- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: How the firewall handles return traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How the firewall handles return traffic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 07:57 AM
Hello All,
Please ignore my ignorance as I tried to wrap my head around this question lingering in my mind.
This is more of a query on how the Cisco firewall handles return traffic when an 'any any' policy is in place. The traffic is originating from a higher security known port 5060, 443, 22, 80 to a lower security destination. Based on my understanding, the return traffic should be allowed due to the permit ip any any rule in place.
Thanks
Will
- Labels:
-
Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 08:33 AM
Hi,
Where and how to apply this ANY ANY policy? What is your configuration?
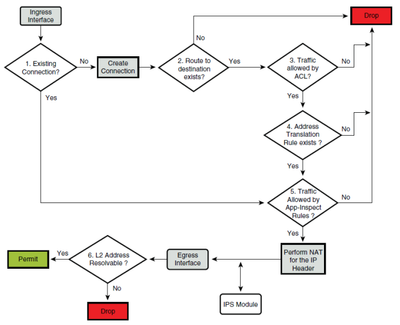
Here is the Cisco ASA packet flow:
I hope it will help you to understand.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 09:41 AM
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 11:59 AM
Hello, Thanks for your detailed reply. Another question I have regarding sip inspection. By default, I can see that
sip is being inspected by the firewall. See global policy-map below.
policy-map global_policy
class inspection_default
inspect dns migrated_dns_map_1
inspect ftp
inspect ip-options
inspect netbios
inspect rsh
inspect rtsp
inspect esmtp
inspect sip
inspect sqlnet
inspect tftp
inspect xdmcp
inspect http
Should sip port 5060 be already opened by the firewall based on it's statefullness? Or I still have to open port 5060 to allow sip traffic from the CUCM to the endpoint?
Appreciate, any light that you can shed on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 02:59 PM
on your sip question: NO
that is not what sip inspection does. so you would need to explicitly allow SIp based on port 5060. once SIP is permitted, sip inspection will look inside the packet and more specifically in the SDP packet contained within sip. based on this, it will dynamically allow ports for RTP. this way you dont need to open thousands of ports for the purpose of allowing video and voice across your FW
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 07:40 PM
You have to explicitly allow SIp based on port 5060
Regards.
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2019 05:23 AM
Thanks for your comment. But wanted to clarify as I thought that due to the
statefullness of the sip traffic, if the UCCM initiated the session port
5060 will be automatically open or allowed. Please see below output and
keep me honest.
ASA4# sh run all | in sip
object service tcp-sip pre-defined
service tcp destination eq sip
object service tcp-udp-sip pre-defined
service tcp-udp destination eq sip
object service udp-sip pre-defined
service udp destination eq sip
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect
0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
policy-map type inspect sip _default_sip_map
traffic-non-sip
ASA4# sh run all | in sip
object service tcp-sip pre-defined
service tcp destination eq sip
object service tcp-udp-sip pre-defined
service tcp-udp destination eq sip
object service udp-sip pre-defined
service udp destination eq sip
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect
0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
policy-map type inspect sip _default_sip_map
traffic-non-sip
Do I still have to allo sip port despite that it's already pre-defined by
the default
ASA configuration?
Appreciate greatly all your input and help.
Regards,
William
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2019 12:15 PM
Those are the configurations in relation to SIP and what to do with the SIP traffic once permitted. The ASA inherently blocks traffic, unless no ACL is applied and you are going from a higher security zone to a lower security zone.
If SIP is not explicitly permitted in the ACL then this traffic would not be permitted through the Firewall.
You would need, for example:
access-list INSIDE permit udp any any eq sip
If the INSIDE acl was applied to your Internal segment on the ASA, this would allow SIP traffic from your Internal Segment through the ASA. The other options you see in your output are now how to handle this traffic, such as Idle Timeout or confirming that it is in fact SIP traffic before permitting the traffic etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2019 12:51 PM
Hi,
Check this document: https://www.cisco.com/c/en/us/td/docs/security/asa/asa96/configuration/firewall/asa-96-firewall-config/inspect-voicevideo.html
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: