- Cisco Community
- Technology and Support
- Security
- Network Security
- NAT Issues continue with ASA 5510
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NAT Issues continue with ASA 5510
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2014 11:39 AM - edited 03-11-2019 08:36 PM
I am still having access issues when using NAT on my ASA 5510. I think it is due to the way I have my ASA setup and the usage of PAT and NAT. I am not sure of the differences in them as of yet, but because I have routers behind my ASA, it seems to me that the issues might relate to the PAT, NAT and the Routers.
Can refer to this link to see my network diagram.
https://supportforums.cisco.com/message/4145313#4145313
The problem is, I cannot seem to access any devices behind the routers.
My initial thought when I started this learning process was to use the ASA as the one point of access to the internet as a firewall. Then behind that I would have my routers and the subnets behind them, including switches and all that stuff. But there is apparently different ways of doing this and the information I get doesn't seem to be consistent, or I should say it is consistent, but doesn't work.
For some reason, I cannot seem to forward packets from the external interface (internet) on the ASA, to resources behind the routers.
I create a network object. Assign it a host. Create the NAT statement. Create the access list. and yet the packets still get denied. The error I see on the ASDM is basically always the same.
| 6 | Jan 27 2014 | 10:36:46 | 98.22.xxx.xxx | 14979 | 192.168.1.2 | 3389 | Routing failed to locate next hop for TCP from Outside:98.22.xxx.xxx/14979 to Inside:192.168.1.2/3389 |
One thing I noticed is that no matter what I specify as the port leaving my network here at work, the ASA doesn't see it as that port. RDP, for example, is supposed to use 3389. But as you see from this caption of my ASA log, I initiated an RDP connection from my work computer and when it hit the ASA is is on port 14979 which if I read this correctly is 98.22.xxx.xxx 14979 then converted to 192.168.1.2 port 3389.
I created a Object Network Group:
object network RDP-DC1
host 192.168.1.2
Set NAT within the group:
object network RDP-DC1
nat (Inside,Outside) static interface service tcp 3389 3389
Then created an Access-List:
access-list Outside_access_in extended permit tcp host 98.22.xxx.xxx object RDP-DC1 eq 3389
But the result is the same as I get when I created the one to allow http traffic on port 8080 to hit an internal address on port 80.
I don't know where my NAT issue is, but I am beginning to think it is in the PAT. Maybe I should create only static routes from the ASA to the routers and then setup the routers to allow access as needed? Right now, I believe the routers are allowing any traffic, since I have the access-list permit any any statement. That does mean allow any traffic to any location, including from the 'Outside' source?
Is the PAT trying to bypass the routers?
Here are some outputs:
ASA5510(config)# sh run nat
!
object network ROUTER-2811
nat (Inside,Outside) static interface service tcp ssh 222
object network ROUTER-2821
nat (DMZ,Outside) static interface service tcp ssh 2222
object network WEBCAM-01
nat (Inside,Outside) static interface service tcp www 8080
object network ROUTER-3745
nat (VOIP,Outside) static interface service tcp ssh 2223
object network RDP-DC1
nat (Inside,Outside) static interface service tcp 3389 3389
!
nat (any,Outside) after-auto source dynamic PAT-SOURCE interface
ASA5510(config)# sh run access-list
access-list USERS standard permit 10.10.1.0 255.255.255.0
access-list Outside_access_in extended permit tcp host 98.22.xxx.xxx object ROUTER-2811 eq ssh
access-list Outside_access_in extended permit tcp host 98.22.xxx.xxx object ROUTER-2821 eq ssh
access-list Outside_access_in extended permit tcp host 98.22.xxx.xxx interface Outside eq https
access-list Outside_access_in extended permit tcp host 98.22.xxx.xxx object WEBCAM-01 eq www
access-list Outside_access_in extended permit tcp host 98.22.xxx.xxx object RDP-DC1 eq 3389
access-list dmz-access-vlan1 extended permit ip 128.162.1.0 255.255.255.0 any
access-list dmz-access remark Permit all traffic to DC1
access-list dmz-access extended permit ip 128.162.1.0 255.255.255.0 host 192.168.1.2
access-list dmz-access remark Permit only DNS traffic to DNS server
access-list dmz-access extended permit udp 128.162.1.0 255.255.255.0 host 192.168.1.2 eq domain
access-list dmz-access remark Permit ICMP to all devices in DC
access-list dmz-access extended permit icmp 128.162.1.0 255.255.255.0 192.168.1.0 255.255.255.0
ASA5510(config)# sh run object-group
object-group network PAT-SOURCE
network-object 10.10.1.0 255.255.255.252
network-object 10.10.0.0 255.255.255.252
network-object 10.10.2.0 255.255.255.252
network-object 192.168.0.0 255.255.255.0
network-object 172.16.10.0 255.255.255.0
network-object 172.16.20.0 255.255.255.0
network-object 128.162.1.0 255.255.255.0
network-object 128.162.10.0 255.255.255.0
network-object 128.162.20.0 255.255.255.0
object-group network DM_INLINE_NETWORK_2
network-object host 98.22.xxx.xxx
object-group network Outside_access_in
object-group protocol DM_INLINE_PROTOCOL_1
protocol-object gre
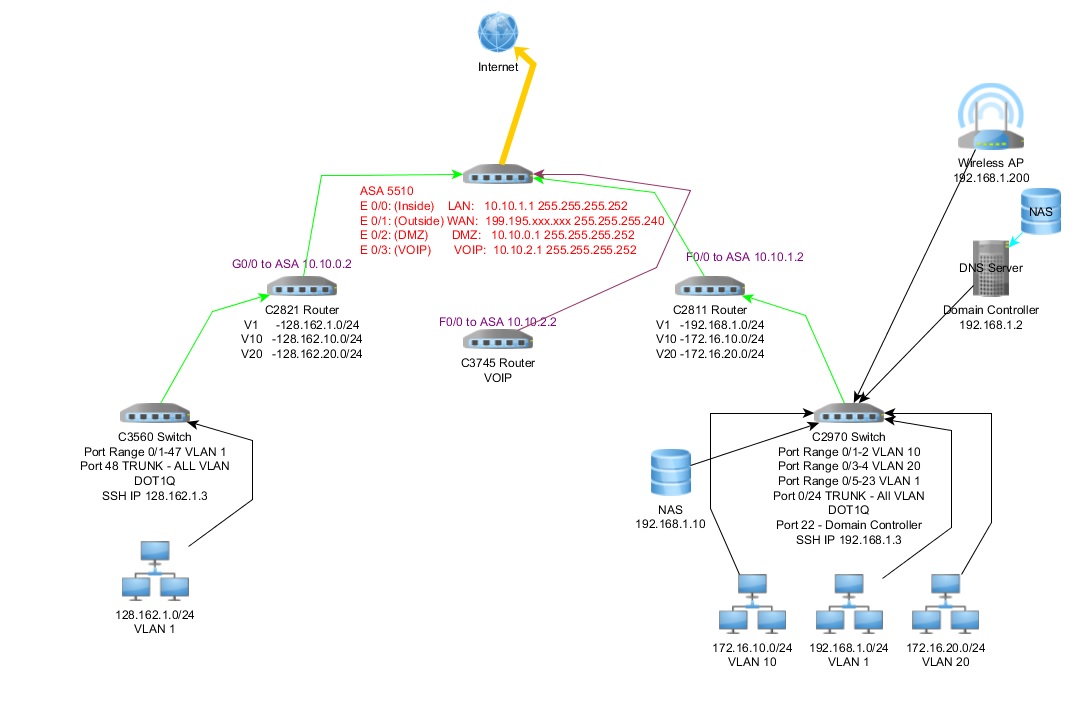
I seem to be missing something in my config preventing nat from working as it should and the work arounds that I do seem to not work properly.
The only statements that do work are the o nes that allow me to SSH into the Routers that are on each interface of the ASA. So I can ssh into the 2811, 2821 fine, but nothing behind them.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2014 02:50 PM
OK, I removed the statement under the network object for the NAT for ssh, no change.
object network ROUTER-2811
no nat (Inside,Outside) static interface service tcp ssh 222
I assume that was the NAT you were talking about?
Here is the route table as well.
ASA5510# sh route
Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is 199.195.xxx.xxx to network 0.0.0.0
S 172.16.20.0 255.255.255.0 [1/0] via 10.10.1.2, Inside
S 172.16.10.0 255.255.255.0 [1/0] via 10.10.1.2, Inside
S 128.162.1.0 255.255.255.0 [1/0] via 10.10.0.2, Inside
S 128.162.10.0 255.255.255.0 [1/0] via 10.10.0.2, Inside
S 128.162.20.0 255.255.255.0 [1/0] via 10.10.0.2, Inside
C 199.195.xxx.xxx 255.255.255.240 is directly connected, Outside
C 10.10.0.0 255.255.255.252 is directly connected, DMZ
C 10.10.1.0 255.255.255.252 is directly connected, Inside
C 10.10.2.0 255.255.255.252 is directly connected, VOIP
S 192.168.1.0 255.255.255.0 [1/0] via 10.10.1.2, Inside
S* 0.0.0.0 0.0.0.0 [1/0] via 199.195.xxx.xxx, Outside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2014 03:00 PM
Mitchell
Did you clear the xlate table for that NAT statement when you removed it ?
Can you post full config of ASA ?
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2014 03:07 PM
Shoot, no I didn't and I thought about it, but didn't .
ASA5510# sh running-config
: Saved
:
ASA Version 9.1(4)
!
hostname ASA5510
domain-name maladomini.int
enable password liSfzvir2g encrypted
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
passwd fzvir2g encrypted
names
dns-guard
!
interface Ethernet0/0
description LAN Interface
nameif Inside
security-level 100
ip address 10.10.1.1 255.255.255.252
!
interface Ethernet0/1
description WAN Interface
nameif Outside
security-level 0
ip address 199.195.xxx.xxx 255.255.255.240
!
interface Ethernet0/2
description DMZ
nameif DMZ
security-level 100
ip address 10.10.0.1 255.255.255.252
!
interface Ethernet0/3
description VOIP
nameif VOIP
security-level 100
ip address 10.10.2.1 255.255.255.252
!
interface Management0/0
management-only
shutdown
nameif management
security-level 0
no ip address
!
boot system disk0:/asa914-k8.bin
ftp mode passive
dns domain-lookup Outside
dns server-group DefaultDNS
name-server 199.195.xxx.xxx
name-server 205.171.2.65
name-server 205.171.3.65
domain-name maladomini.int
same-security-traffic permit inter-interface
object network ROUTER-2811
host 10.10.1.2
object network ROUTER-2821
host 10.10.0.2
object network WEBCAM-01
host 192.168.1.5
object network DNS-SERVER
host 192.168.1.2
object network ROUTER-3745
host 10.10.2.2
object network RDP-DC1
host 192.168.1.2
object-group network PAT-SOURCE
network-object 10.10.1.0 255.255.255.252
network-object 10.10.0.0 255.255.255.252
network-object 10.10.2.0 255.255.255.252
network-object 192.168.0.0 255.255.255.0
network-object 172.16.10.0 255.255.255.0
network-object 172.16.20.0 255.255.255.0
network-object 128.162.1.0 255.255.255.0
network-object 128.162.10.0 255.255.255.0
network-object 128.162.20.0 255.255.255.0
object-group network DM_INLINE_NETWORK_2
network-object host 98.22.xxx.xxx
object-group network Outside_access_in
object-group protocol DM_INLINE_PROTOCOL_1
protocol-object gre
access-list USERS standard permit 10.10.1.0 255.255.255.0
access-list Outside_access_in extended permit tcp host 98.22.xxx.xxx object ROUTER-2811 eq ssh
access-list Outside_access_in extended permit tcp host 98.22.xxx.xxx object ROUTER-2821 eq ssh
access-list Outside_access_in extended permit tcp host 98.22.xxx.xxx interface Outside eq https
access-list Outside_access_in extended permit tcp host 98.22.xxx.xxx object WEBCAM-01 eq www
access-list Outside_access_in extended permit tcp host 98.22.xxx.xxx object RDP-DC1 eq 3389
access-list dmz-access-vlan1 extended permit ip 128.162.1.0 255.255.255.0 any
access-list dmz-access remark Permit all traffic to DC1
access-list dmz-access extended permit ip 128.162.1.0 255.255.255.0 host 192.168.1.2
access-list dmz-access remark Permit only DNS traffic to DNS server
access-list dmz-access extended permit udp 128.162.1.0 255.255.255.0 host 192.168.1.2 eq domain
access-list dmz-access remark Permit ICMP to all devices in DC
access-list dmz-access extended permit icmp 128.162.1.0 255.255.255.0 192.168.1.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu Inside 1500
mtu Outside 1500
mtu management 1500
mtu DMZ 1500
mtu VOIP 1500
icmp unreachable rate-limit 1 burst-size 1
icmp deny any Outside
asdm image disk0:/asdm-715.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
!
object network ROUTER-2811
nat (Inside,Outside) static interface service tcp ssh 222
object network ROUTER-2821
nat (DMZ,Outside) static interface service tcp ssh 2222
object network WEBCAM-01
nat (Inside,Outside) static interface service tcp www 8080
object network ROUTER-3745
nat (VOIP,Outside) static interface service tcp ssh 2223
object network RDP-DC1
nat (Inside,Outside) static interface service tcp 3389 3389
!
nat (any,Outside) after-auto source dynamic PAT-SOURCE interface
access-group Outside_access_in in interface Outside
!
router rip
network 10.0.0.0
version 2
no auto-summary
!
route Outside 0.0.0.0 0.0.0.0 199.195.xxx.xxx 1
route Inside 128.162.1.0 255.255.255.0 10.10.0.2 1
route Inside 128.162.10.0 255.255.255.0 10.10.0.2 1
route Inside 128.162.20.0 255.255.255.0 10.10.0.2 1
route Inside 172.16.10.0 255.255.255.0 10.10.1.2 1
route Inside 172.16.20.0 255.255.255.0 10.10.1.2 1
route Inside 192.168.1.0 255.255.255.0 10.10.1.2 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 0.0.0.0 0.0.0.0 Inside
http 98.22.xxx.xxx 255.255.255.255 Outside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 Inside
ssh 98.22.xxx.xxx 255.255.255.255 Outside
ssh timeout 60
ssh version 2
ssh key-exchange group dh-group1-sha1
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username encrypted privilege 15
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns migrated_dns_map_1
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
inspect icmp error
inspect pptp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
password encryption aes
Cryptochecksum:95cd1440463ac3f
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2014 03:13 AM
Hi,
Can you please put "ip subnet-zero "command and then try.
Regards,
Naisam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2014 07:43 AM
I am sorry, I can't seem to find that command to run.
Closest I found was:
ASA5510# sh ip address inside
System IP Address:
Interface Name IP address Subnet mask Method
Ethernet0/0 Inside 10.10.1.1 255.255.255.252 CONFIG
Current IP Address:
Interface Name IP address Subnet mask Method
Ethernet0/0 Inside 10.10.1.1 255.255.255.252 CONFIG
ASA5510# sh ip address outside
System IP Address:
Interface Name IP address Subnet mask Method
Ethernet0/1 Outside 199.195.xxx.xxx 255.255.255.240 CONFIG
Current IP Address:
Interface Name IP address Subnet mask Method
Ethernet0/1 Outside 199.195.xxx.xxx 255.255.255.240 CONFIG
ASA5510# sh ip address DMZ
System IP Address:
Interface Name IP address Subnet mask Method
Ethernet0/2 DMZ 10.10.0.1 255.255.255.252 manual
Current IP Address:
Interface Name IP address Subnet mask Method
Ethernet0/2 DMZ 10.10.0.1 255.255.255.252 manual
Naisamuddin pk wrote:
Hi,
Can you please put "ip subnet-zero "command and then try.
Regards,
Naisam
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2014 07:45 AM
Jon,
I just tried removing the nat again and this time I cleared the xlate and still no go.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2014 04:06 PM
Thanks for trying to help all. I dunno what's going on. I guess I just won't be able to acess internal accests unless they are directly off a port on the ASA. I can't think of anything else to change.
jon.marshall wrote:
Mitchell
Did you clear the xlate table for that NAT statement when you removed it ?
Can you post full config of ASA ?
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2014 01:54 PM
Is it possible it is a setting on my router that is preventing access to resources behind it? I can't see anything that stands out but I am just learning this.
It seems to me the ASA is working because it allows me to SSH to the routers, I just can't access resources on the other side of the routers.
Here is the config:
CISCO-2811#sh run
Building configuration...
Current configuration : 4779 bytes
!
! Last configuration change at 04:01:02 UTC Tue Jan 28 2014 by mtuckness
version 15.1
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname CISCO-2811
!
boot-start-marker
boot system flash
boot-end-marker
!
!
enable secret 4 DWJfYBf6KhkIRmhhIhVGQWjwfuyzfaX4Im8M
!
aaa new-model
!
!
!
!
!
!
!
aaa session-id common
!
!
dot11 syslog
no ip source-route
!
!
ip cef
no ip dhcp use vrf connected
ip dhcp excluded-address 192.168.1.1 192.168.1.49
ip dhcp excluded-address 172.16.10.1 172.16.10.49
ip dhcp excluded-address 172.16.20.1 172.16.20.49
!
ip dhcp pool Mitchs_Network
network 192.168.1.0 255.255.255.0
dns-server 192.168.1.2 199.195.x.x 205.171.2.65 205.171.3.65 8.8.8.8
default-router 192.168.1.1
!
ip dhcp pool VLAN10
network 172.16.10.0 255.255.255.0
default-router 172.16.10.1
dns-server 199.195.x.x 205.171.2.65 205.171.3.65 8.8.8.8
!
ip dhcp pool VLAN20
network 172.16.20.0 255.255.255.0
dns-server 199.195.x.x 205.171.2.65 205.171.3.65 8.8.8.8
default-router 172.16.20.1
!
!
!
ip domain name maladomini.int
ip name-server 192.168.1.2
ip name-server 199.195.xxx.x
ip name-server 205.171.2.65
ip name-server 205.171.3.65
ip name-server 8.8.8.8
no vlan accounting input
!
multilink bundle-name authenticated
!
!
password encryption aes
crypto pki token default removal timeout 0
!
crypto pki trustpoint TP-self-signed-1290569776
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-1290569776
revocation-check none
rsakeypair TP-self-signed-1290569776
!
!
crypto pki certificate chain TP-self-signed-1290569776
certificate self-signed 01
3082022B 30820194 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 31323930 35363937 3736301E 170D3134 30313035 30363130
33395A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D31 32393035
36393737 3630819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100B18F F63C5121 00785DE0 854601BA EE77DAA3 21286D8C 6E700C37 237CC1BE
611023AF FBE04BBE 7B4B3233 E4E129DD A74604E5 62AA39BF 77F98D5D D63944E9
2345AE37 D93C5753 E425E85A EB22C2C9 CFC5D1A0 F800449B 0419A5C8 A0A101EC
02928172 7B30A609 71ADA3D4 68F4F484 AF2B3249 0E225DB2 C72C136A E670D761
DDE30203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603
551D2304 18301680 1461F6DE 8EF50F7B 0E46359F 421EA106 9375F65F 30301D06
03551D0E 04160414 61F6DE8E F50F7B0E 46359F42 1EA10693 75F65F30 300D0609
2A864886 F70D0101 05050003 81810049 BA55F695 8525265F ED2D77EE 8706BF10
63A7E644 202F6663 9EA5551F 47F7FC50 D4021EDD E3DC5A80 39FD161A C337D20D
71B98875 0F1FE887 649E81D3 F93F7A1B A1E18B99 A77B1A59 84DB4711 867913FD
044084FB 651ECA6E C6EDF35C E43A2946 8C01781E 26DB9484 C8740A82 4A7CA266
A0655526 CBCB4982 F30D68E9 D70753
quit
!
!
license udi pid CISCO2811 sn FTX1041A07T
username secret 5 $18dqYMcpTex8gtUfannzox.
username privilege 15 secret 4 DWJfYBf6KhhIhx8ibAAXVGQWjwfuyzfaX4Im8M
!
redundancy
!
!
ip ssh time-out 60
ip ssh authentication-retries 5
ip ssh version 2
!
!
!
!
!
!
!
interface FastEthernet0/0
description CONNECTION TO INSIDE INT. OF ASA
ip address 10.10.1.2 255.255.255.252
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
!
interface FastEthernet0/1.1
description VLAN 10
encapsulation dot1Q 10
ip address 172.16.10.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
!
interface FastEthernet0/1.2
description VLAN 20
encapsulation dot1Q 20
ip address 172.16.20.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
!
interface FastEthernet0/1.3
description Trunk Interface VLAN 1
encapsulation dot1Q 1 native
ip address 192.168.1.1 255.255.255.0
ip nat inside
ip virtual-reassembly in
!
interface Dialer0
no ip address
!
router rip
version 2
network 172.16.0.0
network 192.168.1.0
network 199.195.xxx.0
no auto-summary
!
ip default-gateway 10.10.1.1
ip forward-protocol nd
no ip http server
ip http authentication local
ip http secure-server
!
!
ip dns server
ip nat inside source list 1 interface FastEthernet0/0 overload
ip route 0.0.0.0 0.0.0.0 10.10.1.1
ip ospf name-lookup
!
access-list 1 permit any
dialer-list 1 protocol ip permit
!
!
!
!
tftp-server system:running-config 1
!
!
!
control-plane
!
!
!
line con 0
exec-timeout 0 0
password 7 101D58606050A147A
line aux 0
line vty 0 4
access-class 20 in
exec-timeout 0 0
password 7 115A485010D241575
transport input ssh
!
scheduler allocate 20000 1000
end
- « Previous
-
- 1
- 2
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
