- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Firepower 1140 not passing traffic to internet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2021 03:13 PM
I am a problem with my Firepower 1140 using only the FDM. I am new to Firepower devices, I have static routes from my switch to the Firepower can ping both end points from the devices. But my switch cannot get to the internet I tried an auto NAT rule using my inside address to the outside port but did not work. See bellow for some config information.
Cisco 9300 Switch
Gateway of last resort is 192.168.2.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 192.168.2.1
20.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 20.20.20.0/24 is directly connected, Loopback1
L 20.20.20.20/32 is directly connected, Loopback1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Vlan1
L 192.168.1.22/32 is directly connected, Vlan1
192.168.2.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.2.0/24 is directly connected, GigabitEthernet1/0/4
L 192.168.2.2/32 is directly connected, GigabitEthernet1/0/4
192.168.10.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.10.0/24 is directly connected, Vlan10
L 192.168.10.2/32 is directly connected, Vlan10
192.168.40.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.40.0/24 is directly connected, Vlan40
L 192.168.40.2/32 is directly connected, Vlan40
FirePower 1140
S* 0.0.0.0 0.0.0.0 [1/0] via X.X.174.153, outside
C X.X.174.152 255.255.255.248 is directly connected, outside
L X.X.174.154 255.255.255.255 is directly connected, outside
C 192.168.1.0 255.255.255.0 is directly connected, inside
L 192.168.1.1 255.255.255.255 is directly connected, inside
C 192.168.2.0 255.255.255.0 is directly connected, inside2
L 192.168.2.1 255.255.255.255 is directly connected, inside2
C 192.168.10.0 255.255.255.0 is directly connected, vlan10
L 192.168.10.3 255.255.255.255 is directly connected, vlan10
C 192.168.40.0 255.255.255.0 is directly connected, vlan40
L 192.168.40.3 255.255.255.255 is directly connected, vlan40
Interface Ethernet1/1 "outside", is up, line protocol is up
Hardware is EtherSVI, BW 1000 Mbps, DLY 10 usec
MAC address e069.ba02.bf24, MTU 1500
IP address X.X.174.154, subnet mask 255.255.255.248
Traffic Statistics for "outside":
13648294 packets input, 14779630428 bytes
8109453 packets output, 1093238895 bytes
551909 packets dropped
Interface Ethernet1/4 "inside2", is up, line protocol is up
Hardware is EtherSVI, BW 1000 Mbps, DLY 10 usec
MAC address e069.ba02.bf27, MTU 1500
IP address 192.168.2.1, subnet mask 255.255.255.0
Traffic Statistics for "inside2":
1051147 packets input, 52419537 bytes
912 packets output, 56983 bytes
315608 packets dropped
Auto NAT Policies (Section 2)
1 (nlp_int_tap) to (inside) source static nlp_server_0_http_intf9 interface service tcp https https
translate_hits = 0, untranslate_hits = 22746
2 (nlp_int_tap) to (inside) source static nlp_server_0_ssh_intf9 interface service tcp ssh ssh
translate_hits = 0, untranslate_hits = 3
3 (nlp_int_tap) to (inside) source static nlp_server_0_ssh_ipv6_intf9 interface ipv6 service tcp ssh ssh
translate_hits = 0, untranslate_hits = 0
7 (nlp_int_tap) to (diagnostic) source dynamic nlp_client_0_intf2 interface
translate_hits = 0, untranslate_hits = 0
8 (nlp_int_tap) to (outside) source dynamic nlp_client_0_intf3 interface
translate_hits = 105808, untranslate_hits = 749
9 (nlp_int_tap) to (outside_main) source dynamic nlp_client_0_intf4 interface
translate_hits = 0, untranslate_hits = 0
10 (nlp_int_tap) to (inside2) source dynamic nlp_client_0_intf5 interface
translate_hits = 0, untranslate_hits = 0
14 (nlp_int_tap) to (inside) source dynamic nlp_client_0_intf9 interface
translate_hits = 295, untranslate_hits = 0
15 (inside2) to (outside) source dynamic CorwSW interface
translate_hits = 0, untranslate_hits = 0
Thanks in advance.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2021 12:22 AM
@00u18jg7x27DHjRMh5d7 you are not trunking the VLANs, you've got a routed port between the switch and the FTD. So remove the sub interfaces from the FTD and create static routes on the FTD for each of the switches VLAN via the "inside2" interface with a next hop of 192.168.2.2.
You will need to ensure you have NAT configured for these VLANs and permitting traffic via an AC rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2021 11:50 PM
@00u18jg7x27DHjRMh5d7 hard to tell, run packet-tracer from the CLI and provide the output for review. Example:-
packet-tracer input inside2 tcp <inside2 src ip> 3000 <8.8.8.8> 80
Do you have an ACP rule configured to permit at least dns, http and https outbound from the inside2 networks?
Provide the output of "show nat detail".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2021 08:31 AM - edited 11-30-2021 08:32 AM
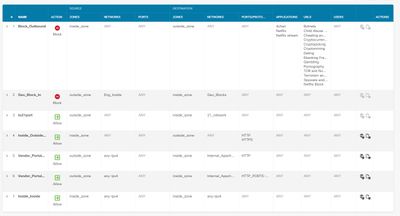
So it looks like something is blocking the next hop from core switch the only denied rules are for geo locations and outbound defaults for threat URL's and applications we don't want used. Not sure were another rule would be blocking.
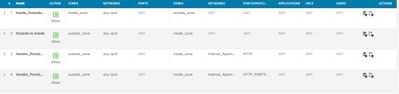
Inside2 is part of the inside zone, bellow I have also attached an overview of the current AC rules.
Thanks
Port on FP as next hop from core
CLI Console
> packet-tracer input inside2 tcp 192.168.2.1 3000 8.8.8.8 80
Phase: 1
Type: INPUT-ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
Found next-hop X.X.174.153 using egress ifc outside(vrfid:0)
Phase: 2
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: inside2(vrfid:0)
input-status: up
input-line-status: up
output-interface: outside(vrfid:0)
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x00005576e034f2b0 flow (NA)/NA
>
To static port on core switch side
> packet-tracer input inside2 tcp 192.168.2.2 3000 8.8.8.8 80
Phase: 1
Type: INPUT-ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
Found next-hop X.X.174.153 using egress ifc outside(vrfid:0)
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group NGFW_ONBOX_ACL global
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435468 ifc inside2 any ifc outside any rule-id 268435468 event-log both
access-list NGFW_ONBOX_ACL remark rule-id 268435468: ACCESS POLICY: NGFW_Access_Policy
access-list NGFW_ONBOX_ACL remark rule-id 268435468: L7 RULE: Block_Outbound
object-group service |acSvcg-268435468
service-object ip
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 409335, packet dispatched to next module
Phase: 8
Type: EXTERNAL-INSPECT
Subtype:
Result: ALLOW
Config:
Additional Information:
Application: 'SNORT Inspect'
Phase: 9
Type: SNORT
Subtype:
Result: ALLOW
Config:
Additional Information:
Snort Trace:
Firewall: starting AC rule matching, zone 1 -> 2, geo 0 -> 0, vlan 0, sgt 0, src sgt type 0, dest_sgt_tag 0, dest sgt type 0, user 9999997, icmpType 184, icmpCode 80
Packet: TCP, SYN, seq 1602900594
Session: new snort session
AppID: service unknown (0), application unknown (0)
Firewall: starting AC rule matching, zone 1 -> 2, geo 0 -> 0, vlan 0, sgt 0, src sgt type 0, dest_sgt_tag 0, dest sgt type 0, user 9999997, icmpType 0, icmpCode 0
Firewall: pending rule-matching, id 268435468, pending AppID
Snort id 5, NAP id 3, IPS id 0, Verdict PASS
Snort Verdict: (pass-packet) allow this packet
Phase: 10
Type: INPUT-ROUTE-LOOKUP-FROM-OUTPUT-ROUTE-LOOKUP
Subtype: Resolve Preferred Egress interface
Result: ALLOW
Config:
Additional Information:
Found next-hop X.X.174.153 using egress ifc outside(vrfid:0)
Phase: 11
Type: ADJACENCY-LOOKUP
Subtype: Resolve Nexthop IP address to MAC
Result: ALLOW
Config:
Additional Information:
Found adjacency entry for Next-hop X.X.174.153 on interface outside
Adjacency :Active
MAC address X.X.d1cb hits 2 reference 13
Result:
input-interface: inside2(vrfid:0)
input-status: up
input-line-status: up
output-interface: outside(vrfid:0)
output-status: up
output-line-status: up
Action: allow
To Core Switch
CLI Console
> packet-tracer input inside2 tcp 192.168.1.22 3000 8.8.8.8 80
Phase: 1
Type: INPUT-ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
Found next-hop X.X.174.153 using egress ifc outside(vrfid:0)
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group NGFW_ONBOX_ACL global
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435468 ifc inside2 any ifc outside any rule-id 268435468 event-log both
access-list NGFW_ONBOX_ACL remark rule-id 268435468: ACCESS POLICY: NGFW_Access_Policy
access-list NGFW_ONBOX_ACL remark rule-id 268435468: L7 RULE: Block_Outbound
object-group service |acSvcg-268435468
service-object ip
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 3
Type: NAT
Subtype:
Result: ALLOW
Config:
object network CorwSW
nat (inside2,outside) dynamic interface
Additional Information:
Dynamic translate 192.168.1.22/3000 to X.X.174.154/3000
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 409244, packet dispatched to next module
Phase: 9
Type: EXTERNAL-INSPECT
Subtype:
Result: ALLOW
Config:
Additional Information:
Application: 'SNORT Inspect'
Phase: 10
Type: SNORT
Subtype:
Result: ALLOW
Config:
Additional Information:
Snort Trace:
Firewall: starting AC rule matching, zone 1 -> 2, geo 0 -> 0, vlan 0, sgt 0, src sgt type 0, dest_sgt_tag 0, dest sgt type 0, user 9999997, icmpType 184, icmpCode 80
Packet: TCP, SYN, seq 1119678248
Session: new snort session
AppID: service unknown (0), application unknown (0)
Firewall: starting AC rule matching, zone 1 -> 2, geo 0 -> 0, vlan 0, sgt 0, src sgt type 0, dest_sgt_tag 0, dest sgt type 0, user 9999997, icmpType 0, icmpCode 0
Firewall: pending rule-matching, id 268435468, pending AppID
Snort id 3, NAP id 3, IPS id 0, Verdict PASS
Snort Verdict: (pass-packet) allow this packet
Phase: 11
Type: INPUT-ROUTE-LOOKUP-FROM-OUTPUT-ROUTE-LOOKUP
Subtype: Resolve Preferred Egress interface
Result: ALLOW
Config:
Additional Information:
Found next-hop X.X.174.153 using egress ifc outside(vrfid:0)
Phase: 12
Type: ADJACENCY-LOOKUP
Subtype: Resolve Nexthop IP address to MAC
Result: ALLOW
Config:
Additional Information:
Found adjacency entry for Next-hop X.X.174.153 on interface outside
Adjacency :Active
MAC address X.X.d1cb hits 0 reference 15
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2021 08:44 AM
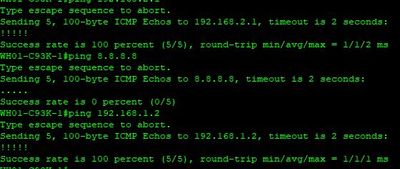
@00u18jg7x27DHjRMh5d7 I don't see you permitting outbound DNS in any of those rules (from inside to outside), are there other rules?
If DNS is not the issue, can you run "system support firewall-engine-debug" filter on the source IP address and generate some consistent traffic. Provide a screenshot of the output.
FYI, I don't think your first rule "Block_Outbound" will do what you intend. It will match application and URL, not application or URL. Not sure if that was your intention?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2021 11:10 AM
So I have main traffic flowing now I didn't have a route from FP to inside network. But all traffic seems to be flowing both directions now.
Only issue now is getting my Vlans to route out. Will these need there own rules for routing out of the FP?
Thanks for the help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2021 11:43 AM
@00u18jg7x27DHjRMh5d7 you can either create network objects for those networks (vlans) and add the objects to the ACP rules to permit the traffic. Alternatively just use the "inside_zone" in the ACP rules, as long as the interface is a member of the "inside_zone" security zone the traffic will be permitted, obviously the FTD will need to have routes to those internal VLANs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2021 06:21 AM
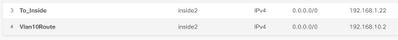
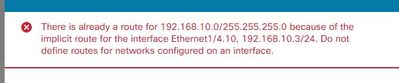
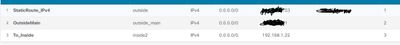
No I have not resolved this issue I have a rule from inside to outside using the zones not working for the vlans. The only static route I could create is listed below everything else gives me the error message also listed bellow. If the FP knows the route exist I don't understand why its not passing the traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2021 06:28 AM
@00u18jg7x27DHjRMh5d7 those routes are incorrect, why are you routing all traffic (0.0.0.0/0) via the inside interface? You initial configuration above had the default route via the outside interface.
Your configuration also indicates that the VLANs are directly connected to the firewall, so therefore no statics should be required. Are you trunking the VLANs between the switch and the FTD? Is the default gateway for the clients the FTD?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2021 12:00 PM
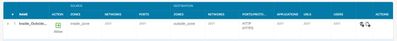
I have attached full clips of the rules to everything can be seen I added the inside rule yesterday in an attempt to route traffic inside has not been working.
GigabitEthernet1/0/3 192.168.2.2 /24 is static port on Core switch
E 1/4 192.168.2.1 /24 port on FP device part of inside zone
E1/1 & 1/3 are ISP connections in Outside Zone
I have a route that is static from core to the FP port I can ping it From Core cannot reach past it normal traffic or VLAN.
FP device can reach all devices on inside network threw core switch. I have configured access rules and NAT that I feel should allow traffic.
I am just missing something small but not sure what it is at this point......
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2021 12:22 PM
@00u18jg7x27DHjRMh5d7 this information contradicts the information in your first post.
Gateway of last resort is 192.168.2.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 192.168.2.1
C 192.168.2.0/24 is directly connected, GigabitEthernet1/0/4
L 192.168.2.2/32 is directly connected, GigabitEthernet1/0/4
FirePower 1140
S* 0.0.0.0 0.0.0.0 [1/0] via X.X.174.153, outside
C X.X.174.152 255.255.255.248 is directly connected, outside
C 192.168.2.0 255.255.255.0 is directly connected, inside2
L 192.168.2.1 255.255.255.255 is directly connected, inside2
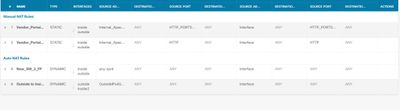
Your default route on the switch is via 192.168.2.1 which is interface inside2 on the FTD. Your Auto NAT rule is for inside not inside2. Create another Auto NAT rule for inside2
If that doesn't work run packet-tracer - packet-tracer inside2 input icmp 192.168.2.2 8 0 8.8.8.8 and provide the output.
Provide "show run", "show route" and "show nat detail" from the FTD and "show run" and "show ip route" from the switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2021 02:24 PM
So that worked cant believe I over looked that. So now only thing not transmitting is the vlans, I have the gateway set on L3 Switch that is now routing traffic out of the FP. DO you set an IP on sub-interface on the FP? or just make the port aware of vlan like I have now? I have attached what should be all the useful information
Thanks again.
!
hostname WH01-C93K-1
!
!
vrf definition Mgmt-vrf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
!
no aaa new-model
clock timezone CST -4 0
clock summer-time CDT recurring
switch 1 provision c9300-48p
switch 2 provision c9300-48p
!
!
!
!
ip routing
!
ip host et-svr-01 192.168.1.238
ip name-server 192.168.1.238
ip domain name etech.local
ip dhcp relay information option
ip dhcp relay information policy keep
ip dhcp relay information trust-all
!
!
!
login on-success log
ipv6 unicast-routing
!
!
!
!
!
vtp domain xxxxxxxxxxx.com
vtp mode off
no device-tracking logging theft
!
!
diagnostic bootup level minimal
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
!
!
transceiver type all
monitoring
!
vlan 10,20,30,40,50,60,70,80,90,100,120,150
!
!
!
interface Loopback1
ip address 20.20.20.20 255.255.255.0
!
interface GigabitEthernet0/0
vrf forwarding Mgmt-vrf
ip address x.x.x.x x.x.x.x
negotiation auto
!
interface GigabitEthernet1/0/1
description Truck to FP 1.1
switchport mode trunk
ip dhcp relay information trusted
!
interface GigabitEthernet1/0/2
description Truck to WH01-A92K-1
switchport mode trunk
ip dhcp relay information trusted
!
interface GigabitEthernet1/0/3
description Routing port to FP
no switchport
ip dhcp relay information trusted
ip address 192.168.2.2 255.255.255.0
!
interface GigabitEthernet1/0/4
switchport mode trunk
ip dhcp relay information trusted
!
interface GigabitEthernet1/0/13
switchport access vlan 20
switchport mode access
!
interface GigabitEthernet1/0/14
switchport access vlan 10
switchport mode access
ip dhcp relay information trusted
!
interface GigabitEthernet1/0/15
switchport access vlan 30
switchport mode access
!
!
!
!
interface Vlan1
ip address 192.168.1.22 255.255.255.0
!
interface Vlan10
description Maintenance
ip address 192.168.10.1 255.255.255.0
ip helper-address 192.168.1.238
!
interface Vlan20
description Marketing - Media
ip address 192.168.20.1 255.255.255.0
ip helper-address 192.168.1.238
!
interface Vlan30
description Sales Floor
ip address 192.168.30.1 255.255.255.0
ip helper-address 192.168.1.238
!
router rip
version 2
network 192.168.0.0
no auto-summary
!
ip forward-protocol nd
ip http server
ip http authentication local
ip http secure-server
ip route 0.0.0.0 0.0.0.0 192.168.2.1
!
!
ip access-list standard 10
10 permit 192.168.2.0 0.0.0.255
!
!
control-plane
service-policy input system-cpp-policy
!
!
end
Gateway of last resort is 192.168.2.1 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 192.168.2.1
20.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 20.20.20.0/24 is directly connected, Loopback1
L 20.20.20.20/32 is directly connected, Loopback1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Vlan1
L 192.168.1.22/32 is directly connected, Vlan1
192.168.2.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.2.0/24 is directly connected, GigabitEthernet1/0/3
L 192.168.2.2/32 is directly connected, GigabitEthernet1/0/3
192.168.10.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.10.0/24 is directly connected, Vlan10
L 192.168.10.1/32 is directly connected, Vlan10
192.168.20.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.20.0/24 is directly connected, Vlan20
L 192.168.20.1/32 is directly connected, Vlan20
192.168.30.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.30.0/24 is directly connected, Vlan30
L 192.168.30.1/32 is directly connected, Vlan30
####################################################################
#######################################################################
FP Device
> show nat detail
Manual NAT Policies (Section 1)
1 (inside2) to (outside) source static Internal_Apache_Vendor_Web_Server interface service _|NatOrigSvc_18c7d892-4172-11ec-ae7f-41e287ee508d _|NatMappedSvc_18c7d892-4172-11ec-ae7f-41e287ee508d
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.1.248/32, Translated: X.X.174.154/29
Service - Origin: tcp source eq 9090 , Translated: tcp source eq 9090
2 (inside2) to (outside) source static Internal_Apache_Vendor_Web_Server interface service _|NatOrigSvc_dc093aef-4311-11ec-afdb-0d6b9a1be6b3 _|NatMappedSvc_dc093aef-4311-11ec-afdb-0d6b9a1be6b3
translate_hits = 2, untranslate_hits = 2
Source - Origin: 192.168.1.248/32, Translated: X.X.174.154/29
Service - Origin: tcp source eq www , Translated: tcp source eq www
Auto NAT Policies (Section 2)
1 (nlp_int_tap) to (inside) source static nlp_server_0_http_intf8 interface service tcp https https
translate_hits = 0, untranslate_hits = 596
Source - Origin: 169.254.1.3/32, Translated: 192.168.1.1/24
Service - Protocol: tcp Real: https Mapped: https
2 (nlp_int_tap) to (inside) source static nlp_server_0_ssh_intf8 interface service tcp ssh ssh
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.1.1/24
Service - Protocol: tcp Real: ssh Mapped: ssh
3 (nlp_int_tap) to (inside) source static nlp_server_0_ssh_ipv6_intf8 interface ipv6 service tcp ssh ssh
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
Service - Protocol: tcp Real: ssh Mapped: ssh
4 (outside) to (inside2) source dynamic OutsideIPv4Gateway interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: X.X.174.153/32, Translated: 192.168.2.1/24
5 (nlp_int_tap) to (vlan20) source dynamic nlp_client_0_intf10 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 0.0.0.0/32
6 (nlp_int_tap) to (vlan30) source dynamic nlp_client_0_intf11 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 0.0.0.0/32
7 (nlp_int_tap) to (vlan1) source dynamic nlp_client_0_intf12 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 0.0.0.0/32
8 (nlp_int_tap) to (diagnostic) source dynamic nlp_client_0_intf2 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 0.0.0.0/32
9 (nlp_int_tap) to (outside_main) source dynamic nlp_client_0_intf3 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: X.X.88.125/24
10 (nlp_int_tap) to (outside) source dynamic nlp_client_0_intf4 interface
translate_hits = 576, untranslate_hits = 3
Source - Origin: 169.254.1.3/32, Translated: X.X.174.154/29
11 (nlp_int_tap) to (brdg2) source dynamic nlp_client_0_intf5 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 0.0.0.0/32
12 (nlp_int_tap) to (brdg1) source dynamic nlp_client_0_intf6 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 0.0.0.0/32
13 (nlp_int_tap) to (inside2) source dynamic nlp_client_0_intf7 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.2.1/24
14 (nlp_int_tap) to (inside) source dynamic nlp_client_0_intf8 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.1.1/24
15 (nlp_int_tap) to (vlan10) source dynamic nlp_client_0_intf9 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 0.0.0.0/32
16 (inside2) to (outside) source dynamic any-ipv4 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: X.X.174.154/29
17 (nlp_int_tap) to (vlan20) source dynamic nlp_client_0_ipv6_intf10 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
18 (nlp_int_tap) to (vlan30) source dynamic nlp_client_0_ipv6_intf11 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
19 (nlp_int_tap) to (vlan1) source dynamic nlp_client_0_ipv6_intf12 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
20 (nlp_int_tap) to (diagnostic) source dynamic nlp_client_0_ipv6_intf2 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
21 (nlp_int_tap) to (outside_main) source dynamic nlp_client_0_ipv6_intf3 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
22 (nlp_int_tap) to (outside) source dynamic nlp_client_0_ipv6_intf4 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
23 (nlp_int_tap) to (brdg2) source dynamic nlp_client_0_ipv6_intf5 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
24 (nlp_int_tap) to (brdg1) source dynamic nlp_client_0_ipv6_intf6 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
25 (nlp_int_tap) to (inside2) source dynamic nlp_client_0_ipv6_intf7 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
26 (nlp_int_tap) to (inside) source dynamic nlp_client_0_ipv6_intf8 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
27 (nlp_int_tap) to (vlan10) source dynamic nlp_client_0_ipv6_intf9 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
Gateway of last resort is X.X.174.153 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via X.X.174.153, outside
C X.X.174.152 255.255.255.248 is directly connected, outside
L X.X.174.154 255.255.255.255 is directly connected, outside
C 192.168.2.0 255.255.255.0 is directly connected, inside2
L 192.168.2.1 255.255.255.255 is directly connected, inside2
NGFW Version 6.6.1
!
vrf to10group
vrf Vlan10
!
interface Ethernet1/1
nameif outside
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address X.X.174.154 255.255.255.248
ospf cost 20
ospf authentication null
!
interface Ethernet1/2
nameif inside
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
vrf forwarding Vlan10
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet1/3
nameif outside_main
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address X.X.88.125 255.255.255.0
!
interface Ethernet1/4
nameif inside2
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address 192.168.2.1 255.255.255.0
ospf cost 65
ospf authentication null
!
interface Ethernet1/4.1
vlan 1
nameif vlan1
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
no ip address
!
interface Ethernet1/4.10
vlan 10
nameif vlan10
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
no ip address
!
interface Ethernet1/4.20
vlan 20
nameif vlan20
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
no ip address
!
interface Ethernet1/4.30
vlan 30
nameif vlan30
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
no ip address
!
interface Management1/1
management-only
nameif diagnostic
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
no ip address
!
ftp mode passive
ngips conn-match vlan-id
dns domain-lookup outside_main
dns domain-lookup outside
dns domain-lookup inside2
dns domain-lookup inside
dns server-group CiscoUmbrellaDNSServerGroup
name-server 208.67.222.222
name-server 208.67.220.220
dns-group CiscoUmbrellaDNSServerGroup
object network any-ipv4
subnet 0.0.0.0 0.0.0.0
object network any-ipv6
subnet ::/0
object network OutsideIPv4DefaultRoute
subnet 0.0.0.0 0.0.0.0
object network XXXXXXXX_Inside
subnet 192.168.1.0 255.255.255.0
object network BDC_Gateway
host X.X.X.38
object network BDC_Inside_Network
subnet X.X.0.0 255.255.255.0
object network BDC_Server
host X.X.0.X
object network Fonality_Server
host 192.168.1.251
object network OutsideIPv4Gateway
host X.X.174.153
object network Outside_Main_Gateway
host X.X.88.1
object network ET-SVR-01
host 192.168.1.238
object network Prelude
host 192.168.1.228
object network Internal_Apache_Vendor_Web_Server
host 192.168.1.248
object network 10group
subnet 10.10.1.0 255.255.255.0
object network 10netgateway
host 10.10.1.1
object network CorwSW
host 192.168.1.22
object network 21_network
subnet 192.168.2.0 255.255.255.0
object network 22Gateway
host 192.168.1.22
object service _|NatOrigSvc_18c7d892-4172-11ec-ae7f-41e287ee508d
service tcp source eq 9090
object service _|NatMappedSvc_18c7d892-4172-11ec-ae7f-41e287ee508d
service tcp source eq 9090
object service _|NatOrigSvc_dc093aef-4311-11ec-afdb-0d6b9a1be6b3
service tcp source eq www
object service _|NatMappedSvc_dc093aef-4311-11ec-afdb-0d6b9a1be6b3
service tcp source eq www
object-group service |acSvcg-268435457
service-object ip
object-group service |acSvcg-268435462
service-object ip
object-group service |acSvcg-268435471
service-object tcp destination eq www
object-group service |acSvcg-268435470
service-object tcp destination eq 9090
access-list NGFW_ONBOX_ACL remark rule-id 268435457: ACCESS POLICY: NGFW_Access_Policy
access-list NGFW_ONBOX_ACL remark rule-id 268435457: L7 RULE: Inside_Outside_Rule
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435457 ifc inside object any-ipv4 ifc outside any rule-id 268435457 event-log both
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435457 ifc inside object any-ipv4 ifc outside_main any rule-id 268435457 event-log both
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435457 ifc inside2 object any-ipv4 ifc outside any rule-id 268435457 event-log both
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435457 ifc inside2 object any-ipv4 ifc outside_main any rule-id 268435457 event-log both
access-list NGFW_ONBOX_ACL remark rule-id 268435462: ACCESS POLICY: NGFW_Access_Policy
access-list NGFW_ONBOX_ACL remark rule-id 268435462: L7 RULE: Outside to Inside
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435462 ifc outside object any-ipv4 ifc inside any rule-id 268435462 event-log both
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435462 ifc outside object any-ipv4 ifc inside2 any rule-id 268435462 event-log both
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435462 ifc outside_main object any-ipv4 ifc inside any rule-id 268435462 event-log both
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435462 ifc outside_main object any-ipv4 ifc inside2 any rule-id 268435462 event-log both
access-list NGFW_ONBOX_ACL remark rule-id 268435471: ACCESS POLICY: NGFW_Access_Policy
access-list NGFW_ONBOX_ACL remark rule-id 268435471: L7 RULE: Vendor_Portal_http
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435471 ifc outside object any-ipv4 ifc inside object Internal_Apache_Vendor_Web_Server rule-id 268435471 event-log flow-end
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435471 ifc outside object any-ipv4 ifc inside2 object Internal_Apache_Vendor_Web_Server rule-id 268435471 event-log flow-end
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435471 ifc outside_main object any-ipv4 ifc inside object Internal_Apache_Vendor_Web_Server rule-id 268435471 event-log flow-end
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435471 ifc outside_main object any-ipv4 ifc inside2 object Internal_Apache_Vendor_Web_Server rule-id 268435471 event-log flow-end
access-list NGFW_ONBOX_ACL remark rule-id 268435470: ACCESS POLICY: NGFW_Access_Policy
access-list NGFW_ONBOX_ACL remark rule-id 268435470: L7 RULE: Vendor_Portal_2_Inside
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435470 ifc outside object any-ipv4 ifc inside object Internal_Apache_Vendor_Web_Server rule-id 268435470 event-log flow-end
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435470 ifc outside object any-ipv4 ifc inside2 object Internal_Apache_Vendor_Web_Server rule-id 268435470 event-log flow-end
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435470 ifc outside_main object any-ipv4 ifc inside object Internal_Apache_Vendor_Web_Server rule-id 268435470 event-log flow-end
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435470 ifc outside_main object any-ipv4 ifc inside2 object Internal_Apache_Vendor_Web_Server rule-id 268435470 event-log flow-end
access-list NGFW_ONBOX_ACL remark rule-id 1: ACCESS POLICY: NGFW_Access_Policy
access-list NGFW_ONBOX_ACL remark rule-id 1: L7 RULE: DefaultActionRule
access-list NGFW_ONBOX_ACL advanced permit ip any any rule-id 1 event-log flow-end
pager lines 24
logging enable
logging timestamp
logging permit-hostdown
mtu diagnostic 1500
mtu outside_main 1500
mtu outside 1500
mtu brdg2 1500
mtu brdg1 1500
mtu inside2 1500
mtu inside 1500
mtu vlan10 1500
mtu vlan20 1500
mtu vlan30 1500
mtu vlan1 1500
no failover
monitor-interface vlan10
monitor-interface vlan20
monitor-interface vlan30
monitor-interface vlan1
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (inside2,outside) source static Internal_Apache_Vendor_Web_Server interface service _|NatOrigSvc_18c7d892-4172-11ec-ae7f-41e287ee508d _|NatMappedSvc_18c7d892-4172-11ec-ae7f-41e287ee508d
nat (inside2,outside) source static Internal_Apache_Vendor_Web_Server interface service _|NatOrigSvc_dc093aef-4311-11ec-afdb-0d6b9a1be6b3 _|NatMappedSvc_dc093aef-4311-11ec-afdb-0d6b9a1be6b3
!
object network any-ipv4
nat (inside2,outside) dynamic interface
object network OutsideIPv4Gateway
nat (outside,inside2) dynamic interface
access-group NGFW_ONBOX_ACL global
!
router ospf 20
timers throttle lsa 0 5000 5000
log-adj-changes detail
!
router bgp 10
bgp log-neighbor-changes
bgp router-id vrf auto-assign
address-family ipv4 unicast
no auto-summary
no synchronization
exit-address-family
!
route outside 0.0.0.0 0.0.0.0 X.X.174.153 1 track 1
route outside_main 0.0.0.0 0.0.0.0 X.X.88.1 2
route inside2 0.0.0.0 0.0.0.0 192.168.1.22 3
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication login-history
http server enable
http ::/0 inside
http 0.0.0.0 0.0.0.0 inside
ip-client vlan1 ipv6
ip-client vlan1
ip-client vlan30 ipv6
ip-client vlan30
ip-client vlan20 ipv6
ip-client vlan20
ip-client vlan10 ipv6
ip-client vlan10
ip-client inside ipv6
ip-client inside
ip-client inside2 ipv6
ip-client inside2
ip-client brdg1 ipv6
ip-client brdg1
ip-client brdg2 ipv6
ip-client brdg2
ip-client outside ipv6
ip-client outside
ip-client outside_main ipv6
ip-client outside_main
ip-client diagnostic ipv6
ip-client diagnostic
no snmp-server location
no snmp-server contact
sysopt connection tcpmss 0
no sysopt connection permit-vpn
!
track 1 rtr 2116304084 reachability
!
track 2 rtr 1808469510 reachability
!
track 3 rtr 1785869986 reachability
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 inside
ssh ::/0 inside
console timeout 0
dhcpd dns 208.67.222.222 208.67.220.220
dhcpd auto_config inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
group-policy DfltGrpPolicy attributes
webvpn
anyconnect ssl dtls none
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
inspect icmp error
inspect snmp
!
service-policy global_policy global
prompt hostname context
app-agent heartbeat interval 1000 retry-count 3
snort preserve-connection
Cryptochecksum:3800b305c27942290d31f627e9d6dac3
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2021 12:22 AM
@00u18jg7x27DHjRMh5d7 you are not trunking the VLANs, you've got a routed port between the switch and the FTD. So remove the sub interfaces from the FTD and create static routes on the FTD for each of the switches VLAN via the "inside2" interface with a next hop of 192.168.2.2.
You will need to ensure you have NAT configured for these VLANs and permitting traffic via an AC rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2021 06:01 AM
That's what I was afraid of having to do, when I attempted to do a trunk port to the FP device traffic wouldn't flow and I didn't see a setting for trucking on it. That is why i went with a static route.
Thanks for the assistance now that I know the proper settings I can tweak it a little and see if I can sort this out.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: