- Cisco Community
- Technology and Support
- Security
- Network Security
- Firepower Threat Defense Prefilter/Access Control policy allow OSPF
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2022 06:40 PM
Hi, Guys, something confuses me a lot recently.
I configured a FTD with initial settings, there is no any Rules in the Access Control,the Default Action of Access Control is to Block all trafffic,meanwhile,my Prefilter is Default Prefilter Policy with its default action is "Analyze all tunnel traffic".
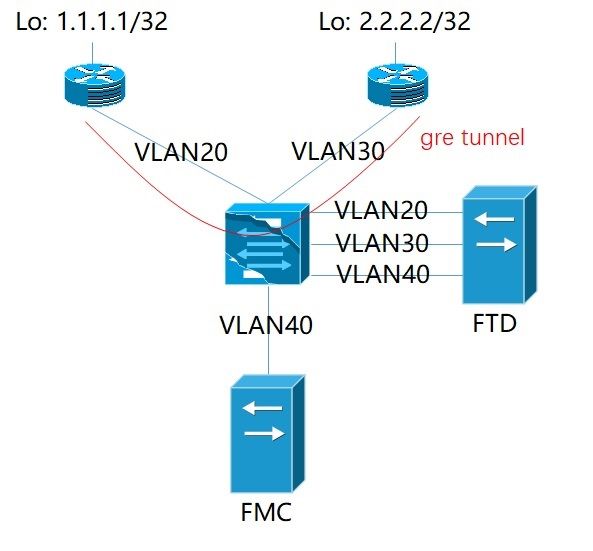
My network topology is folloiwing, two zones connects to my FTD through a L2 switch by configured with two VLANs, the FTD runs as routed mode, a gre tunnel runs across these two zones, and OSPF protocol runs on this gre tunnel, it supposes to the neighbor of OSPF can't build up, cause the prefilter will analyze the gre tunnel, and there is no any Rules to allow the OSPF, but my OSPF runs correctly, can anybody figure out this working principle? Does any policy allow the OSPF protocol running on the gre tunnel?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2022 04:12 AM
do you permit ospf ip
1- multicast using by ospf hello message
2- unicast using by ospf update message
fluctuation of eigrp & ospf may cause of unicast.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2022 04:55 AM
When I check the different in first time I study FTD I found this, hope this what you are looking for
""
- It allows the inspection of tunneled traffic where the FTD LINA engine checks the outer IP header while the Snort engine checks the inner IP header. More specifically, in case of tunneled traffic (e.g. GRE) the rules in the Prefilter policy always act on the outer headers while the rules in the ACP are always applicable to the inside sessions(inner headers). The tunneled traffic refers to these protocols:
- GRE
- IP-in-IP
- IPv6-in-IP
- Teredo Port 3544
""
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2022 01:23 AM
Hi, thanks for your kind reply.
I also refered this material yesterday, according to it, I try to figure out the working process as following:
1) my prefilter policy is set as the Default Prefilter Policy, and Default Action is "Analyze all tunnel traffic", so, when the Inside-1 router try to bulid up a connection with the Inside-2 router by a gre tunnel, the FTD will capture the flow packet, and inspect it (LINA does);
2) the gre tunnel build up successfully;
3) then, Inside-1/Inside-2 will launch a connection for OSPF negotiation, the OSPF Hello packet will be carried on the gre tunnel.
4) LINA engine applies the prefilter policy, cause its action is "Analyze all tunnel traffic",it will send these packets or this connection to the Snort engine, the Snot engine will match this connection with ACP.
My issue is that, I did NOT configure any ACPs to allow the OSPF, and default action it Block all traffic, so it is supposed to abandon this connection, and OSPF can NOT build up a neighbor connection, BUT, the FTD allow the connection and the OSPF works correctly,
the result obeys the working principle in that material.
Update:
I try to run EIGRP, surely, the EIGRP can NOT work! The adjacent neighbor fluctuates.
So, I guess this is the bug in the FTD, my version is 6.3.0, or do you have a better explaination to the OSPF case?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2022 04:12 AM
do you permit ospf ip
1- multicast using by ospf hello message
2- unicast using by ospf update message
fluctuation of eigrp & ospf may cause of unicast.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2022 12:43 AM
For the OSPF case, I did NOT permit OSPF in the ACPs, and Default action of ACPs is block all traffic, but the OSPF works well, no OSPF neighbor adjacent fluctuate, and both side of routes can learn the OSPF routes from each other.
For the EIGRP case, I also did NOT permit EIGRP in the ACPs, and Default action of ACPs is block all traffic as well, the EIGRP can not work, its neighbor adjacent fluctuate, this result is expected.
So, as I memtioned before, I guess there is some bugs for the OSPF case, or exists any other implict configuration to allow the OSPF?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: