- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: API based tool to save the Access Control Policy from FMC as CSV
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
API based tool to save the Access Control Policy from FMC as CSV
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2019 12:09 AM - edited 04-29-2022 04:03 AM
Hello Everyone,
Very often as Network Administrator there is a need to save the ACP on the Firepower Management Center(FMC) as CSV, while the FMC in itself supports the policy import and export option as a full-fledged feature there is no way to save the ACP as CSV.
The script attached here solves the problem, however, this is not a replacement for the backup features from FMC.
Note: This tool by no means is a replacement for the policy import and export option of FMC. This tool is intended to have the CSV generated for ACP.
It does not take the backup of the objects or IPS/File Policy associated, it just gives a listing of the configuration.
What is supported:
1. Policy extraction from the FMC over API.
2. Extracts Zones, Networks, Applications, URL's, Users, IPS Policy, File Policy, Variable Sets, Logging configurations.
3. The output format is in CSV with ";" separated multiple entries within a specific field.
4. Currently supported only on FMC, no FDM support available.
Upcoming features:
1. Auto-listing of available policies across the domains.
2. Support for ISE/SGT attributes.
3. Writing the CSV backup as ACP to the FMC.
Link on Devnet:
https://developer.cisco.com/codeexchange/github/repo/raghukul-cisco/csvExportFirepower/
The tool will be updated every month with new features wherever applicable.
#Firepower #FMC
P.S: This is not an official tool, so please leave your comment/feedback below and we will try our best to address it as soon as possible.
Version 3: Support for large rule sets. @Anupam Pavithran
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-02-2020 01:33 PM
Traceback (most recent call last):
File "Export-Policies.py", line 147, in <module>
for rule in response.json()["items"]:
KeyError: 'items'
I am facing this error. Please help me on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2020 03:12 AM
Be sure to follow the directions under Requirements in the README.md. You need to:
pip install -r fireREST/requirements.txt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2020 08:29 AM
C:\Policy CSV-rel2\Policy CSV>pip install -r fireREST/requirements.txt
Requirement already satisfied: requests in c:\python38\lib\site-packages (from -r fireREST/requirements.txt (line 1)) (2.24.0)
Requirement already satisfied: chardet<4,>=3.0.2 in c:\python38\lib\site-packages (from requests->-r fireREST/requirements.txt (line 1)) (3.0.4)
Requirement already satisfied: certifi>=2017.4.17 in c:\python38\lib\site-packages (from requests->-r fireREST/requirements.txt (line 1)) (2020.6.20)
Requirement already satisfied: urllib3!=1.25.0,!=1.25.1,<1.26,>=1.21.1 in c:\python38\lib\site-packages (from requests->-r fireREST/requirements.txt (line 1)) (1.25.10)
Requirement already satisfied: idna<3,>=2.5 in c:\python38\lib\site-packages (from requests->-r fireREST/requirements.txt (line 1)) (2.10)
The requirement is already satified, but somehow it is falling,
or do I need Python 2.7 to work ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2020 09:05 AM
Hi,
I would like to run this on a production environment with more than 12K ACLs. Is there any risk to run it in production? If we open a case, would you be able to help on this?
Besides, Is there any test lab hosted by cisco where this can be tested?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 08:03 PM
The script was tested with 100rules on the FMC (which then expands into multiple rules on the device). There is no lab hosted as such specifically for testing the tool.
The tool is not an official tool, hence support for the tool as part of TAC is not possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2021 11:08 AM
Hello Raghunath
I ran this successfully on the same firewall quite a few times but recently its giving errors as attached. Every time it gives error after writing random number of acls in the csv. As you can see in the attached image, this time it gave an error after writing 8500 acls. The error is however the same every time which is at line 147.
Could you please help on this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2020 06:27 AM
For what it is worth, we consistently run this on our production environment that has close to 1,000 ACLs without any issues.
I hope that helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2021 11:04 AM
Thanks! I ran it on a firewall which has 12K+ ACLs and worked fine that time! But recently giving errors.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2020 11:58 AM - edited 12-08-2020 12:56 PM
Hi. Tool looks great.
Does anyone have any idea on what may cause the following error:
Traceback (most recent call last):
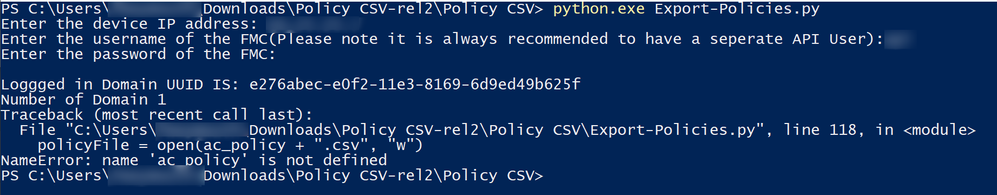
File "C:\Python_Cisco\Policy CSV\Export-Policies.py", line 26, in <module>
ac_policy = Test
NameError: name 'Test' is not defined
In the Export-Policies.py file I did not see a variable listing for the name of the access policy, so I created one called ac_policy = Test
I have created an access policy on the FMC named Test.
Looking forward to your response!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-08-2020 11:26 PM
Hi there,
You don't have to make any changes to the script.
Once you run the script, you'd get the option to select Access Control Policy (In your case, Test)
PS C:\Users\anupam\AC Policy CSV-rel2\Policy CSV> python .\Export-Policies.py Enter the device IP address: 10.106.50.80 Enter the username of the FMC(Please note it is always recommended to have a seperate API User):api Enter the password of the FMC: Loggged in Domain UUID IS: e276abec-e0f2-11e3-8169-6d9ed49b625f Number of Domain 1 1 Blackbriar 2 SFR 5516 Choose the ACP for which CSV has to be generated(integer value):1 The selected AC policy is: Blackbriar ------------------------------------------------------------------------------------- Domain: e276abec-e0f2-11e3-8169-6d9ed49b625f ------------------------------------------------------------------------------------- Access control policy: Blackbriar: 005056BD-C739-0ed3-0000-017179869899 ------------------------------------------------------------------------------------- Writing rule #1 to CSV... Writing rule #2 to CSV... Writing rule #3 to CSV... Writing rule #4 to CSV... Writing rule #5 to CSV... Writing rule #6 to CSV... File is at: ./Blackbriar.csv
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2020 06:13 AM
I have downloaded a fresh copy of the script and this is what I am seeing:
[cid:image001.png@01D6CDFA.A50BA450]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2020 06:14 AM
Hello. This is what I see after copying a fresh download of the script:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2020 07:29 AM
Alright, can you un-comment line number 95 and re-run and share the output. The first occurrence after acp_name =[]
json_resp = json.loads(resp)
print (json_resp['items']) <<<<-------------- remove the #
iterate = 1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2020 11:03 AM
Hello Anupam -
I got this working finally. It was not the script but the API user I created on the FMC did not have permissions to the access policies.
It worked perfectly after that.
Great tool.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2021 01:22 AM
Hi. Can you guide me
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: