- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: How does the FTD appliance handle return traffic for an ACP?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-26-2018 08:32 AM - edited 02-21-2020 08:36 AM
Hello,
I hope I have the correct board for this question. I have what I hope to be a simple question. My question is how does the FTD appliances, such as the 2130, handle return traffic for a given rule for an access control policy? For instance, if I create a rule to allow a source security zone & network/host to a destination security zone & network/host on destination TCP ports 80 & 443, how will the appliance handle the traffic that comes back in response to the initial request? Will it be blocked, allowed, or will I need to specify the ephemeral range in my rule?
Thanks.
Solved! Go to Solution.
- Labels:
-
Firepower Threat Defense (FTD)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-26-2018 09:17 AM
Hi,
This will get allowed because the source port is the random port 49152 and the session will remain in the state table and it will get allowed with L7 inspection if you enable inspection.
Thanks,
Abheesh
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-26-2018 09:01 AM - edited 12-26-2018 09:26 AM
Hi,
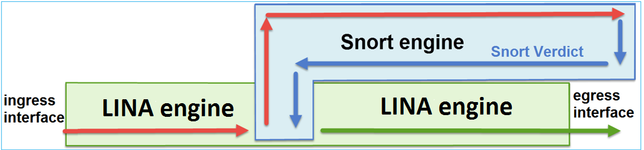
As you know FTD has two engines, LINA & SNORT.
- If a packet enters the ingress interface and it is handled by the LINA engine
- If it is required by the FTD policy the packet is inspected by the Snort engine
- The Snort engine returns a verdict (whitelist or blacklist) for the packet
- The LINA engine drops or forwards the packet based on Snort’s verdict
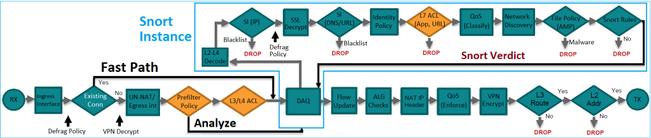
Below diagram will show you the complete packet flow in FTD with ACP
As per your question if a traffic initiated from source to a particular destination FTD keeps the session in session table and match the return traffic as per the table.
Thanks,
Abheesh
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-26-2018 09:11 AM
Hello Abheesh,
Thanks for your quick response. So as long as the originating traffic is held in the session table, the FTD engine will allow the return traffic without any other filtering to take place. For instance, traffic from zone A on source TCP port 49152 to zone B on destination TCP port 80 will be allowed to return from zone B on source TCP port 80 to zone A on destination TCP port 49152 although I don't have an explicit rule opened to allow any traffic on destination TCP port 49152. Is that correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-26-2018 09:17 AM
Hi,
This will get allowed because the source port is the random port 49152 and the session will remain in the state table and it will get allowed with L7 inspection if you enable inspection.
Thanks,
Abheesh
PS: Please don't forget to rate and select as validated answer if this answered your question
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide