- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Hit Count Analyzer - FMC 6.6.1
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2021 02:46 PM - edited 01-27-2021 02:46 PM
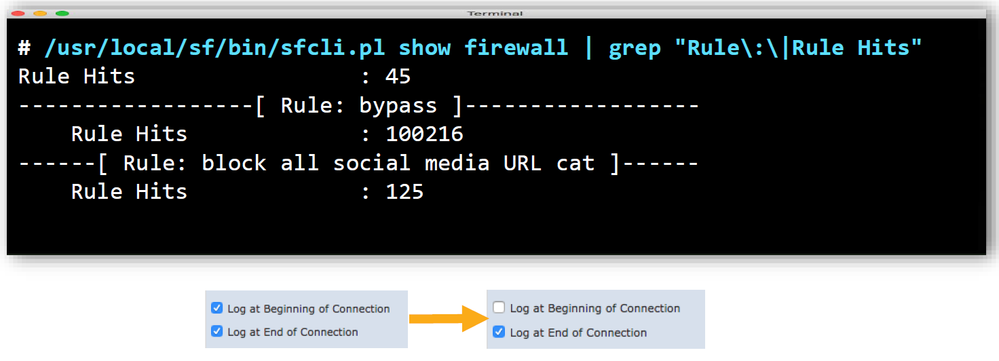
When I run the hitcount analyzer for an ACP and export it to a CSV, the rules with 0 hit counts do not have a date indicating they were never used. Is this the expected behavior? For some of the rules with 0, I imagine they were used at some point, but I can't tell with the date missing from the result.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 08:27 AM
Hit counts will increment independent of logging being set. Logging will additionally generate a syslog message.
Hit counts are not retained across a reboot so a zero count is implicitly "since last boot" (or manual clear of the counts).
Reference (from ASA but the same logic applies): https://www.cisco.com/c/en/us/td/docs/security/asa/asa-cli-reference/A-H/asa-command-ref-A-H/aa-ac-commands.html#wp3307265190
|
log [[level ] [interval secs ] | disable | default ] |
(Optional) Sets logging options when an ACE matches a packet for network access (an ACL applied with the access-group command). If you enter the log keyword without any arguments, you enable system log message 106100 at the default level (6) and for the default interval (300 seconds). If you do not enter the log keyword, then the default system log message 106023 is generated for denied packets. Log options are:
|
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2021 03:37 PM - edited 01-27-2021 03:38 PM
have you enabled the Log for that ACP, If so please check with the command?
You can also test from FTD :
> show access-control-config
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2021 08:02 AM
Yes, logging is enabled at the end of the connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2021 09:22 AM
Can you post the output from command level and GUI to see what is wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2021 12:58 PM
What output are you looking for? When I run the hit count analyzer, there is not an entry in the "last hit time" field for hit counts of 0. The same is true from the CLI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 07:50 AM
Also to note, I have found rules with an incremented hitaount that do not have logging enabled. Are you sure enabling logging pertains to the hit count analyzer?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 08:27 AM
Hit counts will increment independent of logging being set. Logging will additionally generate a syslog message.
Hit counts are not retained across a reboot so a zero count is implicitly "since last boot" (or manual clear of the counts).
Reference (from ASA but the same logic applies): https://www.cisco.com/c/en/us/td/docs/security/asa/asa-cli-reference/A-H/asa-command-ref-A-H/aa-ac-commands.html#wp3307265190
|
log [[level ] [interval secs ] | disable | default ] |
(Optional) Sets logging options when an ACE matches a packet for network access (an ACL applied with the access-group command). If you enter the log keyword without any arguments, you enable system log message 106100 at the default level (6) and for the default interval (300 seconds). If you do not enter the log keyword, then the default system log message 106023 is generated for denied packets. Log options are:
|
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 11:36 AM
Thank you for clarifying! The previous comment was misleading around how logging should be enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2021 12:12 PM
Apologies - i may have mixed things here, Logging is different and hit count is different.
Hit count based on the ACP policies matched and processed.
@Marvin Rhoads is right and corrected.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: