- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Cisco 2130 S2S IPsec trouble
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco 2130 S2S IPsec trouble
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 12:52 AM - edited 02-21-2020 09:40 AM
Hello everyone
I have been working with Cisco ASA's for several years. Im very used to the <crypto maps> setup for IKE1 and IKE2 tunnels on the old ASA code. Now Im working with a 2130 with version 6.5 againt ASA's with 8.4 code.
My problem now is that I have a lot of (cisco asa ipsec removing peer from correlator table failed no match) and Lost Service error messages. This is usually from wrong definition of subnets on each side.
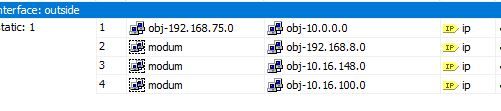
When setting up the ASA's I use the old method like this:
On the 2130 it goes like this for site A and B:
To me it seems like the definitons is somewhat wrong when using this method on the 2130. You match everything against eachother. Not subnet to subnet like the old ASA code.
Can anyone help med understand what is wrong ?
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 01:41 AM
Hi Jon,
Its simple, you need to add your subnet as NODE A and choose your firewall as device & the other end subnet as NODE B and choose EXTRANET and specify the pubic IP of other end
Lets take example:
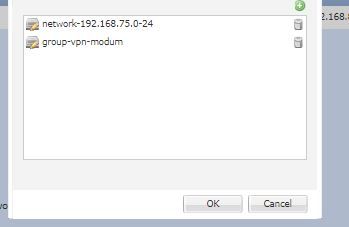
Your Organisation subnet : 192.168.10.0/24, 192.168.20.0//24
create a object group with these two subnets and add this to NODE A
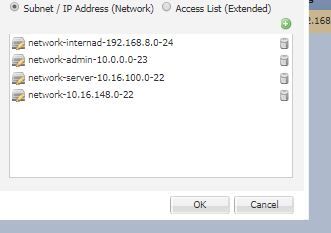
Other End Subnet: 10.10.10.0/24, 10.10.20.0/24
reate a object group with these two subnets and add this to NODE B
Then create the IKEv1 or IKEv2 polices and apply, Then create a identity nat rule for the above subnet and allow that traffic in ACP.
Hope This Helps
Abheesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 01:49 AM
If you look at the original post, you can se that this has been done. My problem is errors and that the tunnel in some cases only can be brought up from one side.
If you have a lot of subnets thrown togheter on the 2130 and you have a strict crypto map on the other side, my assumption is that problems like this can arise. Im looking into using an extended access list now. Testing with a 5506X in my office.
I would be gratefull if anyone can confirm my assumption.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 02:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 02:34 AM
Yes, NAT and ACL are all in order.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 02:45 AM
go to FTD cli and enter system support diagnostic-cli, then debug cryptomap and check y this is failing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 03:10 AM
Seems like there are larger problems with my 2130.
Ipsecs with only one subnet to other fw like checkpoint are also failing. They suddenly stalls and I have to run "clear crypto ipsec sa peer "xxxx"" to get it working again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 03:29 AM - edited 11-07-2019 03:31 AM
Please check hit count in by entering show access list command
You will get access list information from show running configuration | in cypto
Check what access list showing in this vpn and check that access list by show access list ( acl name) and you will see hit count if there is no hitcount please re add it .
2. Second option is to create extended ACL and set source destination subnet sentence as per your requirement
it is compulsory that all subnet added here which should be entered in peer end device also with same CIDR
Please check and let us know .
Regards,
Harmesh Yadav
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-07-2019 05:09 AM
Thanks for answers. I have now opened a TAC case since these errors seems to be beyond misconfiguration.
ACL, NAT, cryptos and encryption (pfs) have been checked out.
When trying to get the SA up from remote site, it comes up with "drop" on VPN (removing peer from correlator table failed, no match!) when doing the same from the 2130, the tunnel comes up with now errors on the remote site log.
All traffic passes as expected when the SA's are up. But when "idle timeout" or "Lost Service" show up, the problems restarting the SA's continues.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: