- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA/Firepower failover and Redundant Interface
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2021 11:17 PM
Hi ,
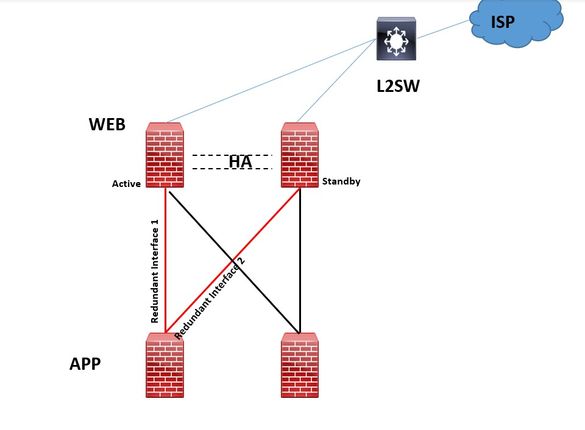
i would like to ask about redundant interfaces.
As per below reference,
Cisco explain how to design and configure redundant link.So i consider the HA design without using switch between firewalls.
i create redundant interface on DB tier firewall to connect to APP tier firewall. I aslo create redundant interface on APP tier firewall to connect web tier firewall. Link monitor for HA in Web tier is WAN and LAN interface. Link monitor for HA setup in application tier is LAN interface. Link monitor for HA setup in DB tier is WAN and LAN interface
Please see the blew picture.
I only worry reason is the firewall redundant interfaces are directly connected to upper layer firewall interfaces without connect to switch .
So let me know the HA and redundancy interfaces will work properly without using switch ?
Please let me know any concern on my design ?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2021 01:20 AM
Yes, this: "if Active firewall go down redundant interface1 of APP firewall is still active and redundant interface 2 never take over active".
Putting a switch (or pair of switches in a stack or VSS or Nexus with VPC etc) between the firewalls is the normal solution (95% plus of deployments). You can use Etherchannels as well to add resiliency (and potentially increase throughput).
No matter what layers or redundancy you build in there are always some possible failure conditions that could interrupt service. The key is to balance the redundancy elements with their added complexity and put in enough to have done due diligence but not so much as to make the complexity and cost outweigh the added availability protection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2021 05:22 AM
We almost never see redundant interfaces in production because they have limited utility. Personally I have worked on well over 1000 ASAs and never seen it in use.
A redundant interface provides a very limited additional level of availability for a given interface. The presumption is that both interface would connect to the same upstream device - i.e. normally a switch. Connecting to separate upstream firewalls would result in very erratic and unpredictable behavior. Consider what happens if your upstream firewall does a failover and your active interface is now connected to the standby upstream firewall. You lose upstream connectivity altogether.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2021 11:50 PM
Hi @Marvin Rhoads ,
Do you mean,as per below diagram,if Active firewall go down redundant interface1 of APP firewall is still active and redundant interface 2 never take over active ? Or do you mean redundant interface priority election process is very complicated if upstream are connected to different devices ?
Or can I use etherchannel to solve this ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2021 01:20 AM
Yes, this: "if Active firewall go down redundant interface1 of APP firewall is still active and redundant interface 2 never take over active".
Putting a switch (or pair of switches in a stack or VSS or Nexus with VPC etc) between the firewalls is the normal solution (95% plus of deployments). You can use Etherchannels as well to add resiliency (and potentially increase throughput).
No matter what layers or redundancy you build in there are always some possible failure conditions that could interrupt service. The key is to balance the redundancy elements with their added complexity and put in enough to have done due diligence but not so much as to make the complexity and cost outweigh the added availability protection.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide