- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA certificates
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA certificates
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2021 05:49 AM
Hi All
When adding certificates to the ASA for anyconnect access, how come we need to add the cert of the Root CA on there?
what is that used for here?
I normally add the identity cert as well as the Root.
Cheers
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2021 07:37 AM
You need CA certificate for FQDN
here is the steps :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2021 10:44 AM
We add the issuing root CA certificate (and - recommended - intermediate CA certificates) so that the ASA itself and any clients can verify a complete chain of trust for the ASA's certificate. Some auditors and third party checkers (like Qualys) will tell you your ASA is less secure if you don't present the entire chain to a connecting client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2021 12:19 PM
Client-ASA
SSL use cert to make client auth the ASA and ASA auth the client.
so ASA have it is identity cert.
Now if client send cert to ASA how the ASA know that this cert is valid or not?
hmm
it need CA cert, but why?
simply the CA cert contain public CA key, when ASA receive the client cert there is digital signature in end of cert which is type of hash process, and this hash process use private key of CA.
note:- any hash use private key we can use public key to valid it, reverse process.
NOW the ASA has CA public and it receive the client cert,
it use public key of CA to check digital signature "hash" it valid or not.
that why we need CA cert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2021 12:41 PM - edited 01-07-2021 12:43 PM
Hi
so what certificate would the client present ?
also does the ASA need to talk to the CA?
Can you break it down in a process, I.e when the client connects what exactly happens ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2021 02:12 PM
client
CA cert
user cert
ASA
CA cert
identity cert
ASA-CA server no need in this case because as I thing you use copy paste
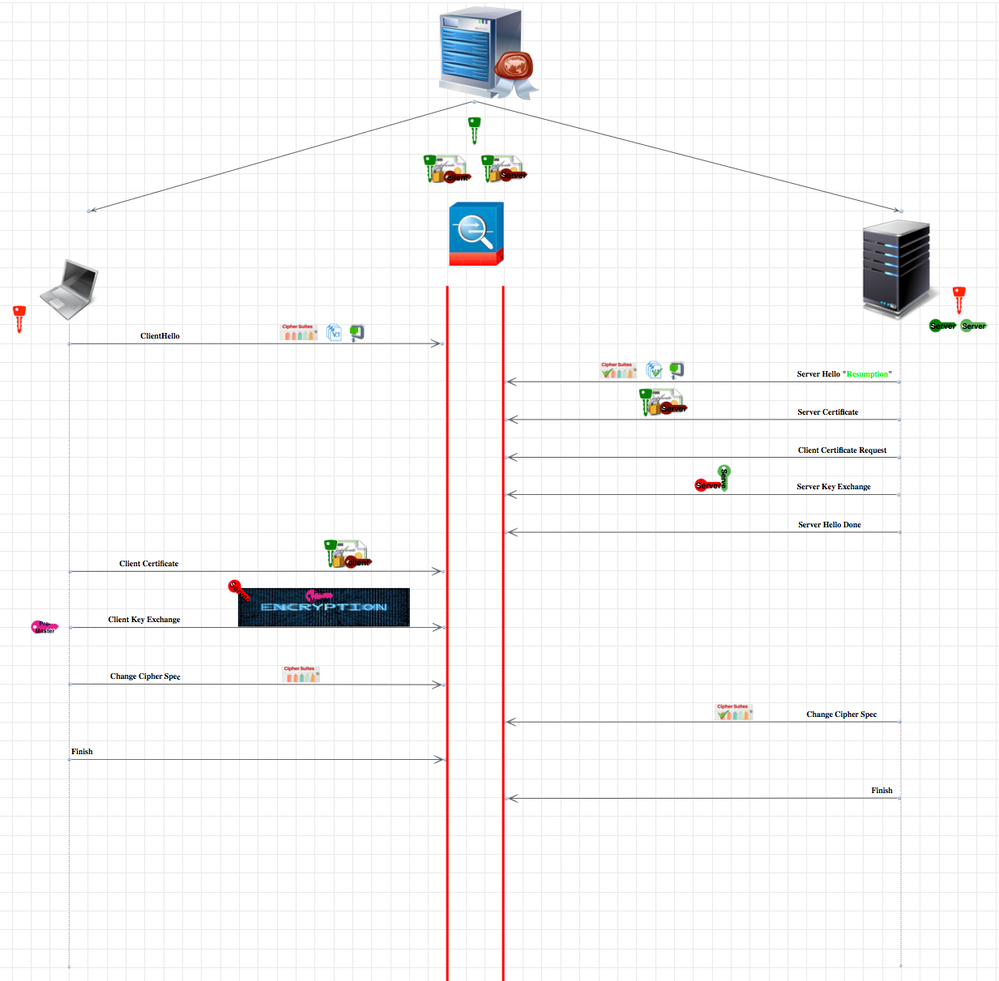
what exactly happened see below photo, any connect use SSL and this is general for all SSL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2021 08:38 AM
Hi there
In my case, we do not use certificate based authentication for our VPN, we just put a certificate on our ASA so when we connnect to it the clients trust it.
In this case how does it work? do we still need the CA and Identity cert on our ASA?
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2021 10:13 AM
You don't strictly require the root (or issuing in case an intermediate CA issued the certificate) CA certificate but it's a best practice.
The certificate on your ASA used for the VPN clients IS an identity cert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2021 12:24 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2021 09:14 PM
I think I misunderstood the original question.
When the CLIENT is authenticating using a certificate, the ASA needs to know that it can trust that certificate. The way it does so is by examining the certificate presented by the client to ascertain the issuing root CA. Only if it trusts the issuing root CA does it accept the client's certificate as trusted for authentication purposes. An ASA by default doesn't trust any third party root CAs, thus we need to add them onto the ASA.
Clients themselves don't usually have this problem when connecting to the ASA (assuming you've used a well-known public CA for your ASA identity certificate) since they rely on the operating system Trusted Root CA store which is updated by the OS vendor (Microsoft, Apple etc.) to include the most public CAs.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: