- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA 5520 weird behaviour and advice
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA 5520 weird behaviour and advice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2014 03:49 AM - edited 03-11-2019 08:52 PM
Good morning folks ,
I have an issue with asa 5520 on gns3 ,while i am able to ping loopback addresses i can not ping any physical interfaces.have you experiences such behaviour before? Now i need your advice, i have set up this network but i am new to asa and i am lost.so i need your precious help.i have 4 servers in dmz area .i want to use the public address in the outside interface .Servers will normally have a private addressing scheme i can not see any other option .R3 edge router needs to support easyvpn for remote users .i want to deploy pat in asa ..do you think this is feasible ? i am really confused ...and i do not know what to do .. any recommendations improving the network will be highly appreciated.
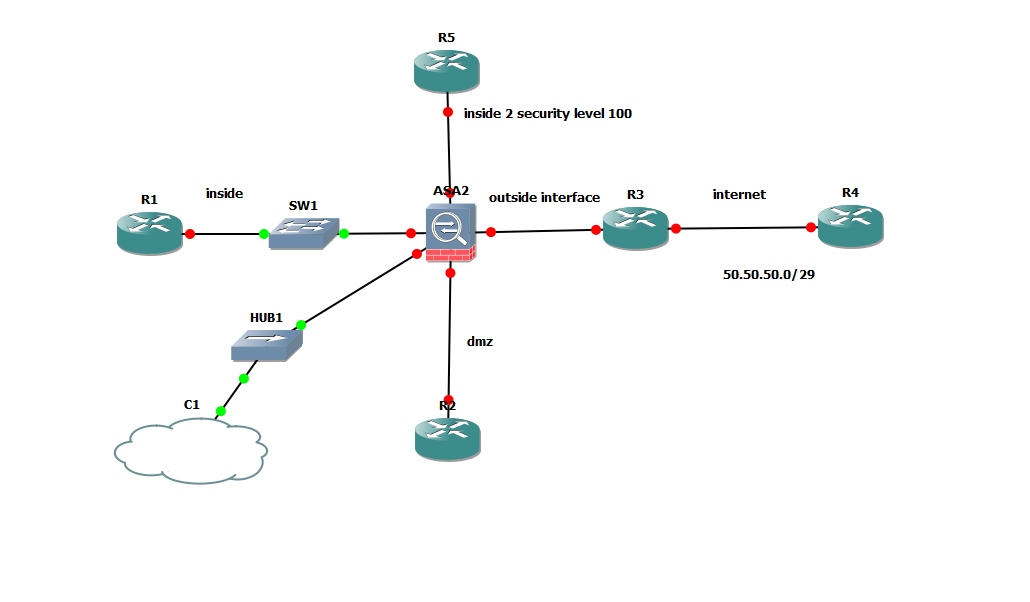
i use this for guidance but they do not provide the public address between edge router and isp ..so i am not sure what i am doing.
thanks in advance for your help!!
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2014 07:14 AM
while i am able to ping loopback addresses i can not ping any physical interfaces.have you experiences such behaviour before?
This sounds very much like a virtualization issue. Have you saved your config and tried restarting the devices?
Is the outside interface on the ASA a public IP address? From your diagram it looks like the only public IP would be on R3. In this scenario it would be R3 which does the NATing
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2014 06:01 AM
Marius thank you very much for your reply ...yes i tried everything only loopbacks are working. I use public 100.100.100.0/29 on the outside network .. i assign static nat on 4 servers and pat for the rest of the network ... edge ip addressing scheme is 50.50.50.0/30 is it possible to work this project? the connection from both inside and inside 2 to dmz and outside works perfect.i need your advice what security level i have to assign to dmvpn link ? the hub is connected with 4 branches.Anyone experienced this situation before ? any kind of improvement and recommendation is highly welcoming. To inform you all traffic from branches will pass throught the firewall for monitoring . so i think there is no need for nat on dmvpn right ?thanks in advance!!

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2014 07:11 AM
When you say only loopbacks are working, how are you testing? where are you pinging from and to?
As for the security level on the DMVPN link that really depends on what is connected there. Normally I would say it should be lower than inside and inside2 but higher than dmz and outside. But keep in mind that the security level is only in effect if there are no ACLs configured on the interface. If you configure ACLs for the interface then the security level is really just a representation of how secure that link is considered.
Anyone experienced this situation before
not sure what you mean by "this situation".
You would need to be more specific on exactly what you are trying to accomplish with this design so that we can come with suggestions to improvements and recommendations.
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2014 09:18 AM
When you say only loopbacks are working, how are you testing? where are you pinging from and to?
As for the security level on the DMVPN link that really depends on what is connected there. Normally I would say it should be lower than inside and inside2 but higher than dmz and outside. But keep in mind that the security level is only in effect if there are no ACLs configured on the interface. If you configure ACLs for the interface then the security level is really just a representation of how secure that link is considered.
not sure what you mean by "this situation".
You would need to be more specific on exactly what you are trying to accomplish with this design so that we can come with suggestions to improvements and recommendations.
Thanks for the reply Marius ,
I know it is frustrating but i am pulling my hair two days now because i am not so familiar with ASA , I know the concept with acls on interfaces .I have congigured loopback everywhere but tested with packet tracer connections are ok .pinging loopbacks are ok but no with physical interfaces.Ok let me explain you the whole project .. in the following design i have 3 branches connected to dmvpn hub which is part of ASA's branch. Branches have private addressing 172.16.0.0/24,172.16.64.0/24 etc .Although these branches are connected to internet directly the customer wants all traffic from branches goes through ASA's branch and then they will be able to access the internet.Another thing is that branches will not have any access to leased line network .All branches should have access to dmz area and internet for services like http ,https.Rmote customers have to be able to access to dmz area .So what i have done so far , i have configured dmvpn but it is not connected yet to ASA's branch.so my first question is how i am going to treat this traffic ? dmvpn hub is connected to ASA.I have configured remote ipsec vpn on ASA for remote users with different private address that i am using .The outside has public network 200.200.200.0/29 and the edge router 50.50.50.0/30 network .I did not want to do nat on edge because it seemed so complex.i hope that this information help you out Marius .if you need more details please do not hesitate to contact .
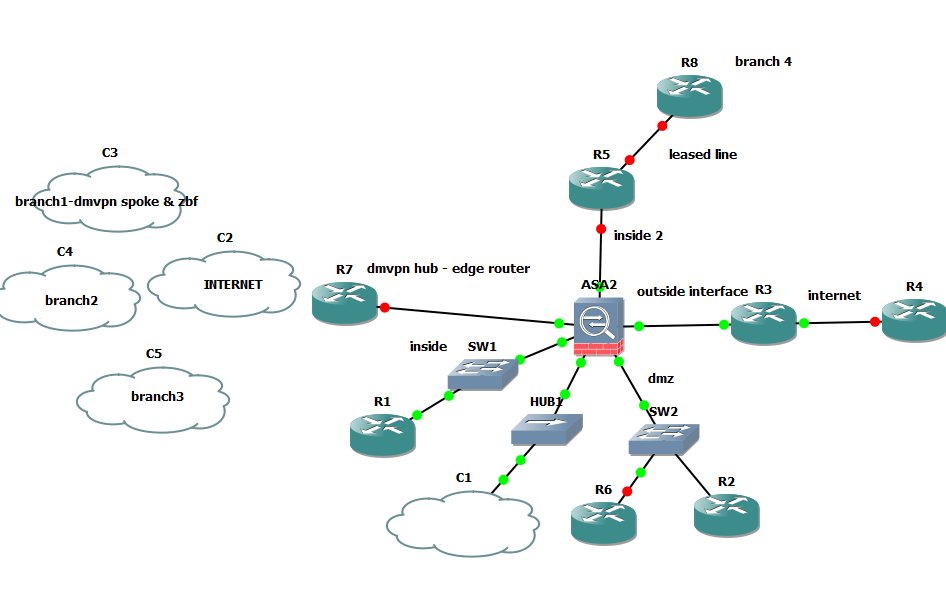
Thanks again for your time!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2014 10:33 AM
I notice in your diagram that the DMVPN hub is also connected to the internet, but R3 is also connected to the internet? Which internet connection do you want the branch offices to use?. The easiest setup would be if they used the internet connection connected to R3.
If it doesn't connect to the internet then NAT is not required.
The hub has a static public IP though, correct?
As for the ASA you would need routing to each spoke pointing out the interface that connects to the hub router.
Is this testing of a design that will be implemented or is this for theoretical purposes?
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2014 02:11 AM
I notice in your diagram that the DMVPN hub is also connected to the internet, but R3 is also connected to the internet? Which internet connection do you want the branch offices to use?. The easiest setup would be if they used the internet connection connected to R3.
If it doesn't connect to the internet then NAT is not required.
The hub has a static public IP though, correct?
As for the ASA you would need routing to each spoke pointing out the interface that connects to the hub router.
Is this testing of a design that will be implemented or is this for theoretical purposes?
Goodmorning Marius, yes hub has a public address as well ...all branches running eigrp except for the one connected via leased line .The whole project is just for theoritical purposes ,no real enviroment..the main goal is to provide the highest and versatile security across the network .So all traffic will traverse dmvpn and will end up crossing the ASA.So it would be great to have your thoughts on this design concering security.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2014 10:35 AM
from one of your earlier post:
Although these branches are connected to internet directly the customer wants all traffic from branches goes through ASA's branch and then they will be able to access the internet
For internet traffic from all branches to pass through the ASA, the hub router would need to have a default gateway pointing to the ASA and the ASA has a default gateway pointing to R3. Then you would need the eigrp process on the hub to announce it is the default gateway. This would mean you would need to remove the default gateway form the branch offices and replace them with static routes to the Hub. You could also accomplish this by setting a default route to the GRE tunnel interface on the hub.
Because of the way DMVPN works traffic between the Branch offices will not pass through the ASA. This is because a direct tunnel is established between the spokes.
So, If you want even the branch to branch traffic to pass through a firewall, you would need to set up a firewall at each location.
Other than that, you would need to configure specific rules on the ASA allowing only the subnets and ports you define to be able to access between the different areas in the network...this could become quite time consuming depending on how many subnets you have and how restrictive traffic between subnets should be.
--
Please remember to rate and select a correct answer
Please remember to select a correct answer and rate helpful posts
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:


