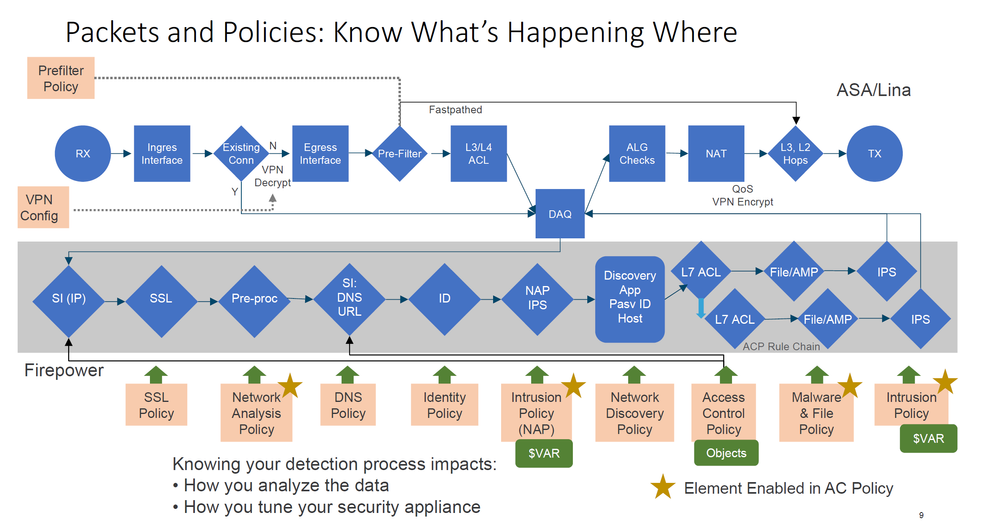
Best Practices for Handling Packets That Pass Before Traffic Identification
-
The default action specified for an access control policy is NOT applied to these packets.
-
Instead, use the following guidelines to choose a value for the Intrusion Policy used before Access Control rule is determined setting in the Advanced settings of the access control policy.
-
You can choose a system-created or custom intrusion policy. For example, you can choose Balanced Security and Connectivity.
-
For performance reasons, unless you have good reason to do otherwise, this setting should match the default action set for your access control policy.
-
If your system does not perform intrusion inspection (for example, in a discovery-only deployment), select No Rules Active. The system will not inspect these initial packets, and they will be allowed to pass.
-
By default, this setting uses the default variable set. Ensure that this is suitable for your purposes.
-
The network analysis policy associated with the first matching network analysis rule preprocesses traffic for the policy you select. If there are no network analysis rules, or none match, the default network analysis policy is used.
-