- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: FTD Remote Access VPN Restriction
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FTD Remote Access VPN Restriction
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-18-2018 05:10 AM - edited 03-12-2019 04:17 AM
Hello, everyone. We have implemented Anyconnect RA VPN on FTD device. However now i want to restrict from which source global IP Addresses i can connect to. I now in ASA it can be done by control-plane ACL but in FTD i do not see any place to configure it.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2020 02:02 AM - edited 06-22-2020 02:03 AM
Even though control-plane ACLs are technically supported with Flexconfig, it is not currently supported (as of 6.6) to do geoblocking of RA VPN that way.
A TAC engineer confirmed this with me just today. There is an (currently unpublished) enhancement bugID for this: CSCvs65322 ENH | Geo-location based AnyConnect Client connections
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2020 02:50 AM - edited 06-22-2020 02:51 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2020 02:52 AM
Nowdays FTD major missing in terms of Remote Access and tunneling are the following (in my opinion)
- Lack of Geographical restrictions for remote access tunnel group (should be for each tunnel group, makes no sense to do it for the whole firewall interface) and anonymizers
- Lack of SAML authentication support for Remote Access
- Lack of VTI tunnel interfaces -> this is really a major drawbacks for hybrid cloud connectivity
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2020 03:06 AM
@giovanni.augusto #2 and #3 should be coming in Firepower 6.7 this fall.
For #1 I agree - be sure to contact your Cisco account manager and mention ENH bugID CSCvs65322 !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-16-2020 03:57 AM
any update in version 6.7 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2022 11:56 AM
So I was talking to TAC today; while the workaround works but it doesn't scale well, I have to block a country in Asia, and that country has 13K IP subnets, yes we can import .csv with 13k objects each line is one network, but how to group those 13k objects into one object-group to apply it to the extend ACL?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2022 11:43 AM
that wont work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2021 02:48 PM
Any links on what you actually put in the flexconfig?
My scenario is remote access is getting brute force attacked and failing on the auth but we want to block that traffic by geo so it doesn't get that far.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2021 03:35 AM
I have the same Problem. If I configure Object and ACL in FMC and try to write flexconfig like
access-group <acl-name> in interface <interface-name> control-plane
it doesn't work, because ftd doesn't have the ACL and the Object. In flexconfig I can not write ACL.
Anybody have idea or config example how I can do it?
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2021 04:25 AM
You need to create an acl first in the FMC ... lets say controlplaneacl
Then the flexconfig command is (use nameif of the interface instead of the word nameif in the command):
access-group $controlplaneacl in interface nameif control-plane
So example:
access-group $controlplaneacl in interface WAN control-plane
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2021 10:27 AM - edited 06-02-2021 10:30 AM
@jovalo your suggested approach worked fine. I plan to writeup a more detailed how-to for this since the question comes up more and more often lately.
For now, here's my result...
Behavior without control-plane ACL:
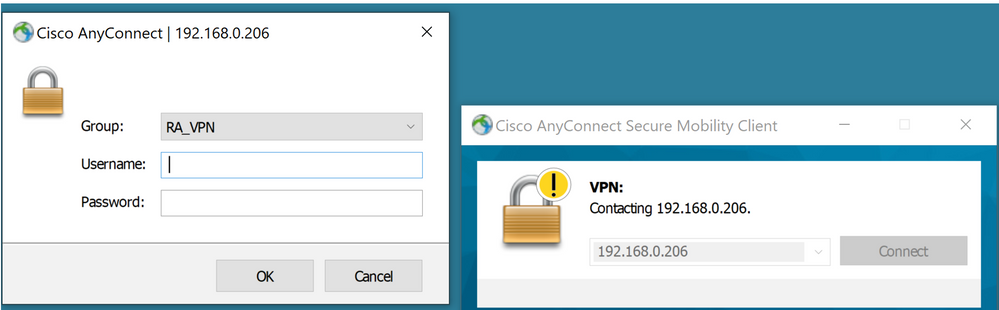
> show running-config access-group access-group CSM_FW_ACL_ global >
Behavior after adding flexconfig with control-plane ACL blocking my PC’s address:
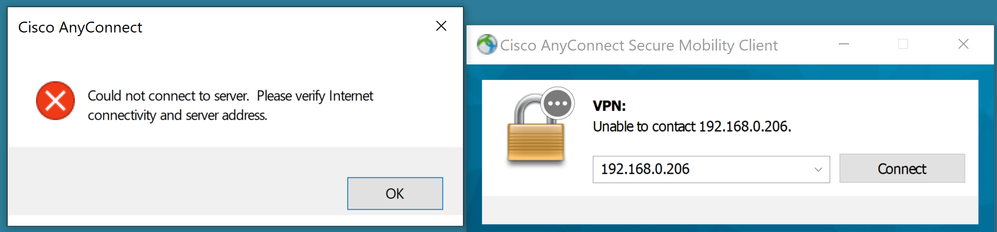
Note the presence of the access-group command applied to the interface and the hit count in the access-list itself:
> show running-config access-group access-group ACL-Control_Plane-Test in interface Outside-Home control-plane access-group CSM_FW_ACL_ global > > show access-list ACL-Control_Plane-Test access-list ACL-Control_Plane-Test; 2 elements; name hash: 0xab9a61e4 access-list ACL-Control_Plane-Test line 1 extended deny object-group ProxySG_ExtendedACL_8589937617 object Spectre-DHCP any (hitcnt=8) 0x29d27b31 access-list ACL-Control_Plane-Test line 1 extended deny ip host 192.168.0.165 any (hitcnt=8) 0x1f6ec140 access-list ACL-Control_Plane-Test line 2 extended permit object-group ProxySG_ExtendedACL_8589937621 any4 any (hitcnt=0) 0x175edbeb access-list ACL-Control_Plane-Test line 2 extended permit ip any4 any (hitcnt=0) 0x08985061 >
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2021 10:48 PM
Funny, but I see the error that the acl doesn't exist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-02-2021 11:36 PM
Don't forget in the FlexConfig Object to add the object by:
Insert --> Insert Policy Object --> Extended ACL object --> choose a name like controlplaneacl --> select the acl
Then that name (in this case controlplaneacl) can be used as a object with the $ so example of the flexconfig line:
access-group $controlplaneacl in interface WAN control-plane
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2021 12:29 AM
I posted a more complete how-to in this other thread:
In coming days I plan to write it all up in a comprehensive white paper for posting on the community.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2021 09:08 PM
@steve121 we cannot currently use geolocation to restrict AnyConnect access.
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvs65322/?rfs=iqvred
- « Previous
-
- 1
- 2
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:







