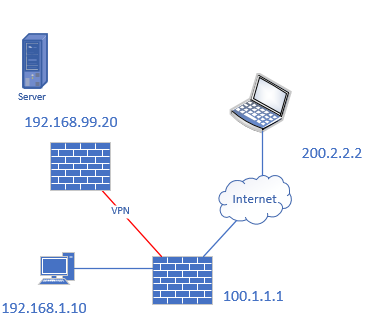
Need some assistance in how to configure ASA to allow hairpin of public Internet traffic across VPN tunnel.
I have a server with an IP of 192.168.99.20 that sits behind an ASA with a VPN tunnel to another ASA with an outside public IP of 100.1.1.1. I need to allow anyone coming in on the Intnernet to reach port 443 on the server via the public IP of 100.1.1.1
Currently, the only traffic mapped to the VPN tunnel between the ASA's is the 192.168.99.0 network and then 192.168.1.0 network.
How can I configure hairpin to allow public traffic on port 443 to reach this server?