- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA pass-through L2TP ipsec to dmz
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA pass-through L2TP ipsec to dmz
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2020 12:37 AM - edited 11-15-2020 12:41 AM
Hi
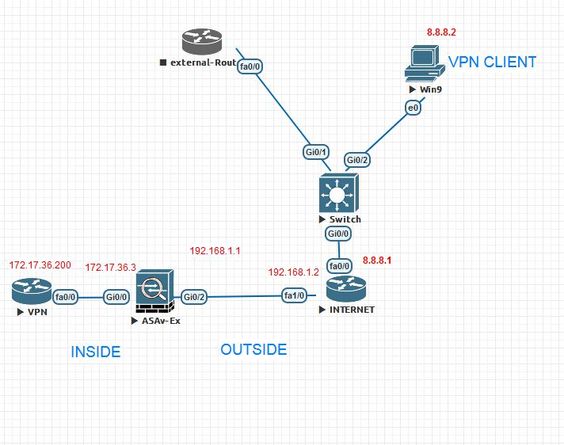
we have VPN server( Router l2tp ipsec ) on the DMZ interface, and i have asa in edge . we want to allow vpn l2tp ipsec traffic to pass through outside to Dmz
my ASA sample config for allow ipsec traffic from outside to dmz:
object network vpn-router
host 192.168.1.200
nat (dmz,outside) static *.*.*.* (public ip address )
access-list outside-to-in extended permit ip any any ( for test , i allow all traffic to in )
access-group outside-to-in in interface outside
access-list mpf extended permite udp any any 4500
access-list mpf extended permite udp any any 500
access-list mpf extended permite esp any any
access-list mpf extended permite ah any any
class-map mpf-class
match access-list mpf
policy-map global_policy
class mpf-class
inspect ipsec-pass-thru
service-policy global_policy global
BUT :
NO any vpn clients connect from outside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2020 02:54 AM
High level as per the Outside to DMZ concern ok, what is the error you get?
Do you have ACL also from DMZ to Inside? - since we do not see that config, or post-show run full config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2020 04:21 AM
i can telnet/ssh/http from outside client to vpn router in inside , but l2tp vpn not work
and router L2TP config is ok , i test it from inside pc
----------
ASA packet tracer and show run :
--------------- packet tracer
External(config)# packet-tracer input outside udp 8.8.8.2 isakmp 172.17.36.200 isakmp
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 172.17.36.200 using egress ifc INSIDE
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside in interface OUTSIDE
access-list outside extended permit ip any any
Additional Information:
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map class-ipsec
match access-list ipsec
policy-map global_policy
class class-ipsec
inspect ipsec-pass-thru _default_ipsec_passthru_map
service-policy global_policy global
Additional Information:
Phase: 6
Type: QOS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: NAT
Subtype: rpf-check
Result: DROP
Config:
object network vpn
nat (INSIDE,OUTSIDE) static interface
Additional Information:
Result:
output-interface: INSIDE
output-status: up
output-line-status: up
Action: drop
------------------- show run
-----------------------------
External(config)#
External(config)# SH RUN
: Saved
:
: Serial Number: 9ANXTECUDUT
: Hardware: ASAv, 2048 MB RAM, CPU Pentium II 2261 MHz
:
ASA Version 9.5(2)204
!
hostname External
enable password N7FecZuSHJlVZC2P encrypted
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
names
!
interface GigabitEthernet0/0
nameif INSIDE
security-level 100
ip address 172.17.36.3 255.255.255.0
!
interface GigabitEthernet0/1
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/2
nameif OUTSIDE
security-level 2
ip address 192.168.1.1 255.255.255.0
!
interface Management0/0
nameif MNG
security-level 100
ip address 192.168.45.88 255.255.255.0
!
ftp mode passive
object network vpn
host 172.17.36.200
access-list inside extended permit ip any any
access-list outside extended permit ip any any
access-list ipsec extended permit udp any any eq isakmp
access-list ipsec extended permit udp any any eq 4500
access-list ipsec extended permit esp any any
access-list ipsec extended permit gre any any
access-list ipsec extended permit ah any any
access-list ipsec extended permit tcp any any eq 1701
access-list ipsec extended permit tcp any any eq pptp
access-list ipsec extended permit tcp any any eq 1703
access-list ipsec extended permit udp any any eq 1703
access-list ipsec extended permit udp any any eq 1701
access-list ipsec extended permit udp any any eq 1723
pager lines 23
logging enable
logging asdm informational
mtu INSIDE 1500
mtu OUTSIDE 1500
mtu MNG 1500
no failover
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
!
object network vpn
nat (INSIDE,OUTSIDE) static interface
access-group inside in interface INSIDE
access-group outside in interface OUTSIDE
route OUTSIDE 0.0.0.0 0.0.0.0 192.168.1.2 1
route INSIDE 172.17.36.0 255.255.255.0 172.18.50.32 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication http console LOCAL
aaa authentication enable console LOCAL
http server enable
http 192.168.45.0 255.255.255.0 MNG
no snmp-server location
no snmp-server contact
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpool policy
auto-import
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.45.0 255.255.255.0 MNG
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
dynamic-access-policy-record DfltAccessPolicy
username test password P4ttSyrm33SV8TYp encrypted
!
class-map inspection_default
match default-inspection-traffic
class-map class-ipsec
match access-list ipsec
!
!
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns migrated_dns_map_1
inspect ftp
inspect h323 h225
inspect h323 ras
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
inspect icmp
class class-ipsec
inspect ipsec-pass-thru
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
profile License
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination transport-method http
Cryptochecksum:fbd681c44817b87053ed0af7113d2c8d
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-15-2020 09:38 AM
DO you have public ip other than the outside of ASA,
make NAT static inside outside to this public IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2020 01:41 AM
for test , i check with another public ip in static NAT
object network vpn
nat (INSIDE,OUTSIDE) static 192.168.1.8
but , Not Work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2020 03:58 PM
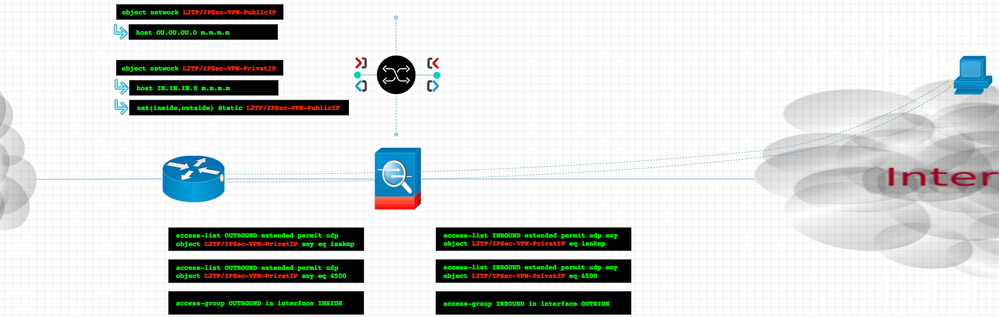
I make this NAT and access list please make review and config ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2020 05:12 AM
thanks for reply .
But it is not work .
--------------- packet tracer
External(config)# packet-tracer input outside udp 8.8.8.2 isakmp 172.17.36.200 isakmp
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 172.17.36.200 using egress ifc INSIDE
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside in interface OUTSIDE
access-list outside extended permit ip any any
Additional Information:
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map class-ipsec
match access-list ipsec
policy-map global_policy
class class-ipsec
inspect ipsec-pass-thru _default_ipsec_passthru_map
service-policy global_policy global
Additional Information:
Phase: 6
Type: QOS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: NAT
Subtype: rpf-check
Result: DROP
Config:
object network vpn
nat (INSIDE,OUTSIDE) static interface
Additional Information:
Result:
output-interface: INSIDE
output-status: up
output-line-status: up
Action: drop
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2020 06:22 AM - edited 11-30-2020 02:42 PM
Any update friend
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2020 12:34 AM
Unfortunately none of the tips worked
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2020 04:15 AM
I read about this pass through,
so can you check the following
1- use real client outside asa not use packet tracer
2- config
inspect ipsec pass thru
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: