- Cisco Community
- Technology and Support
- Security
- Network Security
- I just wanted to let you know
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2016 03:31 AM - edited 03-12-2019 01:34 AM
Hello All,
I need to allow IPSEC NAT-T through an ASA5520 Ver 9.17. The vendor has stated that I need to forward UDP ports 500 and 4500 and also ICMP and ESP to the interface of their router which will be the termination point for the VPN tunnel. Unfortunately, my knowledge of ASA configuration is limited to basic setup and this is a little beyond me. I have been reading on the forum, but I am a little confused about how to configure this correctly as I have found a lot of information and I can't decide what is needed. Below is the network diagram that the vendor supplied.
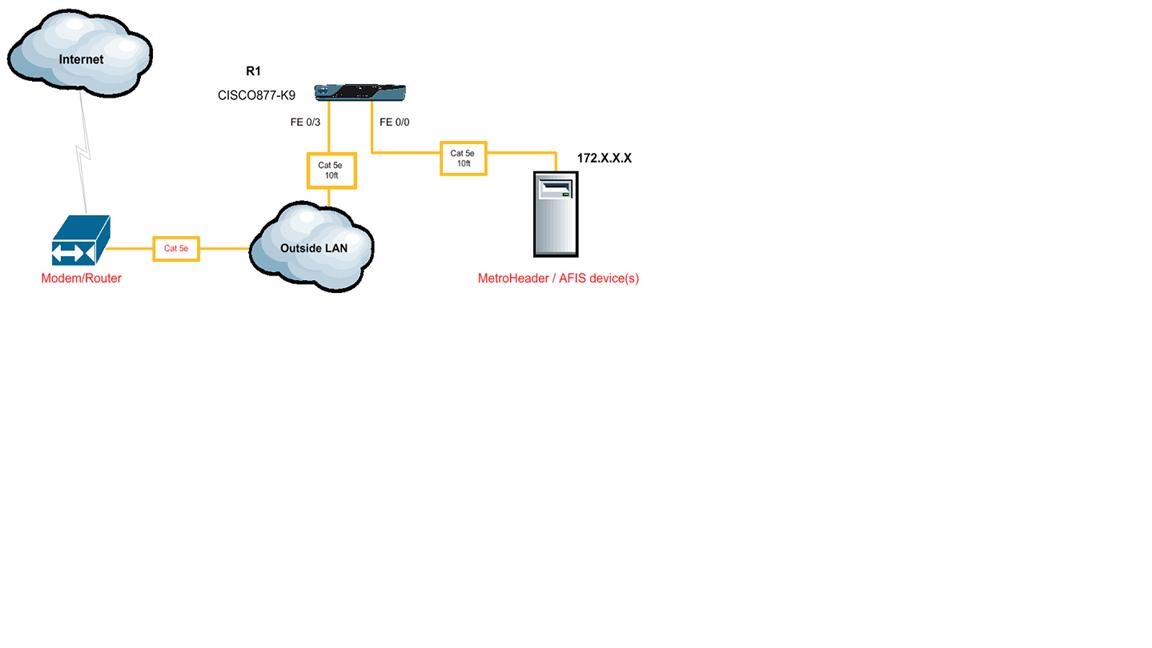
So far I am thinking the following needs to be added to the config...
object network metro_NAT-T
host 10.10.49.25
object network metro_isakmp
host 10.10.49.25
nat (911,outside) static 10.0.0.2 service udp 500 500
nat (911,outside) static 10.0.0.2 service udp 4500 4500
access-list 100 permit tcp any object metro_nat-t eq 500
access-list 100 permit tcp any object metro_isakmp eq 4500
The host IP is the WAN interface of the CISCO877 in the diagram. access-list 100 is in the outside interface.
The vendor also specified ESP protocol 50, but I am unsure how exactly to allow that.
I can post the entire ASA config if need be.
Any help on this would be greatly appreciated.
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2016 03:59 AM
If you did not use NAT-T you would have to permit esp but since NAT-T is used ESP traffic will be tunneled in UDP/4500. I have tested it yesterday to verify again and it worked fine. :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2016 12:59 PM
Your ACL permits TCP but you have to permit UDP/500 & UDP/4500
access-list 100 permit udp any metro_isakmp eq 500
access-list 100 permit udp any metro_isakmp eq 4500
If NAT-T is enabled ESP traffic will be tunneled over UDP/4500. No additional configuration should be required on your side.
Let me know if that answers your question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2016 03:56 AM
Oh thanks. I missed the access list thing. So just forwarding UDP ports 500 and 4500 to the VPN endpoint on the inside should allow the tunnel to work? I also read something about inspect esp or something like that but couldn't determine weather it applied to this situation.
Thanks for your help. I am installing this on Monday and would like to have the ASA configured properly before it goes in.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2016 03:59 AM
If you did not use NAT-T you would have to permit esp but since NAT-T is used ESP traffic will be tunneled in UDP/4500. I have tested it yesterday to verify again and it worked fine. :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2016 04:46 AM
That's excellent thanks.
I have the firewall ready to be installed and will be putting it in on Monday. I just thought of something else though...
The have AT&T Uverse at this location and it's actually two separate buildings that share an internet connection. It's kind of a weird situation because it's a rural county and although the two buildings are only about 50ft apart, only one address shows having the Uverse service available and the other does not. AT&T refuses to even consider installing separate internet service at the second building because their system shows it as being unavailable.
Anyway, The whole setup is complicated by the fact that AT&T utilizes a residential gateway even for it's business accounts. They have a /29 static block and the way I have it configured is one organization uses one IP and the other one in the other building uses another IP so the two are on separate LANs sharing the same internet connection.
AT&Ts residential gateway will only allow one static IP address to be used at any one time by a single MAC address. How they expect anyone to be able to utilize their static block with these devices is beyond me. Anyway, the way I have found to work around this little challenge is to install a 2811 between the AT&T RG and their firewall. I configured HSRP on the 2811 so that the RG could be happy assigning each static IP to a different MAC address. I then use NAT on the 2811 and then again on the firewall. The end result is the ability to NAT each static IP ultimately to an interface on the firewall. (If anyone has a better idea on how to accomplish this, I'm all ears).
Long story short, because of the goofy design of the RG, they have a double NAT. The 2811 is configured to route all traffic to the LAN interface so it shouldn't interfere with NAT transversal should it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2016 01:51 PM
The current design will not interfere with NAT-T.
If I understood your issue with AT&T correctly you have to have a single mac address for every static ip address you use. The only possible solution I see here is using proxy-arp and using NAT on a edge router or firewall.
In case of asa you could use virtual mac adresses to make sure both primary and secondary use the same mac-address in case they are active
Sample confiuration
asa(config)# failover mac address gigabitethernet0/0 <active-mac> <standby-mac>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2016 02:41 AM
I just wanted to let you know that the ASA install yesterday went off without a hitch. There were some issues on the vendor side with getting the VPN tunnel set up, but my ASA config was solid.
Thanks again for all your help.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


