- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Firepower 2110
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 04:44 AM
Hi Community,
For a Firepower 2110, what are the main criteria used to deploy this appliance either using Appliance or Platform mode? The documentation available online does not seem to answer this question, it only lists a few features that are exclusively available in Platform mode, as opposed to -> Appliance mode, unsupported features section.
If deployed in Platform mode, is there an equivalent command to the "show run" available in ASA to display all the configuration in use in the FXOS module?
Thanks.
Ho
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 07:48 AM
Default mode for 2100 is appliance mode, its like inbuilt FXOS. In 2100 ASA and FXOS operating systems share the same Management Interface. On 4100/9300 FXOS management interface is same as the chassis manager, we need to configure separate interface for the application(ASA/FTD) management.
HTH
Abheesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 05:54 AM
if you configured the appliance in Platform mode and when you need to access to ASA code. all you have to do is login to the console connect asa it will take you to asa and one you in the asa code you can run the command show run. it the same logic apply here LISH and LINA. ASA code is running on LINA where as LISH is FXOS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 06:27 AM
Thanks for the reply.
For a Firepower 2110, what are the main criteria used to deploy this appliance either using Appliance or Platform mode?
Why is it required to have 2 IPs in the management interface when deployed in Platform Mode?
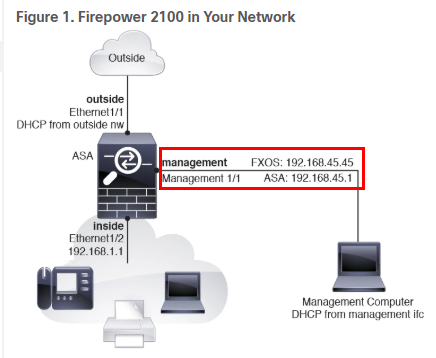
Section: Figure 1. Firepower 2100 in Your Network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 07:48 AM
Default mode for 2100 is appliance mode, its like inbuilt FXOS. In 2100 ASA and FXOS operating systems share the same Management Interface. On 4100/9300 FXOS management interface is same as the chassis manager, we need to configure separate interface for the application(ASA/FTD) management.
HTH
Abheesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 09:01 AM
Hi,
This document (Figure 1. Firepower 2100 in Your Network) shows 2 different IPs for the management interface, not 1:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 10:04 AM
https://www.cisco.com/c/en/us/td/docs/security/firepower/quick_start/fp2100/firepower-2100-gsg/asa-platform.html#id_54062
HTH
Abheesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2020 12:49 AM
Hi,
In the below screenshot, there is one IP for the management interface and a different IP for the Management 1/1, why is this the case?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2020 02:36 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2020 10:18 AM
Do the IPs configured for the ASA and FXOS need to be part of the same subnet or not?
If the former, I understand they can share the same default gateway, is this correct?
If the latter, I presume 2 different default gateways need configured for the management interfaces for the ASA and FXOS respectivelty, is this correct?
For a Firepower 2110, what are the main criteria used to deploy this appliance either using Appliance or Platform mode?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2020 02:25 AM
Hi,
Anyone out there who can assist with this please?
Ta.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2020 04:30 AM
Appliance mode is the default. its completely depend what deployment option you want to adopt. Typically, the FXOS Management 1/1 IP address will be on the same network as the ASA Management 1/1 IP address.
I understand they can share the same default gateway, is this correct?
correct.
I presume 2 different default gateways need configured for the management interfaces for the ASA and FXOS respectivelty, is this correct?
if you running in platform mode yes.
here read this guide on 2110
here cisco live 2019.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2020 08:49 AM
- If the firewall is deployed in platform mode, is it mandatory to have both management interfaces with IPs that belong to different subnets, or is this just one option and can both management interfaces (ASA and FXOS) be configured with IPs that are part of the same subnet?
- If deployed in platform mode and access via ssh is required to the firewall over the management interface, is it possible to access it directly and independently using the ASA´s management interface AND also, the FXOS management interface IP?
Thanks.
Ho
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2020 03:20 AM
Hi,
Anyone out there who knows the answers to the last queries?
Thanks!
Ho.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2020 04:51 AM
Having reviewed document "Cisco Firepower 2100 ASA Platform Mode FXOS Configuration Guide", it appears to be possible to configure DNS, NTP, SNMP and Trustpoints using both ASA and FXOS.
These are all queries for a Platform mode deployment:
1) If DNS, NTP, SNMP and Trustpoints are configured under FXOS, do they all use the management interface for these communications by default? Can this behaviour be changed? Will the ASA inherit these configurations from the FXOS module, and will they be visible from the ASA - not only in terms of the configuration, but also, for instance, is it possible to review the NTP status from the ASA if NTP has been configured from FXOS?
2) Assuming DNS, NTP, SNMP and Trustpoints can be configured from both ASA and FXOS, what are the implications of configuring these from ASA or FXOS?
3) According to the document mentioned above, SSH client is configured by default in FXOS. To secure this access to certain IPs, how is this access list configured?
Thanks.
Ho.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-03-2020 11:28 PM
Hi,
Anyone who can shed some light with these queries please?
Ta.
Ho
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide