- Cisco Community
- Technology and Support
- Security
- Network Security
- No access to an ASA's interface from behind the other one
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2014 08:02 AM - edited 03-11-2019 08:33 PM
Hi,
I'm facing the issue of not being able to access the "dmz" interface from behind the "internet" interface.
Here is a breif portray of the topology:
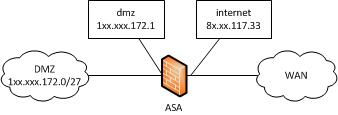
Input access list on the "internet" allows required traffic to 1xx.xxx.172.1.
No nat is configured between these interfaces.
Routing is OK because hosts in the DMZ network are accessible from the Internet.
Software version is 9.1(3).
Security level of the interfaces is the same.
Same-security inter-interface traffic is permitted.
Here is what packet tracer says:
# packet-tracer input internet udp 7x.xxx.224.140 30467 1xx.xxx.172.1 500 det
Phase: 1
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 1xx.xxx.172.1 255.255.255.255 identity
Phase: 2
Type: ROUTE-LOOKUP
Subtype: input
Result: ALLOW
Config:
Additional Information:
in 1xx.xxx.172.1 255.255.255.255 identity
Result:
input-interface: internet
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
output-status: up
output-line-status: up
Action: drop
Drop-reason: (no-route) No route to host
Please help me to find out the cause why asa cannot find the route to its own interface.
Thank you in advance.
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2014 08:11 AM
Hi,
You will not be able to connect to an IP address of an ASA interface from behind another ASA interface. This is a limitation that has been there for Cisco firewalls from as long as I can remember.
The only exception is when you have a VPN connection connected to one ASA interface then you can connect through that VPN connection to another interface of the ASA. In that case the ASA will also require that you have the following command
management-access
Where the
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2014 08:11 AM
Hi,
You will not be able to connect to an IP address of an ASA interface from behind another ASA interface. This is a limitation that has been there for Cisco firewalls from as long as I can remember.
The only exception is when you have a VPN connection connected to one ASA interface then you can connect through that VPN connection to another interface of the ASA. In that case the ASA will also require that you have the following command
management-access
Where the
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2014 11:04 AM
Hi Jouni,
Thank you for your answer. Is there any official cisco article about this limitation? I didn't find any.
The problem is that the subnet connected to the "internet" interface is routable within a certain region, and not worldwide. The subnet connected to the "dmz" interface is routable worldwide and commuters leaving that region will be able to establish VPN connection only to the "dmz" interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2014 01:08 PM
Hi,
It might be just my head working slow at the moment but I am not sure I got the actual scenario/setup.
If I understood you correctly you have users that are currently connecting to the interface "internet" for VPN connections. When they leave a certain region they will only be able to reach the ASA through the "dmz" interface?
In the case of SSL or IPsec VPN Client you do have the possibility to enable the VPN connections on both interfaces at the same time.
Though I still get the picture that the user would still be connecting through the interface "internet" but is not able to route the packets to the connected network of interface "internet" for some reason (I am not quite sure what that would be)
Here is link to a document explaining the limitation I mentioned. I could not find it referenced in newer version of the same document but to my understanding this still applies
Note
For security purposes the security appliance does not support far-end interface ping, that is pinging the IP address of the outside interface from the inside network.
Source:
http://www.cisco.com/en/US/docs/security/asa/asa71/configuration/guide/trouble.html
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2014 01:47 PM
Yes Jouni, you understood me correctly, that users will be able to connect only to the "dmz" through "internet". I enabled the VPN connections on both interfaces and got the limitation, which I created the discussion about.
Thank you for the reference. "Far-end interface" is a good term. It helped me to extend my search results in the subject, and it seems, that indeed it is impossible to make any connection to a far-end interface on ASAs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2014 08:34 AM
That sounds like the same issue I have. I have a router on each of the ASA ports 0/0 LAN (inside) 0/1 WAN (Outside) 0/2 DMZ (Cisco-2821) 0/3 VOIP (Cisco-3745).
Am I to understand that I cannot route traffic for clients behind the 2821 (DMZ) to clients behind the LAN (Inside) interface?
Wow, why would that not allow traffic between interfaces?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2014 08:43 AM
Hi,
The above limitation we are talking about simply prevents a host from behind an interface from connecting directly to another interface on the ASA. It doesnt block any traffic between the actual networks behind different interfaces. Only traffic to the ASA itself.
So consider your LAN and WAN ports. Users behind LAN will not be able to connect to the ASA by using its WAN port IP address. This however does not mean that users behind LAN could not access networks behind the WAN interface. They just cant connect to the ASA interface itself. They would have to be located behind WAN to connect to WAN interface. Now they can connect to the LAN interface as they are behind that interface.
So having traffic go through the ASA between different networks is no problem as long as Routing, NAT and ACLs are fine on all the devices. (NAT and ACL might not be present on each device naturally)
- Jouni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2014 08:49 AM
I hate to hijack someone elses post, but could you take a look at my post and tell me what I am doing wrong. I have followed the suggestions of the person trying to help, but I still cannot get from my networks behind my 2821 or 3745 to the 2811.
Here is the link. I even have a diagram up and all the configs are zipped up in the first post.
https://supportforums.cisco.com/message/4143926#4143926
I just don't see what I am missing. I added this statement:
same-security-traffic permit inter-interface
I also added his access-lists he suggested. No go
JouniForss wrote:
Hi,
The above limitation we are talking about simply prevents a host from behind an interface from connecting directly to another interface on the ASA. It doesnt block any traffic between the actual networks behind different interfaces. Only traffic to the ASA itself.
So consider your LAN and WAN ports. Users behind LAN will not be able to connect to the ASA by using its WAN port IP address. This however does not mean that users behind LAN could not access networks behind the WAN interface. They just cant connect to the ASA interface itself. They would have to be located behind WAN to connect to WAN interface. Now they can connect to the LAN interface as they are behind that interface.
So having traffic go through the ASA between different networks is no problem as long as Routing, NAT and ACLs are fine on all the devices. (NAT and ACL might not be present on each device naturally)
- Jouni
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:



