-object 10.10.10.0 255.255.255.0
access-list srr_splitTunnelAcl standard permit 10.10.10.0 255.255.255.0
access-list srr_splitTunnelAcl standard permit 10.10.11.0 255.255.255.0
access-list srr_splitTunnelAcl standard permit 192.168.100.0 255.255.255.0
access-list srr_splitTunnelAcl standard permit 192.168.101.0 255.255.255.0
access-list srr_splitTunnelAcl standard permit 192.168.6.0 255.255.255.0
access-list OsloEth0+modem1+management-oslo_access_in extended permit ip any any
access-list OsloEth1+modem2_access_in extended permit ip any any
access-list Local-Codecs_nat0_outbound extended permit ip 192.168.6.0 255.255.255.0 object-group PoolLocalCodecs
access-list srrcodecs_splitTunnel standard permit 192.168.6.0 255.255.255.0
access-list srrcodecs_splitTunnel standard permit 193.231.72.0 255.255.255.0
access-list srrcodecs_splitTunnel standard permit 89.238.216.32 255.255.255.240
access-list srrcodecs_splitTunnel standard permit 10.10.10.0 255.255.255.0
access-list srrcodecs_splitTunnel standard permit 10.10.11.0 255.255.255.0
access-list SRR-LAN_in extended deny ip any any log
access-list VPN1_splitTunnelAcl standard permit 192.168.6.0 255.255.255.0
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq lpd
access-list AnyConnect_Client_Local_Print remark IPP: Internet Printing Protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 631
access-list AnyConnect_Client_Local_Print remark Windows' printing port
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 9100
access-list AnyConnect_Client_Local_Print remark mDNS: multicast DNS protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.251 eq 5353
access-list AnyConnect_Client_Local_Print remark LLMNR: Link Local Multicast Name Resolution protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.252 eq 5355
access-list AnyConnect_Client_Local_Print remark TCP/NetBIOS protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 137
access-list AnyConnect_Client_Local_Print extended permit udp any4 any4 eq netbios-ns
access-list outside_in extended permit tcp any object 6.6-VNC eq 5900
access-list outside_in extended permit tcp any object 6.2-VNC eq 5901
access-list outside_in extended permit ip 10.10.10.0 255.255.255.0 10.10.11.0 255.255.255.0
access-list outside_in extended permit ip 172.18.1.0 255.255.255.0 10.10.11.0 255.255.255.0
access-list outside_in extended permit ip 10.10.11.0 255.255.255.0 10.10.10.0 255.255.255.0
access-list outside_in extended permit ip 10.10.11.0 255.255.255.0 172.18.1.0 255.255.255.0
pager lines 24
logging enable
logging timestamp
logging trap notifications
logging history emergencies
logging asdm errors
logging host outside 10.1.0.100
logging host outside 10.106.0.50
mtu outside 1500
mtu SRR-LAN 1500
mtu OsloEth0+modem1+management-oslo_1 1500
mtu Local-Codecs 1500
mtu osloEth1+modem2_1 1500
mtu osloEth1+modem2_2 1500
mtu EuroRadio_CGT 1500
mtu OsloEth0+modem1+management-oslo_2 1500
icmp unreachable rate-limit 1 burst-size 1
icmp permit any SRR-LAN
icmp permit any Local-Codecs
icmp permit any EuroRadio_CGT
icmp permit any OsloEth0+modem1+management-oslo
icmp permit any OsloEth1+modem2
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (EuroRadio_CGT,outside) source static NETWORK_OBJ_192.168.6.0_24 NETWORK_OBJ_192.168.6.0_24 destination static NETWORK_OBJ_10.10.10.96_28 NETWORK_OBJ_10.10.10.96_28 no-proxy-arp route-lookup
nat (Local-Codecs,outside) source static NETWORK_OBJ_192.168.6.0_24 NETWORK_OBJ_192.168.6.0_24 destination static NETWORK_OBJ_10.10.10.96_28 NETWORK_OBJ_10.10.10.96_28 no-proxy-arp route-lookup
!
object network Local-Codecs
nat (Local-Codecs,outside) dynamic interface
object network EuroRadio_CGT
nat (EuroRadio_CGT,outside) dynamic interface
object network 6.6-VNC
nat (Local-Codecs,outside) static interface service tcp 5900 5900
object network 6.2-VNC
nat (Local-Codecs,outside) static interface service tcp 5901 5901
access-group outside_in in interface outside
access-group SRR-LAN_in in interface SRR-LAN
access-group OsloEth0+modem1+management-oslo_access_in in interface OsloEth0+modem1+management-oslo
access-group OsloEth1+modem2_access_in in interface OsloEth1+modem2
route outside 0.0.0.0 0.0.0.0 89.238.216.33 1
route SRR-LAN 10.0.0.0 255.0.0.0 10.1.0.1 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authorization command LOCAL
aaa authorization exec LOCAL
aaa authentication login-history
http server enable 50000
http 193.231.72.0 255.255.255.0 outside
http 86.120.118.125 255.255.255.255 outside
http 89.238.213.250 255.255.255.255 outside
http 10.1.20.0 255.255.255.0 outside
http 195.82.148.30 255.255.255.255 outside
http 192.168.6.250 255.255.255.255 outside
http 192.168.6.251 255.255.255.255 outside
http 192.168.6.252 255.255.255.255 outside
http 192.168.6.253 255.255.255.255 outside
http 192.168.6.254 255.255.255.255 outside
http 10.1.0.0 255.255.0.0 SRR-LAN
http 79.246.82.240 255.255.255.255 outside
http 5.154.236.2 255.255.255.255 outside
snmp-server host outside 10.1.0.100 community ***** version 2c
snmp-server host outside 10.106.0.161 poll community *****
no snmp-server location
no snmp-server contact
snmp-server community *****
sysopt noproxyarp outside
service sw-reset-button
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs group1
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 20
authentication rsa-sig
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 40
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 50
authentication rsa-sig
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 70
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 80
authentication rsa-sig
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 100
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 110
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 130
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 140
authentication rsa-sig
encryption des
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh stricthostkeycheck
ssh 0.0.0.0 0.0.0.0 outside
ssh 10.1.0.0 255.255.0.0 SRR-LAN
ssh 10.0.0.0 255.0.0.0 SRR-LAN
ssh timeout 60
ssh version 2
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 10.1.50.1
webvpn
enable outside
anyconnect image disk0:/anyconnect-win-4.5.03040-webdeploy-k9.pkg 2
anyconnect image disk0:/anyconnect-macos-4.5.03040-webdeploy-k9.pkg 3
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy DfltGrpPolicy attributes
vpn-idle-timeout 2
group-policy GroupPolicy_SSL internal
group-policy GroupPolicy_SSL attributes
wins-server none
dns-server value 193.231.236.25
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value srrcodecs_splitTunnel
default-domain value rornet.ro
tunnel-group SSL type remote-access
tunnel-group SSL general-attributes
address-pool Euro
default-group-policy GroupPolicy_SSL
tunnel-group SSL webvpn-attributes
group-alias SSL enable
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:b735bbefc44e5cb8ac0c5c0e2c5fe051
: end
ASA# packet-tracer input outside icmp 10.10.10.239 8 1 10.10.11.10
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.10.11.10 using egress ifc OsloEth1+modem2
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_in in interface outside
access-list outside_in extended permit ip 10.10.10.0 255.255.255.0 10.10.11.0 255.255.255.0
Additional Information:
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_in in interface outside
access-list outside_in extended permit ip 10.10.10.0 255.255.255.0 10.10.11.0 255.255.255.0
Additional Information:
Phase: 6
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: CP-PUNT
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 9
Type: WEBVPN-SVC
Subtype: in
Result: DROP
Config:
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: OsloEth1+modem2
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
ASA# packet-tracer input outside tcp 10.10.10.239 80 10.10.11.10 80 detailed
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.10.11.10 using egress ifc OsloEth1+modem2
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_in in interface outside
access-list outside_in extended permit ip 10.10.10.0 255.255.255.0 10.10.11.0 255.255.255.0
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f29ec2258f0, priority=13, domain=permit, deny=false
hits=4, user_data=0x7f29e2aab2c0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=10.10.10.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=10.10.11.0, mask=255.255.255.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f29e94341f0, priority=0, domain=nat-per-session, deny=false
hits=3922254, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f29ea07c810, priority=0, domain=inspect-ip-options, deny=true
hits=2491683, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 5
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_in in interface outside
access-list outside_in extended permit ip 10.10.10.0 255.255.255.0 10.10.11.0 255.255.255.0
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f29ec2258f0, priority=13, domain=permit, deny=false
hits=5, user_data=0x7f29e2aab2c0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=10.10.10.0, mask=255.255.255.0, port=0, tag=any
dst ip/id=10.10.11.0, mask=255.255.255.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 6
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f29e94341f0, priority=0, domain=nat-per-session, deny=false
hits=3922255, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 7
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f29ea07c810, priority=0, domain=inspect-ip-options, deny=true
hits=2491684, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 8
Type: CP-PUNT
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f29eae7f800, priority=79, domain=punt, deny=true
hits=84, user_data=0x7f29e90323e0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=10.10.10.239, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 9
Type: WEBVPN-SVC
Subtype: in
Result: DROP
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f29edc19760, priority=71, domain=svc-ib-tunnel-flow, deny=false
hits=84, user_data=0xe28000, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=10.10.10.239, mask=255.255.255.255, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: OsloEth1+modem2
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
What i think is that traffic from 10.10.11.10 needs to be extempt, going out through internet, it should go through the vpn tunnel:
I have tried:
object-group network NO_NAT_VPN_DESTINATION1
network-object 10.10.11.0 255.255.255.0
object-group network NO_NAT_VPN_DESTINATION2
network-object 10.10.10.0 255.255.255.0
!not working because it is a bvi interface
nat (OsloEth1+modem2,outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static VPN_POOL VPN_POOL no-proxy-arp
! i have tried this , but it didn`t worked
nat (osloEth1+modem2_1,outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static NO_NAT_VPN_DESTINATION2 NO_NAT_VPN_DESTINATION2 no-proxy-arp
nat (osloEth1+modem2_2,outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static NO_NAT_VPN_DESTINATION2 NO_NAT_VPN_DESTINATION2 no-proxy-arp
Connected with anyconnect, i am able to ping 10.10.10.0..
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2020 05:52 AM
while you connected to anyconnect could you reach to address 10.10.11.0/24 I know when you did a packet tracer it is showing its taking the right path for natting. instead of doing a packet tracer could you please connect at something on 10.10.11.0/24 range. i mean in term of real live network. your nat rules and tunnel-group and the group-policy looks good.
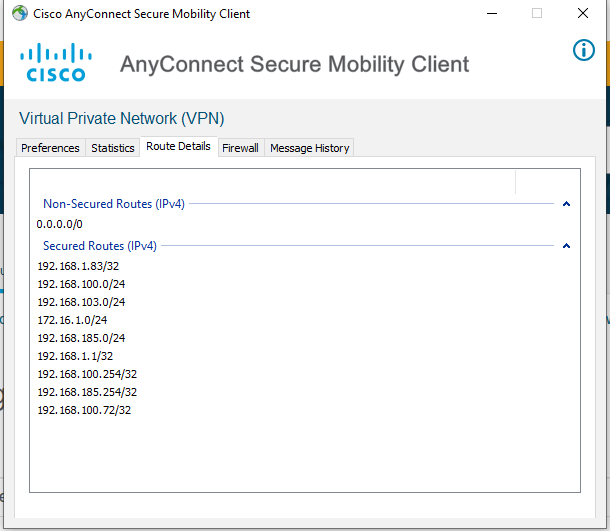
could you also double check your split tunnel ip addresses are shown in your anyconnect client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2020 04:57 AM
here apply these config and test it.
object network ANYCONNECT-POOL range 10.10.10.239 10.10.10.254 ! object network ANYCONNECT-POOL range 10.10.10.239 10.10.10.254 nat (outside,outside) dynamic interface ! nat (any,outside) source static any any dest static ANYCONNECT-POOL ANYCONNECT-POOL no-proxy-arp route-lookup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2020 05:09 AM
Dear Salim,
Many thanks for you answer. I did apply all of you`re recommandations. Unfortunelly, problem is the same.
I have tried to packed trace with a unused ip now, and the flow seems fine. I am only able to ping/telnet an ip from the same subnet from the vpn class, but not 10.10.11.10
ASA# sh vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : X Index : 26322
Assigned IP : 10.10.10.241 Public IP : 193.231.72.7
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA1
Bytes Tx : 255074 Bytes Rx : 78927
Group Policy : GroupPolicy_SSL Tunnel Group : SSL
Login Time : 14:49:58 EEDT Thu Jun 4 2020
Duration : 0h:16m:28s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : 0a0a0a01066d20005ed8dfe6
Security Grp : none
Username : X Index : 52633
Assigned IP : 10.10.10.242 Public IP : 86.120.253.68
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA1
Bytes Tx : 22016 Bytes Rx : 58851
Group Policy : GroupPolicy_SSL Tunnel Group : SSL
Login Time : 15:04:17 EEDT Thu Jun 4 2020
Duration : 0h:02m:09s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : 0a0a0a010cd990005ed8e341
Security Grp : none
ASA-EURORADIO# packet-tracer input outside icmp 10.10.10.243 8 1 10.10.11.10
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.10.11.10 using egress ifc OsloEth1+modem2
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (any,outside) source static any any destination static ANYCONNECT-POOL ANYCONNECT-POOL no-proxy-arp route-lookup
Additional Information:
NAT divert to egress interface OsloEth1+modem2
Untranslate 10.10.11.10/0 to 10.10.11.10/0
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_in in interface outside
access-list outside_in extended permit ip 10.10.10.0 255.255.255.0 10.10.11.0 255.255.255.0
Additional Information:
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (any,outside) source static any any destination static ANYCONNECT-POOL ANYCONNECT-POOL no-proxy-arp route-lookup
Additional Information:
Static translate 10.10.10.243/0 to 10.10.10.243/0
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_in in interface outside
access-list outside_in extended permit ip 10.10.10.0 255.255.255.0 10.10.11.0 255.255.255.0
Additional Information:
Phase: 8
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (any,outside) source static any any destination static ANYCONNECT-POOL ANYCONNECT-POOL no-proxy-arp route-lookup
Additional Information:
Static translate 10.10.10.243/0 to 10.10.10.243/0
Phase: 9
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 10
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 11
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect icmp
service-policy global_policy global
Additional Information:
Phase: 12
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Phase: 13
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Phase: 14
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (any,outside) source static any any destination static ANYCONNECT-POOL ANYCONNECT-POOL no-proxy-arp route-lookup
Additional Information:
Phase: 15
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect icmp
service-policy global_policy global
Additional Information:
Phase: 16
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Phase: 17
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Phase: 18
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (any,outside) source static any any destination static ANYCONNECT-POOL ANYCONNECT-POOL no-proxy-arp route-lookup
Additional Information:
Phase: 19
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 2695765, packet dispatched to next module
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: OsloEth1+modem2
output-status: up
output-line-status: up
Action: allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2020 05:27 AM - edited 06-04-2020 05:35 AM
share the show run nat and show nat detail output please.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2020 05:38 AM
ASA-EURORADIO# sh run nat
nat (OsloEth0+modem1+management-oslo_1,outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
nat (OsloEth0+modem1+management-oslo_2,outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
nat (OsloEth0+modem1+management-oslo_1,outside) source static NO_NAT_VPN_DESTINATION2 NO_NAT_VPN_DESTINATION2 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
nat (OsloEth0+modem1+management-oslo_2,outside) source static NO_NAT_VPN_DESTINATION2 NO_NAT_VPN_DESTINATION2 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
nat (osloEth1+modem2_1,outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
nat (osloEth1+modem2_2,outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
nat (osloEth1+modem2_2,outside) source static NO_NAT_VPN_DESTINATION2 NO_NAT_VPN_DESTINATION2 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
nat (osloEth1+modem2_1,outside) source static NO_NAT_VPN_DESTINATION2 NO_NAT_VPN_DESTINATION2 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
nat (any,outside) source static ANYCONNECT-POOL ANYCONNECT-POOL destination static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 no-proxy-arp route-lookup
Above are some of my atempts.
nat (any,outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static ANYCONNECT-POOL ANYCONNECT-POOL no-proxy-arp route-lookup
!
object network ANYCONNECT-POOL
nat (outside,outside) dynamic interface
ASA-EURORADIO# show nat detail
Manual NAT Policies (Section 1)
1 (EuroRadio_CGT) to (outside) source static NETWORK_OBJ_192.168.6.0_24 NETWORK_OBJ_192.168.6.0_24 destination static NETWORK_OBJ_10.10.10.96_28 NETWORK_OBJ_10.10.10.96_28 no-proxy-arp route-lookup
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.6.0/24, Translated: 192.168.6.0/24
Destination - Origin: 10.10.10.96/28, Translated: 10.10.10.96/28
2 (Local-Codecs) to (outside) source static NETWORK_OBJ_192.168.6.0_24 NETWORK_OBJ_192.168.6.0_24 destination static NETWORK_OBJ_10.10.10.96_28 NETWORK_OBJ_10.10.10.96_28 no-proxy-arp route-lookup
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.6.0/24, Translated: 192.168.6.0/24
Destination - Origin: 10.10.10.96/28, Translated: 10.10.10.96/28
3 (OsloEth0+modem1+management-oslo_1) to (outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
translate_hits = 0, untranslate_hits = 0
Source - Origin: 10.10.11.0/24, Translated: 10.10.11.0/24
Destination - Origin: 172.18.1.0/24, Translated: 172.18.1.0/24
4 (OsloEth0+modem1+management-oslo_2) to (outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
translate_hits = 0, untranslate_hits = 0
Source - Origin: 10.10.11.0/24, Translated: 10.10.11.0/24
Destination - Origin: 172.18.1.0/24, Translated: 172.18.1.0/24
5 (OsloEth0+modem1+management-oslo_1) to (outside) source static NO_NAT_VPN_DESTINATION2 NO_NAT_VPN_DESTINATION2 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
translate_hits = 482, untranslate_hits = 0
Source - Origin: 10.10.10.0/24, Translated: 10.10.10.0/24
Destination - Origin: 172.18.1.0/24, Translated: 172.18.1.0/24
6 (OsloEth0+modem1+management-oslo_2) to (outside) source static NO_NAT_VPN_DESTINATION2 NO_NAT_VPN_DESTINATION2 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
translate_hits = 5, untranslate_hits = 0
Source - Origin: 10.10.10.0/24, Translated: 10.10.10.0/24
Destination - Origin: 172.18.1.0/24, Translated: 172.18.1.0/24
7 (osloEth1+modem2_1) to (outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
translate_hits = 0, untranslate_hits = 0
Source - Origin: 10.10.11.0/24, Translated: 10.10.11.0/24
Destination - Origin: 172.18.1.0/24, Translated: 172.18.1.0/24
8 (osloEth1+modem2_2) to (outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
translate_hits = 427, untranslate_hits = 0
Source - Origin: 10.10.11.0/24, Translated: 10.10.11.0/24
Destination - Origin: 172.18.1.0/24, Translated: 172.18.1.0/24
9 (osloEth1+modem2_2) to (outside) source static NO_NAT_VPN_DESTINATION2 NO_NAT_VPN_DESTINATION2 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
translate_hits = 0, untranslate_hits = 0
Source - Origin: 10.10.10.0/24, Translated: 10.10.10.0/24
Destination - Origin: 172.18.1.0/24, Translated: 172.18.1.0/24
10 (osloEth1+modem2_1) to (outside) source static NO_NAT_VPN_DESTINATION2 NO_NAT_VPN_DESTINATION2 destination static NO_NAT_VPN_CLASS NO_NAT_VPN_CLASS no-proxy-arp route-lookup
translate_hits = 0, untranslate_hits = 0
Source - Origin: 10.10.10.0/24, Translated: 10.10.10.0/24
Destination - Origin: 172.18.1.0/24, Translated: 172.18.1.0/24
11 (any) to (outside) source static ANYCONNECT-POOL ANYCONNECT-POOL destination static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 no-proxy-arp route-lookup
translate_hits = 0, untranslate_hits = 0
Source - Origin: 10.10.10.239-10.10.10.254, Translated: 10.10.10.239-10.10.10.254
Destination - Origin: 10.10.11.0/24, Translated: 10.10.11.0/24
12 (any) to (outside) source static NO_NAT_VPN_DESTINATION1 NO_NAT_VPN_DESTINATION1 destination static ANYCONNECT-POOL ANYCONNECT-POOL no-proxy-arp route-lookup
translate_hits = 7, untranslate_hits = 0
Source - Origin: 10.10.11.0/24, Translated: 10.10.11.0/24
Destination - Origin: 10.10.10.239-10.10.10.254, Translated: 10.10.10.239-10.10.10.254
Auto NAT Policies (Section 2)
1 (Local-Codecs) to (outside) source static 6.2-VNC interface service tcp 5901 5901
translate_hits = 0, untranslate_hits = 305903
Source - Origin: 192.168.6.2/32, Translated: 89.238.216.40/28
Service - Protocol: tcp Real: 5901 Mapped: 5901
2 (Local-Codecs) to (outside) source static 6.6-VNC interface service tcp 5900 5900
translate_hits = 0, untranslate_hits = 1031745
Source - Origin: 192.168.6.6/32, Translated: 89.238.216.40/28
Service - Protocol: tcp Real: 5900 Mapped: 5900
3 (outside) to (outside) source dynamic ANYCONNECT-POOL interface
translate_hits = 357, untranslate_hits = 0
Source - Origin: 10.10.10.239-10.10.10.254, Translated: 89.238.216.40/28
4 (Local-Codecs) to (outside) source dynamic Local-Codecs interface
translate_hits = 445775, untranslate_hits = 6982
Source - Origin: 192.168.6.0/24, Translated: 89.238.216.40/28
5 (EuroRadio_CGT) to (outside) source dynamic EuroRadio_CGT interface
translate_hits = 661893, untranslate_hits = 57196
Source - Origin: 192.168.101.0/24, Translated: 89.238.216.40/28
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2020 05:52 AM
while you connected to anyconnect could you reach to address 10.10.11.0/24 I know when you did a packet tracer it is showing its taking the right path for natting. instead of doing a packet tracer could you please connect at something on 10.10.11.0/24 range. i mean in term of real live network. your nat rules and tunnel-group and the group-policy looks good.
could you also double check your split tunnel ip addresses are shown in your anyconnect client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2020 11:05 PM
Many thanks Salim for you`re support . 5 stars for you`re professionalism!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide