- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Firepower FPR 1100 - Series firewall and routing without a router
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2020 11:33 AM - edited 02-21-2020 09:53 AM
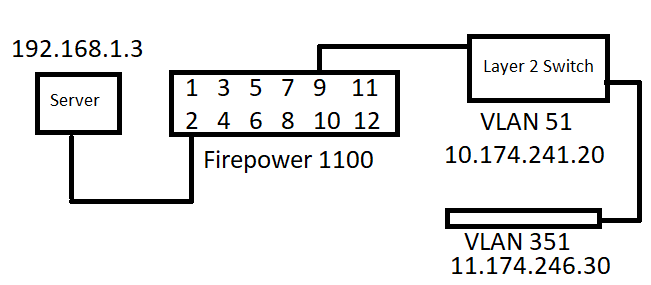
We are working with a Firepower FPR 1100 series firewall in the main office and a remote location with a layer 2 switch. On port 2 of the firewall, we have a server with IP address 192.168.1.3. At port 9 on the firewall we are connected to a switch at a remote site with ip address 10.174.241.20 on vlan 51. Connected to that switch we have a camera at 11.174.246.30 on vlan 351. From the firewall we can ping the switch and the camera. From the switch at the remote location we can ping the interface ip address on the router, but cannot ping the server. Please help with the best way to setup a route from the server to the camera and back. We need the traffic from the camera to the server to pass UDP traffic. Please help as this firewall is new a bit of a learning curve. Below is an image with the basic needs. Also we've pasted the running config below the picture. Thank you for your input!
> show running-config
: Saved
:
: Serial Number: xxxxxxxx
: Hardware: FPR-1120, 5281 MB RAM, CPU Atom C3000 series 2000 MHz, 1 CPU (12 cores)
:
NGFW Version 6.4.0
!
hostname PAIN
enable password ***** encrypted
strong-encryption-disable
names
no mac-address auto
!
interface Ethernet1/1
nameif outside
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address 192.168.2.5 255.255.255.0
!
interface Ethernet1/2
nameif server
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address 192.168.1.99 255.255.255.0
!
interface Ethernet1/3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet1/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet1/5
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet1/6
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet1/7
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet1/8
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet1/9
nameif 96w
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
no ip address
!
interface Ethernet1/9.51
vlan 51
nameif 96switch
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address 10.174.241.99 255.255.255.0
!
interface Ethernet1/9.351
vlan 351
nameif mm96cssgw
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address 11.174.246.99 255.255.255.0
!
interface Ethernet1/10
nameif inside133e
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
no ip address
!
interface Ethernet1/10.71
vlan 71
nameif switch
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address 10.173.241.24 255.255.255.0
!
interface Ethernet1/10.271
vlan 271
nameif cam
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
ip address 10.173.245.24 255.255.255.0
!
interface Ethernet1/11
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet1/12
shutdown
no nameif
no security-level
no ip address
!
interface Management1/1
management-only
nameif diagnostic
cts manual
propagate sgt preserve-untag
policy static sgt disabled trusted
security-level 0
no ip address
!
ftp mode passive
ngips conn-match vlan-id
dns domain-lookup any
dns server-group CiscoUmbrellaDNSServerGroup
name-server 208.67.222.222
name-server 208.67.220.220
dns-group CiscoUmbrellaDNSServerGroup
object network any-ipv4
subnet 0.0.0.0 0.0.0.0
object network any-ipv6
subnet ::/0
access-list NGFW_ONBOX_ACL remark rule-id 1: ACCESS POLICY: NGFW_Access_Policy
access-list NGFW_ONBOX_ACL remark rule-id 1: L5 RULE: DefaultActionRule
access-list NGFW_ONBOX_ACL advanced trust ip any any rule-id 1 event-log both
pager lines 24
logging enable
logging timestamp
logging list eventlog level informational class auth
logging list eventlog level debugging class bridge
logging list eventlog level warnings class config
logging list eventlog level errors class ha
logging list eventlog level emergencies class ids
logging list eventlog level critical class csd
logging list eventlog level notifications class eigrp
logging list eventlog level alerts class dap
logging permit-hostdown
mtu diagnostic 1500
mtu inside96w 1500
mtu outside 1500
mtu inside133e 1500
mtu civicsmartserver 1500
mtu mm59wbcamera 1500
mtu pdue96 1500
mtu mm96eswitch 1500
mtu pdue133 1500
mtu mm133eswitch 1500
mtu cam133e 1500
mtu cam96e 1500
mtu mm96cssgw 1500
mtu mm59wbpdu 1500
mtu mm59wbswitch 1500
no failover
monitor-interface mm59wbcamera
monitor-interface pdue96
monitor-interface mm96eswitch
monitor-interface pdue133
monitor-interface mm133eswitch
monitor-interface cam133e
monitor-interface cam96e
monitor-interface mm96cssgw
monitor-interface mm59wbpdu
monitor-interface mm59wbswitch
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
access-group NGFW_ONBOX_ACL global
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication login-history
ip-client mm96cssgw ipv6
ip-client mm96cssgw
ip-client mm59wbswitch ipv6
ip-client mm59wbswitch
ip-client mm59wbpdu ipv6
ip-client mm59wbpdu
ip-client cam96e ipv6
ip-client cam96e
ip-client cam133e ipv6
ip-client cam133e
ip-client mm133eswitch ipv6
ip-client mm133eswitch
ip-client pdue133 ipv6
ip-client pdue133
ip-client mm96eswitch ipv6
ip-client mm96eswitch
ip-client pdue96 ipv6
ip-client pdue96
ip-client mm59wbcamera ipv6
ip-client mm59wbcamera
ip-client civicsmartserver ipv6
ip-client civicsmartserver
ip-client inside133e ipv6
ip-client inside133e
ip-client outside ipv6
ip-client outside
ip-client inside96w ipv6
ip-client inside96w
ip-client diagnostic ipv6
ip-client diagnostic
no snmp-server location
no snmp-server contact
sysopt connection tcpmss 0
no sysopt connection permit-vpn
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
crypto ikev2 policy 100
encryption des
integrity sha
group 5
prf sha
lifetime seconds 86400
crypto ikev1 policy 150
authentication rsa-sig
encryption des
hash sha
group 5
lifetime 86400
crypto ikev1 policy 160
authentication pre-share
encryption des
hash sha
group 5
lifetime 86400
telnet timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ssl-client
webvpn
anyconnect ssl dtls none
anyconnect ssl rekey time 4
anyconnect ssl rekey method new-tunnel
dynamic-access-policy-record DfltAccessPolicy
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
inspect icmp error
!
service-policy global_policy global
prompt hostname context
app-agent heartbeat interval 1000 retry-count 3
snort preserve-connection
Cryptochecksum:97fd5b77f30adbeaaaa6c98a70e415fd
: end
>
Solved! Go to Solution.
- Labels:
-
Other Network Security Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2020 08:27 PM
What do you mean but the switch can ping the ip address of the router? Are you pinging the firewall ip sitting on the same vlan of the server (192.168.1.99)?
what is the default gateway of your server?
I see an acl doing trust any any which means it shouldn't block any traffic.
Based on the config, i believe you're using fdm gui, am I right?
Have you checked on the connection monitoring page if you see the traffic and if it's allowed?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2020 08:27 PM
What do you mean but the switch can ping the ip address of the router? Are you pinging the firewall ip sitting on the same vlan of the server (192.168.1.99)?
what is the default gateway of your server?
I see an acl doing trust any any which means it shouldn't block any traffic.
Based on the config, i believe you're using fdm gui, am I right?
Have you checked on the connection monitoring page if you see the traffic and if it's allowed?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2020 02:38 PM
I really need to delete this entire question and start over. Thank you for your input as it was spot on with the gateway question. We've done a lot of configuration since this last post and will need to update it completely (will start a new thread.) Thanks again!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide