- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Cisco FMC URL Policy Issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco FMC URL Policy Issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2020 07:51 AM - edited 02-21-2020 09:52 AM
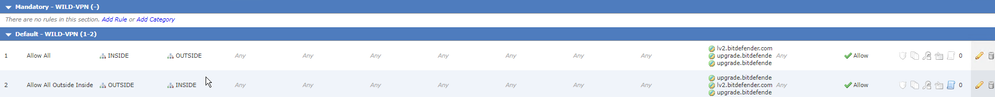
I'm trying to allow traffic to and from a URL, specifically upgrade.bitdefender.com/av64bit-eps or ip add: 104.18.168.222. I've attached an image of how it's configured on the FMC. Traffic is still not being allowed so I'm trying to confirm what the issue is. I've attached a packet trace as well as some other items
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2020 07:57 AM
Remove the source portsm change to any and then try again.
Useful command, try using the "system support firewall-engine-debug" from the CLI of the FTD and then perform a test and observe the output.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2020 10:06 AM
Thanks again for the reply. I updated the ports to any, but the outcome was still the same. I also tried the suggested command and here's the output:
admin@firepower:~$ system support firewall-engine-debug
-sh: system: command not found
admin@firepower:~$ system ?
-sh: system: command not found
admin@firepower:~$
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2020 10:14 AM
What is the configuration of those URLs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2020 07:38 AM
I figured out how to run the command, but never got any output from the debug. Does that mean that traffic from PC isn't hitting the FMC? However when I ran a packet trace from the FMC the traffic appears to be allowed.
Phase: 1
Type: CAPTURE
Subtype:
Result: ALLOW
Config:
Additional Information:
MAC Access list
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 3
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 207.225.150.1 using egress ifc OUTSIDE
Phase: 4
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group CSM_FW_ACL_ global
access-list CSM_FW_ACL_ advanced permit ip ifc INSIDE any ifc OUTSIDE any rule-id 268434433
access-list CSM_FW_ACL_ remark rule-id 268434433: ACCESS POLICY: WILD-VPN - Default
access-list CSM_FW_ACL_ remark rule-id 268434433: L7 RULE: Allow All
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 5
Type: CONN-SETTINGS
Subtype:
Result: ALLOW
Config:
class-map class-default
match any
policy-map global_policy
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
service-policy global_policy global
Additional Information:
Phase: 6
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: FOVER
Subtype: standby-update
Result: ALLOW
Config:
Additional Information:
Phase: 9
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 10
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 11
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 19909447, packet dispatched to next module
Phase: 12
Type: EXTERNAL-INSPECT
Subtype:
Result: ALLOW
Config:
Additional Information:
Application: 'SNORT Inspect'
Phase: 13
Type: SNORT
Subtype:
Result: ALLOW
Config:
Additional Information:
Snort Trace:
Packet: TCP, SYN, seq 1044228831
Session: new snort session
AppID: service unknown (0), application unknown (0)
Firewall: starting rule matching, zone 2 -> 1, geo 0 -> 0, vlan 0, sgt 65535, username 'No Authentication Required', , icmpType 0, icmpCode 0
Firewall: pending rule-matching, 'Allow All' , pending URL
Snort id 2, NAP id 1, IPS id 0, Verdict PASS
Snort Verdict: (pass-packet) allow this packet
Phase: 14
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 207.225.150.1 using egress ifc OUTSIDE
Phase: 15
Type: ADJACENCY-LOOKUP
Subtype: next-hop and adjacency
Result: ALLOW
Config:
Additional Information:
adjacency Active
next-hop mac address 0000.0c07.ac01 hits 2359096 reference 50
Result:
input-interface: INSIDE
input-status: up
input-line-status: up
output-interface: OUTSIDE
output-status: up
output-line-status: up
Action: allow
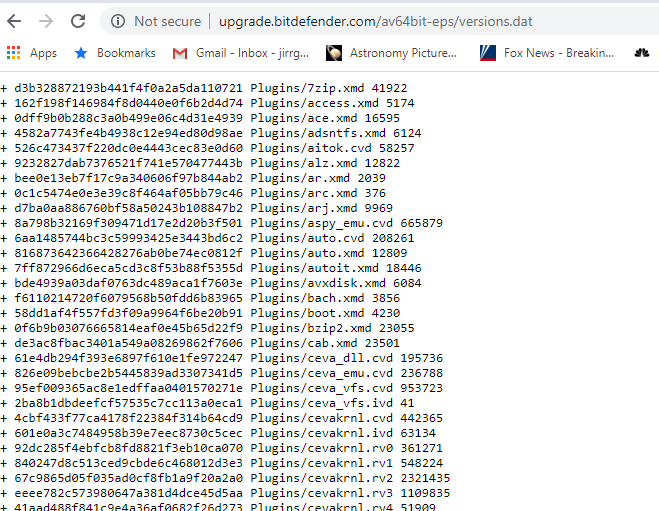
The odd thing is that even though the: upgrade.bitdefender.com/av64bit-eps/versions.dat is allowed on the FMC no vmware servers can reach it. The following pic is what would come up if it could be reached. How is it that packet tracer shows it as reachable yet the servers cannot?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide