- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Forcing ASA to NAT when using NTP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2016 08:00 AM - edited 03-12-2019 12:33 AM
When giving an ASA an NTP server that is on the outside Internet, is there a way of forcing which NAT rule it uses? It seems to use the default egress interface which is not what we want.
We've tried creating a NAT rule that has a source interface of any and a destination interface of the outside interface, but our specific NAT rule still doesn't get caught.
Has anyone tried to do this before and if so did you get this to work?
It's an ASA5515-X running 9.3x
Thanks!
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2016 08:38 AM
Hi
In your NTP command, what source interface have you set? e.g.
ntp server 172.1.1.1 key 1 source inside
Have you done a packet tracer from the CLI, with whatever interface you have set in NTP as the SRC_ADDR, and if so can you paste the output?
Example
"packet-tracer input DMZ tcp 10.2.1.1 1024 10.4.2.1 http"
packet-tracer input [src_int] protocol src_addr src_port dest_addr dest_port [detailed] [xml]
Thanks
James
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2016 08:55 AM
The NTP command reads as follows:
ntp server x.x.x.x source outside
(no authentication is used)
If we do a packet tracer and we specify the outside interface of the firewall as the source IP address, the NAT rule we want fires correctly. I'm not in a position to undertake a packet tracer on the firewall at present.
Thanks, Anish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2016 09:38 AM
I think because the packet is originating on the OUTSIDE interface, it's just doing a route lookup the been forwarded, bypassing NAT - see packet order of operations
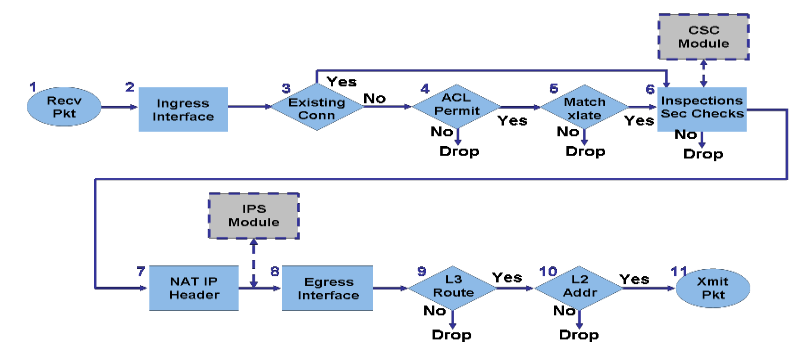
I could be wrong but try something like this:
object network obj-local
subnet 172.22.1.0 255.255.255.0 (inside interface)
object network obj-remote
subnet x.y.z.1 255.255.255.0 (NTP-destination)
nat (inside,outside) 1 source static obj-local obj-local destination static obj-remote obj-remote
ntp server x.y.z.1 source inside
You'll need a matching ACL obviously.
Hope it helps
Dont forget to rate :-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2016 12:44 AM
Hi James,
thanks for the coherent response. can I just check a couple of things with you?
with the command:
object network obj-local
subnet 172.22.1.0 255.255.255.0 (inside interface)
Are you proposing that we have the inside interface even though this isn't used as the source IP address?
And the second thing, with the command ntp server x.y.z.1 source inside
should the interface be the interface though which the ntp server is reached? in which case should this read '..... source Outside'
Thanks, Anish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-30-2016 04:05 AM
I was thinking - get the NTP sourced from the inside interface (i.e. ntp server x.y.z.1 source inside) and use that source interface IP in the NAT statement - so you have something to NAT. Obviously doing this you'll need to do an ACL as well.
If you have a default route your routing should still try and pump it out to the Outside.
Like i said, it might not work but at the moment it's the only thing i can think of without seeing the config.
Just wondered - at the moment, as the NTP is been sourced from your Outside interface and using that external IP, why do you need to source NAT it to something else?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2016 06:28 AM
Hi James,
We're going to try and mess about with it. But in answer to your question, we need to NAT it because the outside interface of the firewall isn't the outside routable address.
Cheers, Anish
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2016 06:45 AM
Right - it makes sense now. Let me know how you get on and if it works can you rate my responses?
Thanks
James
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2016 08:44 AM
Hi Anish,
Could you share the NAT command you have used on the ASA for the NTP traffic ?
Regards,
Aditya
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:


