- Cisco Community
- Technology and Support
- Security
- Network Security
- ASA unable to access internet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2013 02:03 PM - edited 03-11-2019 06:59 PM
hello,
first of all, sorry for my bad english. actually i'm french and above all an absolute beginner in ASA Cisco
i'm trying to install a Cisco ASA 5505 for a client and it's impossible to access to internet (in fact, the original subject is about creating an IPsec site-to-site VPN, but I can not even access internet so...)
Below my setup
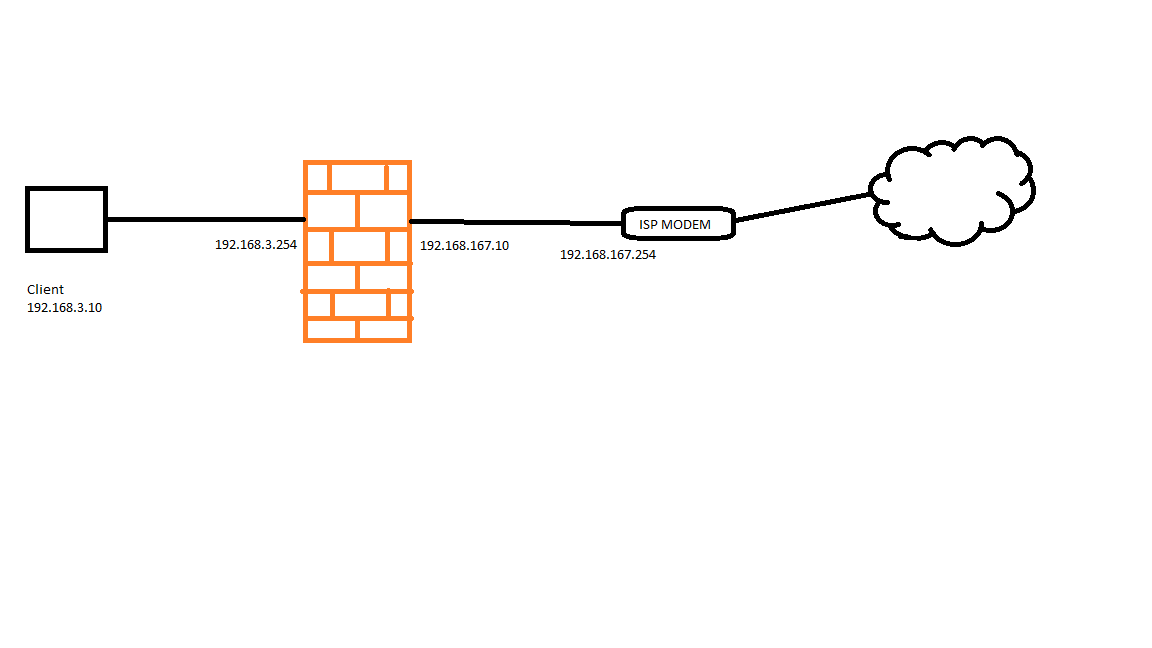
From my client I cannot ping the outside interface, but I think it's normal.
From the firewall, I can ping the ISP Modem and Google DNS server 8.8.8.8
I configured the Asa with the wizzard tool
see below the configuration:
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.3.254 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 192.168.167.10 255.255.255.0
!
ftp mode passive
access-list inside_access_in extended permit icmp any any
access-list outside_access_in extended permit icmp any any
pager lines 24
logging asdm informational
mtu outside 1500
mtu inside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
access-group outside_access_in in interface outside
access-group inside_access_in in interface inside
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 192.168.3.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
telnet timeout 5
ssh timeout 5
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
Thank you for your help
Regards
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2013 02:16 PM
Hi,
You dont have a default route
Add this
route outside 0.0.0.0 0.0.0.0 192.168.167.254
I am not sure how your ISP modems NAT and routing is configured so you might want to configure Dynamic PAT for your LAN users on the ASA if the "route" command isnt enough.
global (outside) 1 interface
nat (inside) 1 192.168.3.0 255.255.255.0
Also your ACL only allows ICMP from the LAN. I would suggest adding the following
access-list inside_access_in permit ip 192.168.3.0 255.255.255.0 any
Also add
policy-map global_policy
class inspection_default
inspect icmp
inspect icmp error
Hope this helps
Please mark the reply as the correct answer if it answered your question.
Ask more if needed
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2013 02:16 PM
Hi,
You dont have a default route
Add this
route outside 0.0.0.0 0.0.0.0 192.168.167.254
I am not sure how your ISP modems NAT and routing is configured so you might want to configure Dynamic PAT for your LAN users on the ASA if the "route" command isnt enough.
global (outside) 1 interface
nat (inside) 1 192.168.3.0 255.255.255.0
Also your ACL only allows ICMP from the LAN. I would suggest adding the following
access-list inside_access_in permit ip 192.168.3.0 255.255.255.0 any
Also add
policy-map global_policy
class inspection_default
inspect icmp
inspect icmp error
Hope this helps
Please mark the reply as the correct answer if it answered your question.
Ask more if needed
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2013 05:51 AM
Hello!
thank you! i forgot the NAT configuration! solved!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:


