- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA connected to 3750x (Layer 3 Switch) Internet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2021 12:44 PM
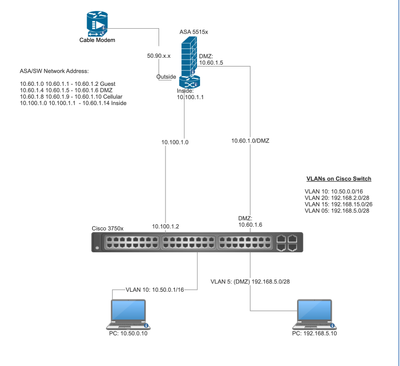
I have an ASA 5515x connected to a Layer 3 (3750x) switch with multiple interfaces (Inside, DMZ, Cellular, Guest) and a connection to a 3750 where I have VLANs, and IP Routing enabled.
Not to be able to reach the internet from any of these VLANs. I'm able to ping back and forth from ASA to Switch and vice-versa (Interfaces). I'm unable to ping the ASA interface from Workstation (192.168.5.10). I'm convinced there's a route missing from the switch or access-list from the ASA.
ASA Routes
S* 0.0.0.0 0.0.0.0 [1/0] via 172.16.0.1, outside
S 10.50.0.0 255.255.0.0 [1/0] via 10.100.1.2, inside
C 10.60.1.0 255.255.255.252 is directly connected, Guest-Network
L 10.60.1.1 255.255.255.255 is directly connected, Guest-Network
C 10.60.1.4 255.255.255.252 is directly connected, DMZ
L 10.60.1.5 255.255.255.255 is directly connected, DMZ
C 10.100.1.0 255.255.255.248 is directly connected, inside
L 10.100.1.1 255.255.255.255 is directly connected, inside
C 172.16.0.0 255.255.255.0 is directly connected, outside
L 172.16.0.156 255.255.255.255 is directly connected, outside
S 192.168.5.0 255.255.255.240 [1/0] via 10.60.1.6, DMZ
S 192.168.15.0 255.255.255.255 [1/0] via 10.60.1.2, Guest-Network
Switch Routes
ip route 0.0.0.0 0.0.0.0 10.100.1.1
ip route 0.0.0.0 0.0.0.0 10.60.1.5
ip route 0.0.0.0 0.0.0.0 10.60.1.1
ip route 0.0.0.0 0.0.0.0 10.60.1.9
ip route 10.50.0.0 255.255.0.0 10.100.1.1
ip route 192.168.2.0 255.255.255.240 10.60.1.9
ip route 192.168.5.0 255.255.255.240 10.60.1.5
ip route 192.168.15.0 255.255.255.240 10.60.1.1
I've included the network diagram and configs for both devices.
Thank you in advance.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2021 06:07 AM
please share the output of Swtich interfaces.
!
show ip interface brief | ex unassigned
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2021 01:45 PM
Hi to fix the issue. on ASA define these route.
ASA route inside 10.50.0.0 255.255.0.0 10.100.1.2 route inside 192.168.5.0 255.255.255.240 10.100.1.2 route inside 192.168.15.0 255.255.255.255 10.100.1.2
On switches only one default route is required
SW ip route 0.0.0.0 0.0.0.0 10.100.1.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2021 11:44 PM - edited 03-05-2021 11:59 PM
change your nat rules. the seem you can not connect or ping to outside is due to your existing nat rule the configured nat rule you have is
object network LAN subnet 10.50.0.0 255.255.0.0 nat (any,outside) dynamic interface
this above nat rule means only traffic comming from subnet 10.20.0.0 however even though you configured "any" in your nat statement.
you need to put a new nat rule in section one which would be allow any subnet in your network to go out to internet.
nat (any,outside) source dynamic any interface
once apply this rule do a packet tracer and check the connectivity if you can reach/ping 8.8.8.8.
Your routing look ok.can you ping from 192.168.5.10 to VLAN-5 192.168.5.1 also from SW can you ping to 10.60.1.5
ping 10.60.1.5 source vlan 5
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2021 05:23 AM - edited 03-06-2021 05:25 AM
Thank you for your reply and help. I added the command and now my NAT looks like this. However, I'm unable to connect or ping the internet from the VLANs.
nat (any,outside) source dynamic any interface
!
nat (inside,outside) after-auto source dynamic any interface inactive
I've attached a packet tracer screenshot.
Yes, from the DMZ WKSTN (192.168.5.10), I'm able to ping VLAN-5 192.168.5.1, 10.60.1.6, and 10.60.1.5 (ASA Interface). This is a correction, I just realized last night that I'm able to ping 10.60.1.5. So, I'm able to ping all the ASA Interfaces from the proper VLANs. Just can't get out to the internet from the VLANs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2021 05:49 AM
show/run these commands and share the output.
show run nat
show nat detail
!
packet-tracer input DMZ tcp 192.1268.5.10 ssh 8.8.8.8 443 detail
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2021 05:58 AM
These are the result. FYI. for now I have the Outside Interface connected to another port off my cable modem for Internet access until I get this to work.
Result of the command: "show run nat"
nat (any,outside) source dynamic any interface
!
nat (inside,outside) after-auto source dynamic any interface inactive
Result of the command: "show nat detail"
Manual NAT Policies (Section 1)
1 (any) to (outside) source dynamic any interface
translate_hits = 3168, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 172.16.0.156/24
Manual NAT Policies (Section 3)
1 (inside) to (outside) source dynamic any interface inactive
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: 172.16.0.156/24
packet-tracer input DMZ tcp 192.168.5.10 ssh 8.8.8.8 443 detail
Result of the command: "packet-tracer input DMZ tcp 192.168.5.10 ssh 8.8.8.8 443 detail"
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 172.16.0.1 using egress ifc outside
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group DMZ_access_in in interface DMZ
access-list DMZ_access_in extended permit ip any any
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f844b0cc7c0, priority=13, domain=permit, deny=false
hits=2464, user_data=0x7f8441021a00, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=DMZ, output_ifc=any
Phase: 3
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (any,outside) source dynamic any interface
Additional Information:
Dynamic translate 192.168.5.10/22 to 172.16.0.156/167
Forward Flow based lookup yields rule:
in id=0x7f844b9fcd80, priority=6, domain=nat, deny=false
hits=3211, user_data=0x7f844b092130, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=outside
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f844a278d90, priority=0, domain=nat-per-session, deny=false
hits=715, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f844af5d8b0, priority=0, domain=inspect-ip-options, deny=true
hits=2473, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=DMZ, output_ifc=any
Phase: 6
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (any,outside) source dynamic any interface
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7f844a28c9a0, priority=6, domain=nat-reverse, deny=false
hits=3189, user_data=0x7f844b07fd60, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=outside
Phase: 7
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7f844a278d90, priority=0, domain=nat-per-session, deny=false
hits=717, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 8
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7f844ae93d10, priority=0, domain=inspect-ip-options, deny=true
hits=3854, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=outside, output_ifc=any
Phase: 9
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 3710, packet dispatched to next module
Module information for forward flow ...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_tcp_normalizer
snp_fp_translate
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Module information for reverse flow ...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_translate
snp_fp_tcp_normalizer
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Result:
input-interface: DMZ
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2021 06:54 AM
ok from the ASA you have access to internet as this has proven from packet tracer. can you ping from swtich with source vlan x. and do this sucessful. or if you ping 8.8.8.8 on the switch what does it show you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2021 07:21 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2021 02:48 AM
can you confirm you can ping from your firewall to ip 8.8.8.8
can you confirm if you can ping from switch to firewall
can you confirm if you can ping from firewall to swtich
earlier you send packet tracer output it shows your asa have a reachability to internet. what you means "FYI. for now I have the Outside Interface connected to another port off my cable modem for Internet access until I get this to work."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2021 05:24 AM
Yes, I'm able to ping the Firewall from the Switch and Switch from the Firewall.
----------
Ping Switch from Firewall
Home-5515x-Router# ping 10.60.1.6
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.60.1.6, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/10 ms
Home-5515x-Router# ping 10.60.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.60.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/10 ms
Home-5515x-Router# ping 10.100.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.100.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Yes, able to ping the Internet from Firewall
Home-5515x-Router# ping 8.8.8.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/16/20 ms
---------------------------
Ping Firewall from Switch
CiscoHomeSwitch#ping 10.60.1.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.60.1.5, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/7/25 ms
CiscoHomeSwitch#ping 10.60.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.60.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/9 ms
CiscoHomeSwitch#ping 10.100.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.100.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/9 ms
CiscoHomeSwitch#
---------------------
What I meant is this. Since I do not have Firewall/Switch properly configured for internet access, I temporarily have the Firewall (outside interface) connected to my modem cable to get out to the internet. That's the reason you see the Outside interface has a private IP address (172.16.0.156). Hope this makes sense to you.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2021 05:56 AM
"What I meant is this. Since I do not have Firewall/Switch properly configured for internet access, I temporarily have the Firewall (outside interface) connected to my modem cable to get out to the internet. That's the reason you see the Outside interface has a private IP address (172.16.0.156). Hope this makes sense to you."
- Ok From Firewall you can ping the SVI on the swtich and frome Switch SVI you can ping the firewall interface ip address/es. you can also ping to 8.8.8.8 from Firewall. could you also confirm if you can ping from the swtich SVI to 8.8.8.8 please.
other think you have plan to decommision your cable router and directily plug in ISP (broadband) cable to you ASA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2021 07:39 AM
- Ok From Firewall you can ping the SVI on the swtich and frome Switch SVI you can ping the firewall interface ip address/es. you can also ping to 8.8.8.8 from Firewall. could you also confirm if you can ping from the swtich SVI to 8.8.8.8 please.
Yes, I can ping SVI (10.60.1.6) from the firewall.
Home-5515x-Router# ping 10.60.1.6
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.60.1.6, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/20 ms
"other think you have plan to decommision your cable router and directily plug in ISP (broadband) cable to you ASA?"
I had it set up that way before and it didn't work. I can try it again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2021 06:01 AM
Just out of curiosity, I connected my laptop to the ASA Inside interface and assigned it an IP 10.100.1.5, 255.255.0.0, 10.100.1.1. I was very surprised that I was ABLE to access the Internet. So the network 10.100.1.0 is routed properly to the Internet. It seems as though the switch VLAN networks aren't getting routed.
These are the routes on the Switch. Is that properly configured? In fact, do I need both routes for each VLAN?
ip route 0.0.0.0 0.0.0.0 10.100.1.1
ip route 0.0.0.0 0.0.0.0 10.60.1.5
ip route 0.0.0.0 0.0.0.0 10.60.1.1
ip route 0.0.0.0 0.0.0.0 10.60.1.9
ip route 10.50.0.0 255.255.0.0 10.100.1.1
ip route 192.168.2.0 255.255.255.240 10.60.1.9
ip route 192.168.5.0 255.255.255.240 10.60.1.5
ip route 192.168.15.0 255.255.255.240 10.60.1.1
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2021 06:07 AM
please share the output of Swtich interfaces.
!
show ip interface brief | ex unassigned
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2021 06:28 AM
This is the "show ip interface brief "
Also, I'm able to ping the VLAN Interfaces from the ASA.
Home-5515x-Router# ping 192.168.5.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.5.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/10 ms
Home-5515x-Router# ping 10.50.0.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.50.0.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/8/20 ms
Home-5515x-Router#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2021 01:45 PM
Hi to fix the issue. on ASA define these route.
ASA route inside 10.50.0.0 255.255.0.0 10.100.1.2 route inside 192.168.5.0 255.255.255.240 10.100.1.2 route inside 192.168.15.0 255.255.255.255 10.100.1.2
On switches only one default route is required
SW ip route 0.0.0.0 0.0.0.0 10.100.1.1
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide