- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: MACsec Switch to Host with ISE and Microsoft CA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
MACsec Switch to Host with ISE and Microsoft CA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2021 03:47 AM
hello all.
been trying to configure this setup for the last 3 weeks.
at the moment i have a session on the ise, however anyconnect shows the encryption as none...
also, i do not have network
what am i missing here?
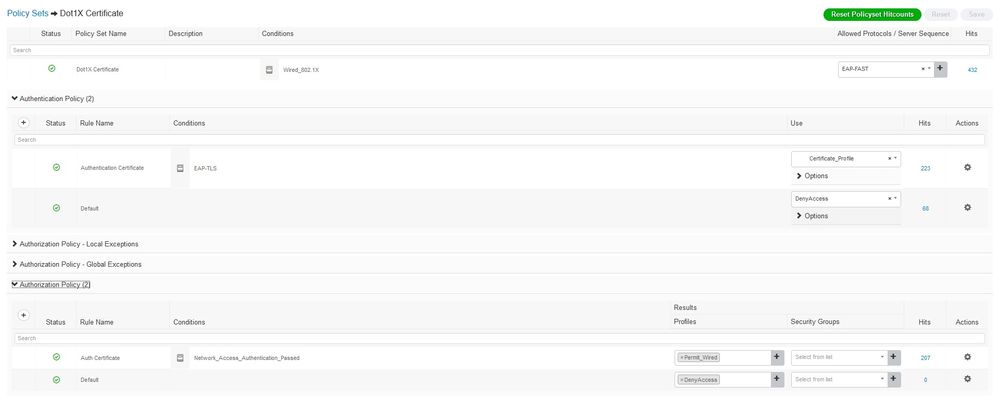
the authentication and authorization policies are ok.
the ca seems to be working fine
the switch config seems ok
i am out of ideas
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2021 02:25 PM
we need to know more information, how your setup and configuration, what switch model, what is the port config? what is not working?
is this any connect on always? what version of any connect?
here is some example reference :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2021 06:18 AM
hi.
at the moment this is the situation:
anyconnect shows the connection as connected
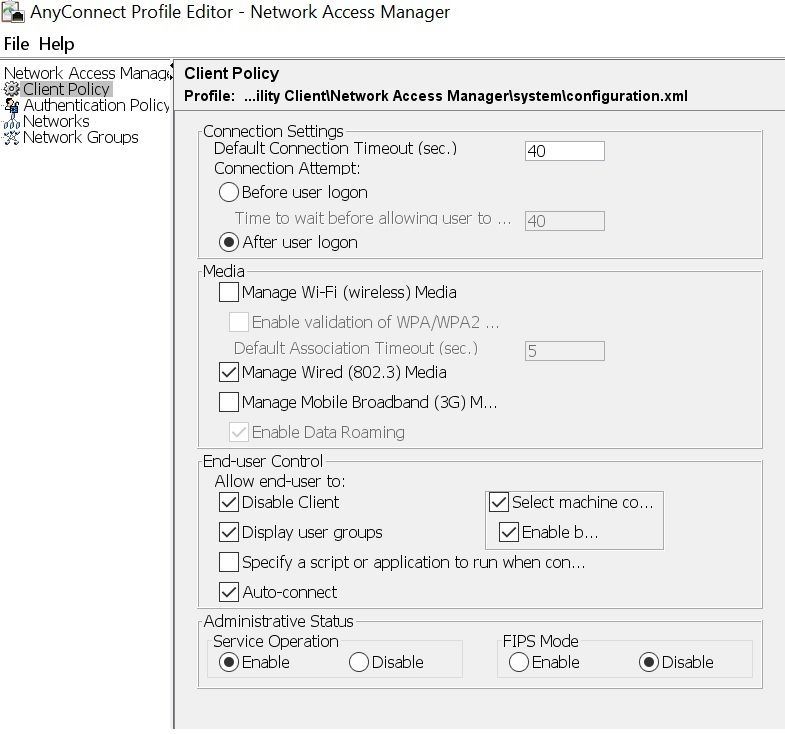
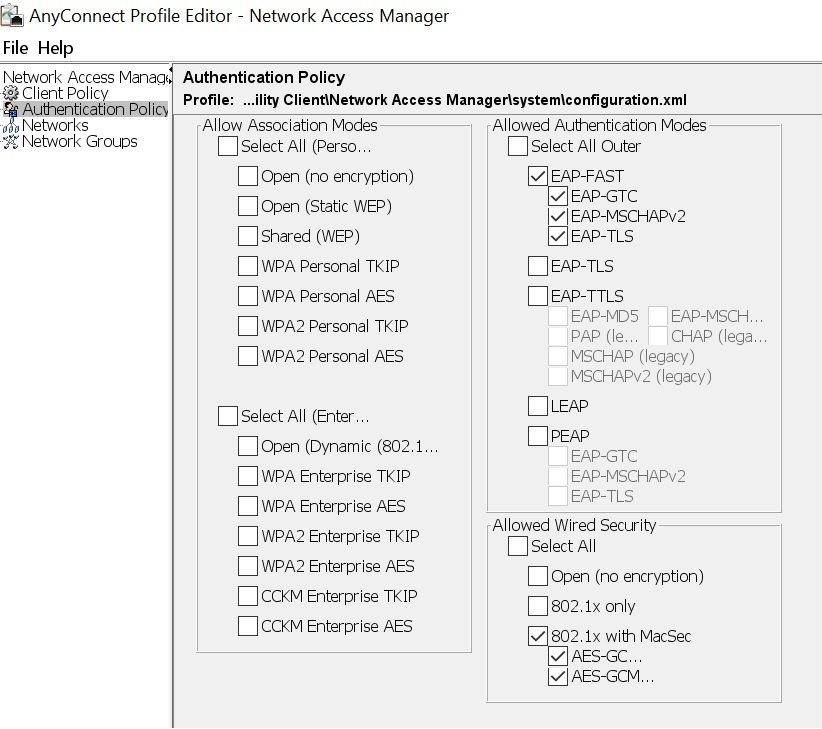
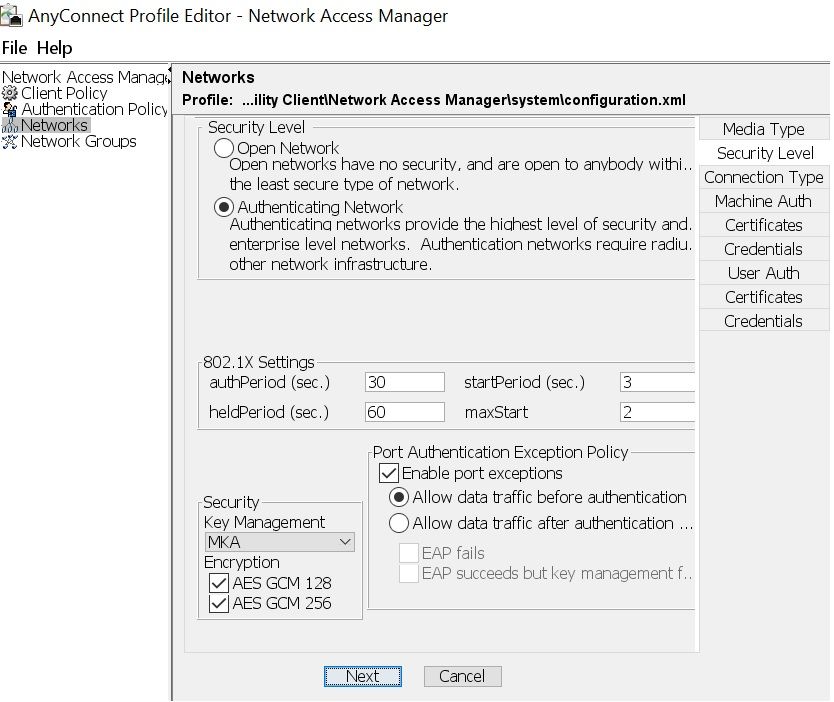
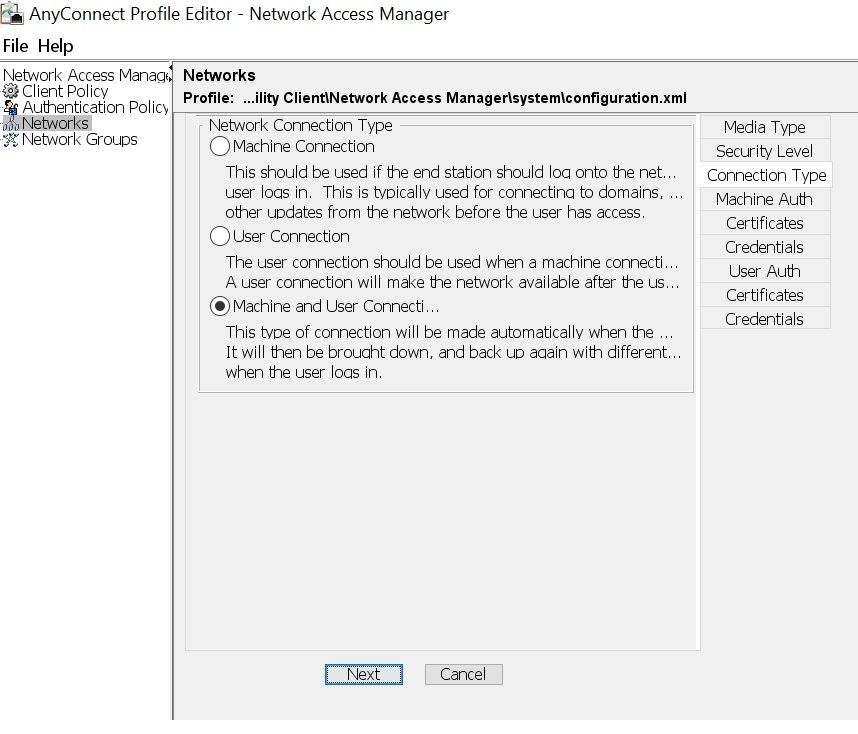
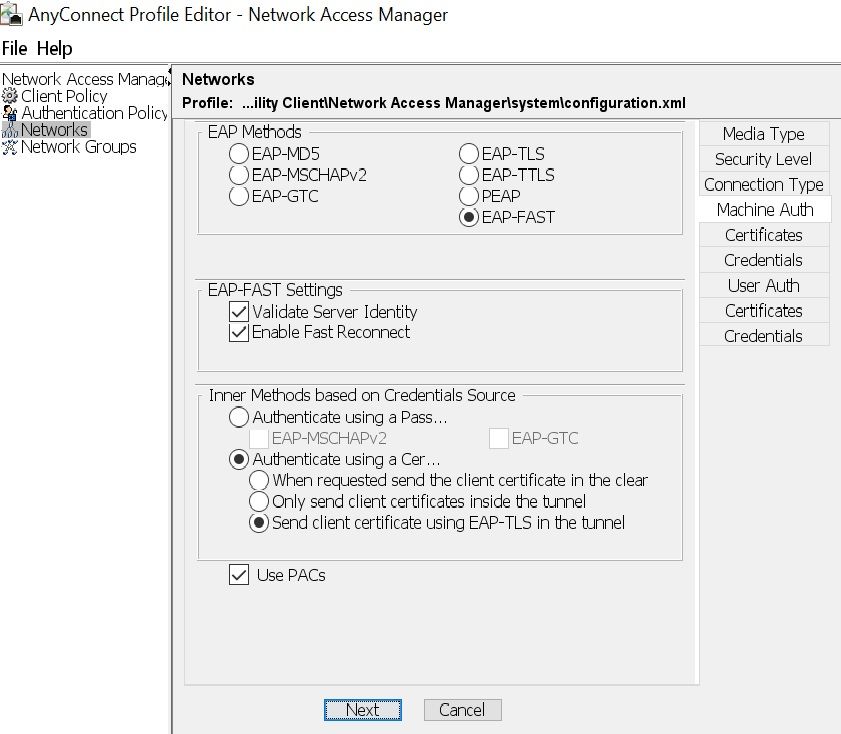
configuration: 802.1x(macsec)
encryption: GCM(software)
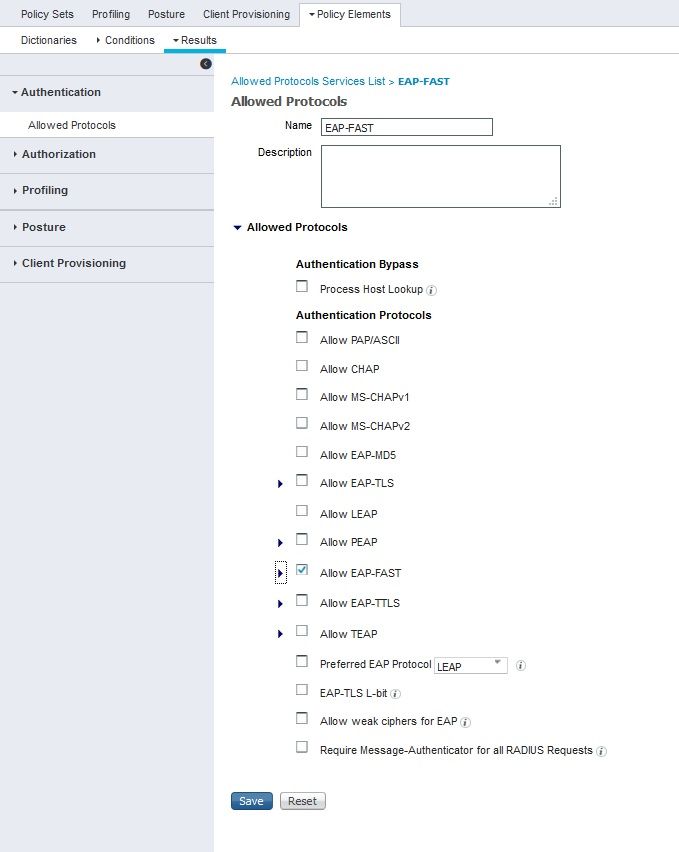
EAP methos: eapFast(eaptls
server: shows as blank???
credential type: certificate
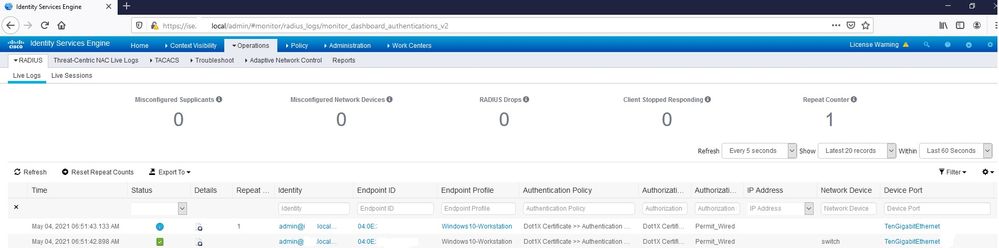
ise shows session as connected
switch shows mka session as secured
as if everything is working,yet no network
adding some info
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2021 06:31 AM - edited 05-04-2021 06:41 AM
Hi ic,
Try removing the ip access-group from the interface and let me know what you see.
Also please do
show interface gigX/Y/Z
show logging | inc gigX/Y/Z
sh mac address-table gigX/Y/Z
Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2021 07:16 AM
ip group removed -same
sh mac address-table gigX/Y/Z - shows the mac of the client,type static ports and vlan numbers
show logging | inc gigX/Y/Z - shows nothing
anything specific you want from show interface gigX/Y/Z? i have a problem uploading it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2021 07:50 AM
Hello Itay,
On the switch please shut, no shut the port that faces the host.
Then run those same commands above and post the output inline if there is a problem uploading a text file.
also post the output from
show macsec interface gigX/Y/Z
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2021 08:05 AM
sh mac address-table int te x/x/x
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
9 xxxx.xxxx.xxxx STATIC Te x/x/x
Total Mac Addresses for this criterion: 1
-----------------------------------------------
sh logging | inc te x/x/x
-----------------------------------------------
sh int te x/x/x
TenGigabitEthernet x/x/x is up, line protocol is up (connected)
Hardware is Ten Gigabit Ethernet, address is xxxx.xxxx.xxxx (bia xxxx.xxxx.xxxx)
Description: macsec test port
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive not set
Full-duplex, 1000Mb/s, link type is auto, media type is 1000BaseSX SFP
input flow-control is on, output flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:01, output 00:00:01, output hang never
Last clearing of "show interface" counters never
Input queue: 0/2000/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
26740 packets input, 3097694 bytes, 0 no buffer
Received 23493 broadcasts (8255 multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 8255 multicast, 0 pause input
0 input packets with dribble condition detected
15985 packets output, 2225253 bytes, 0 underruns
Output 1053 broadcasts (0 multicasts)
0 output errors, 0 collisions, 7 interface resets
100 unknown protocol drops
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 pause output
0 output buffer failures, 0 output buffers swapped out
---------------------------------------------------------
sh macsec int te x/x/x
MACsec is enabled
Replay protect : enabled
Replay window : 0
Include SCI : yes
Use ES Enable : no
Use SCB Enable : no
Admin Pt2Pt MAC : forceTrue(1)
Pt2Pt MAC Operational : no
Cipher : GCM-AES-128
Confidentiality Offset : 30
Capabilities
ICV length : 16
Data length change supported: yes
Max. Rx SA : 32
Max. Tx SA : 32
Max. Rx SC : 16
Max. Tx SC : 16
Validate Frames : strict
PN threshold notification support : Yes
Ciphers supported : GCM-AES-128
Transmit Secure Channels
SCI : 6C710D45ED230002
SC state : notInUse(2)
Elapsed time : 00:02:50
Start time : 7w0d
Current AN: 0
Previous AN: -
Next PN: 85
SA State: notInUse(2)
Confidentiality : yes
SAK Unchanged : yes
SA Create time : 03:23:56
SA Start time : 7w0d
SC Statistics
Auth-only Pkts : 0
Auth-only Bytes : 0
Encrypt Pkts : 0
Encrypt Bytes : 0
SA Statistics
Auth-only Pkts : 0
Encrypt Pkts : 84
Port Statistics
Egress untag pkts 0
Egress long pkts 0
Receive Secure Channels
SCI : 040E3C4C6D480000
SC state : notInUse(2)
Elapsed time : 00:02:50
Start time : 7w0d
Current AN: 0
Previous AN: -
Next PN: 270
RX SA Count: 0
SA State: notInUse(2)
SAK Unchanged : yes
SA Create time : 03:23:54
SA Start time : 7w0d
SC Statistics
Notvalid pkts 0
Invalid pkts 0
Valid pkts 0
Valid bytes 0
Late pkts 0
Uncheck pkts 0
Delay pkts 0
UnusedSA pkts 0
NousingSA pkts 0
Decrypt bytes 0
SA Statistics
Notvalid pkts 0
Invalid pkts 0
Valid pkts 65
UnusedSA pkts 0
NousingSA pkts 0
Port Statistics
Ingress untag pkts 0
Ingress notag pkts 126
Ingress badtag pkts 226
Ingress unknownSCI pkts 0
Ingress noSCI pkts 0
Ingress overrun pkts 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2021 05:38 PM
A couple of questions...
Please shut \ no shut again, then do show logging | inc X/Y/Z (just use the numerical interface identifier) There should be output from the interface flap and from the MKA negotiation.
From the other thread, I see you have a C9300-24UX.
This thread shows you are connecting to a 10G interface but at 1G speed.
Is your host connected to the NM module?
What is the manufacturer & model number of the SFP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-04-2021 11:27 PM - edited 05-05-2021 04:19 AM
update:
the thing was with mac policy.
recreated it.
now AnyConnect shows as encrypted and traffic is working.
show mka sessions shows sessions as secured.
however, running Wireshark on the client i can still see the traffic...…
so it does seem that nothing is encrypted at all, even though it all seems to work
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2021 05:25 AM
Itay, Glad to hear you got this working with a tweak to the MKA policy.
If show macsec interfafce ten1/1/1 shows MACsec as enabled && AnyConnect shows GCM encryption occurring then traffic -on the wire- is encrypted.
So, why doesn't Wireshark show the same? Wireshark is capturing too high up in the device driver to see the encrypted traffic. You can either trust that its working or get yourself a network tap; with a tap and a 3rd device running Wireshark you will get traffic that's actuallly on the wire and all you should see is encrypted traffic. You can pick taps up on ebay for ~ $100 USD.
You can see this thread where a similar question was raised.
https://community.cisco.com/t5/switching/macsec-implementation/td-p/2276670
Hope this helps
Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2021 11:08 AM - edited 05-05-2021 11:09 AM
Thanks for the help.
Got to admit,this one was rough to implement.
Cisco should publish better documantion about macsec and ibns 2.
I would be happy to help with the documentation (-:
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide