- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Issue - Cisco ASA can't communicate between Private and Public Net
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Issue - Cisco ASA can't communicate between Private and Public Network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-03-2023 07:29 PM
Hi There,
I got an issue after migrating the firewall from Cisco ASA 5545 to 5525.
1 of 20 tenants can't communicate to Public Network but can still communicate between Private Network,
but the Public Interface (Gi0/0.5) can ping to the Public Network.
interface GigabitEthernet0/0.5
mac-address 0200.0005.1d00 standby 0200.0005.1d01
nameif INTERNET
security-level 0
ip address 27.254.23.xx 255.255.255.128 standby 27.254.23.xx
!
interface GigabitEthernet0/2.224
nameif IN-01
security-level 30
ip address 10.10.124.xx 255.255.255.224 standby 10.10.124.xx
!
interface GigabitEthernet0/4.123
nameif OUT-01
security-level 0
ip address 10.10.124.xx 255.255.255.224 standby 10.10.124.xx
So, what is pointed to is the NAT table issue.
Did you guy heard about the bug related to NAT table or the issue like this before?
Thank you,
Net
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2023 12:54 AM
you have two interface OUT-01 and INTERNET
which one you use in
NAT and Routing traffic ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2023 05:36 PM
I am using NAT for the INTERNET interface
and static routing for OUT-01
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2023 11:50 PM
sorry again
your Host connect to IN-01 and need to access internet what Interface is egress of traffic ?
are this interface is config with NATing ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2023 09:04 AM
The host behind the IN-01 interface will access the internet through the INTERNET interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2023 06:26 PM
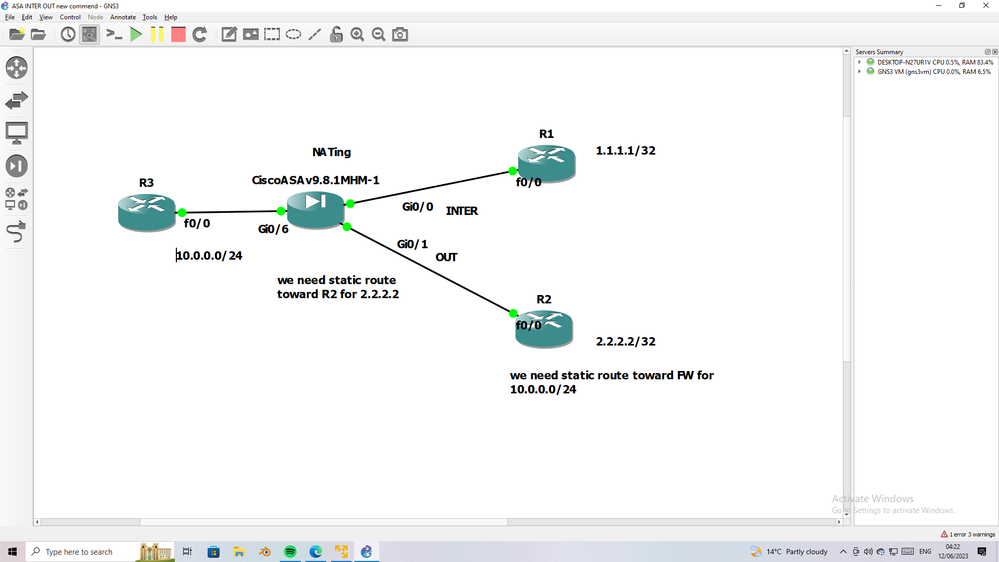
you have default route toward the INTER link and you have NATing to NAT private to public IP
NOW for OUTside we need statice route to forward traffic via this interface and we need in router or L3SW connect to FW static route also toward the ASA for subnet connect to INside
you have missing one of route either in ASA or in R/L3SW connect to ASA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2023 09:43 PM - edited 06-11-2023 09:46 PM
Hi Guy
I am sorry for the unclear information.
The problem is the VM behind the private subnet (R3) can't reach the internet (8.8.8.8 behind R1 router)
but able to reach the VM behind another subnet interface with in the firewall.
and the INTER interface on the firewall itself can reach the 8.8.8.8 (behind the 1.1.1.1 or R1 Router in your picture)
Commonly, the issue like this we always point to the NAT configuration, am I correct?
But as I checked, the NAT configuration on the existing firewall and new firewall is totally the same.
So, Did you guy used to facing the problem like this ?
IOS version : 9.14(4)7 on both existing and new firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2023 05:37 AM
Yes it point to NAT
can you do packet tracer for this traffic and share the result here
NOTE:- please add detail keyword to packet tracer
Thanks
MHM
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: