- Cisco Community
- Technology and Support
- Security
- Network Security
- Cisco ASA Static Route Lab: Unable to ping from ASA1 to ASA3
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco ASA Static Route Lab: Unable to ping from ASA1 to ASA3
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2014 12:46 AM - edited 03-11-2019 08:57 PM
Hi all,
My simple lab topology is as follows:
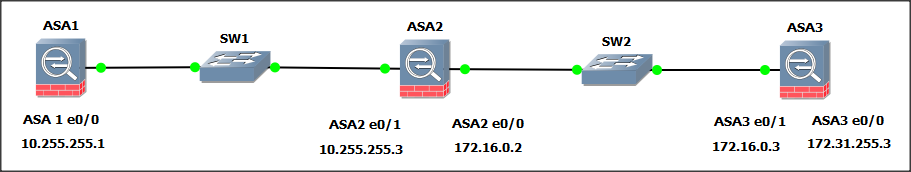
Firewall configuration is as follows:
IP Address
ASA1# sh int ip b | i CONFIG up
Ethernet0/0 10.255.255.1 YES CONFIG up up
ASA1#
ASA2(config)# sh int ip b | i CONFIG up
Ethernet0/0 172.16.0.2 YES CONFIG up up
Ethernet0/1 10.255.255.3 YES CONFIG up up
ASA2(config)#
ASA3# sh int ip b | i CONFIG up
Ethernet0/0 172.31.255.3 YES CONFIG up up
Ethernet0/1 172.16.0.3 YES CONFIG up up
ASA3#
Access-list
ASA1# sh run access-l
access-list I extended permit ip any any
access-list O extended permit ip any any
access-list c extended permit ip any host 172.16.0.3
access-list c extended permit ip host 172.16.0.3 any
ASA1#
ASA2(config)# sh run access-l
access-list I extended permit ip any any
access-list O extended permit ip any any
access-list c extended permit ip any host 172.16.0.3
access-list c extended permit ip host 172.16.0.3 any
ASA2(config)#
ASA3# sh run access-l
access-list c extended permit ip any host 172.16.0.3
access-list c extended permit ip host 172.16.0.3 any
access-list I extended permit ip any any
access-list O extended permit ip any any
ASA3#
I can ping ASA2 from ASA1 & ASA3
Unfortunately, I can’t ping ASA3 from ASA1
I’ve attached the capture log for your reference. Please let me know if you need more info in order to solve this issue.
Ping Test
ASA1# p 172.16.0.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.0.3, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
ASA1#
Packet Capture
ASA1# sh cap
capture co type raw-data access-list c packet-length 54 interface outside [Capturing - 350 bytes]
ASA1#
ASA1# sh cap co
5 packets captured
1: 00:29:42.739097 10.255.255.1 > 172.16.0.3: icmp: echo request
2: 00:29:44.742774 10.255.255.1 > 172.16.0.3: icmp: echo request
3: 00:29:46.741004 10.255.255.1 > 172.16.0.3: icmp: echo request
4: 00:29:48.749259 10.255.255.1 > 172.16.0.3: icmp: echo request
5: 00:29:50.746985 10.255.255.1 > 172.16.0.3: icmp: echo request
5 packets shown
ASA1#
ASA2(config)# sh cap
capture ci type raw-data access-list c packet-length 54 interface inside [Capturing - 350 bytes]
capture co type raw-data access-list c packet-length 54 interface outside [Capturing - 350 bytes]
ASA2(config)#
ASA2(config)#
ASA2(config)# sh cap ci
5 packets captured
1: 00:29:44.856904 10.255.255.1 > 172.16.0.3: icmp: echo request
2: 00:29:46.852830 10.255.255.1 > 172.16.0.3: icmp: echo request
3: 00:29:48.842562 10.255.255.1 > 172.16.0.3: icmp: echo request
4: 00:29:50.853334 10.255.255.1 > 172.16.0.3: icmp: echo request
5: 00:29:52.857621 10.255.255.1 > 172.16.0.3: icmp: echo request
5 packets shown
ASA2(config)#
ASA2(config)# sh cap co
5 packets captured
1: 00:29:44.856904 10.255.255.1 > 172.16.0.3: icmp: echo request
2: 00:29:46.852830 10.255.255.1 > 172.16.0.3: icmp: echo request
3: 00:29:48.842562 10.255.255.1 > 172.16.0.3: icmp: echo request
4: 00:29:50.853334 10.255.255.1 > 172.16.0.3: icmp: echo request
5: 00:29:52.857621 10.255.255.1 > 172.16.0.3: icmp: echo request
5 packets shown
ASA2(config)#
ASA3# sh cap
capture ci type raw-data access-list c packet-length 54 interface inside [Capturing - 140 bytes]
capture co type raw-data access-list c packet-length 54 interface outside [Capturing - 0 bytes]
ASA3#
ASA3#
ASA3# sh cap ci
3 packets captured
1: 00:29:51.176687 10.255.255.1 > 172.16.0.3: icmp: echo request
2: 00:29:53.176153 10.255.255.1 > 172.16.0.3: icmp: echo request
3: 00:29:55.175619 10.255.255.1 > 172.16.0.3: icmp: echo request
3 packets shown
ASA3#
Packet Tracer
ASA1# packet-tracer input outside icmp 10.255.255.1 8 0 172.16.0.3 detailed
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd5a64450, priority=12, domain=capture, deny=false
hits=1, user_data=0xd8344970, cs_id=0x0, l3_type=0x0
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0000.0000.0000
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd8643a20, priority=1, domain=permit, deny=false
hits=11, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0000.0000.0000
Phase: 3
Type: FLOW-LOOKUP
Subtype:
Result: ALLOW
Config:
Additional Information:
Found no matching flow, creating a new flow
Phase: 4
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 0.0.0.0 0.0.0.0 outside
Phase: 5
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd868bf20, priority=500, domain=permit, deny=true
hits=1, user_data=0x6, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip=10.255.255.1, mask=255.255.255.255, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
ASA1#
ASA2# packet-tracer input inside icmp 10.255.255.1 8 0 172.16.0.3 detailed
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd5a652e8, priority=12, domain=capture, deny=false
hits=11, user_data=0xd83424c8, cs_id=0x0, l3_type=0x0
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0000.0000.0000
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd86a5938, priority=1, domain=permit, deny=false
hits=26, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0000.0000.0000
Phase: 3
Type: FLOW-LOOKUP
Subtype:
Result: ALLOW
Config:
Additional Information:
Found no matching flow, creating a new flow
Phase: 4
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 172.16.0.0 255.255.0.0 outside
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd86a8d90, priority=0, domain=permit-ip-option, deny=true
hits=8, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0
Phase: 6
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd86aa9f0, priority=66, domain=inspect-icmp-error, deny=false
hits=7, user_data=0xd86aa920, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0
Phase: 7
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd89caba0, priority=12, domain=capture, deny=false
hits=12, user_data=0xd83424c8, cs_id=0xd5a65248, reverse, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=172.16.0.3, mask=255.255.255.255, port=0
Phase: 8
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
out id=0xd8a4efb8, priority=12, domain=capture, deny=false
hits=5, user_data=0xd8923a28, cs_id=0xd89cda08, reverse, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=172.16.0.3, mask=255.255.255.255, port=0
Phase: 9
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 10, packet dispatched to next module
Module information for forward flow ...
snp_fp_inspect_ip_options
snp_fp_adjacency
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Module information for reverse flow ...
Phase: 10
Type: ROUTE-LOOKUP
Subtype: output and adjacency
Result: ALLOW
Config:
Additional Information:
found next-hop 172.16.0.3 using egress ifc outside
adjacency Active
next-hop mac address 00ab.10be.8701 hits 1
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: allow
ASA2#
ASA3# packet-tracer input inside icmp 10.255.255.1 8 0 172.16.0.3 detailed
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd5a654f8, priority=12, domain=capture, deny=false
hits=5, user_data=0xd83431f0, cs_id=0x0, l3_type=0x0
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0000.0000.0000
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd86a5938, priority=1, domain=permit, deny=false
hits=15, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0000.0000.0000
Phase: 3
Type: FLOW-LOOKUP
Subtype:
Result: ALLOW
Config:
Additional Information:
Found no matching flow, creating a new flow
Phase: 4
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 172.16.0.3 255.255.255.255 identity
Phase: 5
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd86a7718, priority=112, domain=permit, deny=false
hits=5, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=1
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd86a8d90, priority=0, domain=permit-ip-option, deny=true
hits=5, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0
Phase: 7
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd86a7cb8, priority=66, domain=inspect-icmp, deny=false
hits=3, user_data=0xd86a7be8, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0
Phase: 8
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd86aa9f0, priority=66, domain=inspect-icmp-error, deny=false
hits=3, user_data=0xd86aa920, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0
Phase: 9
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd89c0a98, priority=12, domain=capture, deny=false
hits=6, user_data=0xd83431f0, cs_id=0xd5a65de0, reverse, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=172.16.0.3, mask=255.255.255.255, port=0
Phase: 10
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
out id=0xd89c2970, priority=12, domain=capture, deny=false
hits=0, user_data=0xd83431f0, cs_id=0xd5a65de0, reverse, flags=0x0, protocol=0
src ip=172.16.0.3, mask=255.255.255.255, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0
Phase: 11
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 5, packet dispatched to next module
Module information for forward flow ...
snp_fp_inspect_ip_options
snp_fp_inspect_icmp
snp_fp_adjacency
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Module information for reverse flow ...
snp_fp_inspect_ip_options
snp_fp_inspect_icmp
snp_fp_adjacency
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Phase: 12
Type: ROUTE-LOOKUP
Subtype: output and adjacency
Result: ALLOW
Config:
Additional Information:
found next-hop 0.0.0.0 using egress ifc identity
adjacency Active
next-hop mac address 0000.0000.0000 hits 15
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
output-status: up
output-line-status: up
Action: allow
ASA3#
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2014 08:13 AM
Difficult to say without knowing how you have configured the firewalls eg.
1) what are the security levels of the interfaces on ASA2
2) if they are the same are you allowing same security traffic
3) do you have NAT setup or no NAT
4) what routes do you have in place
etc.
Jon
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
