- Cisco Community
- Technology and Support
- Security
- Network Security
- PT ASA - ACL
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
PT ASA - ACL
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2020 09:31 PM
Hi everyone, im trying to find out how to specifically permit source ip going to destination.
Im using Packet Tracer.
It is working when I use this command,
access-list 100 extended permit tcp any any
access-list 100 extended permit icmp any any
access-group 100 in interface outside
but, i'd like to tighten it up to permit only specific source IP. Im using below commands and it is not working.
access-list 100 extended permit ip10.32.75.0 255.255.255.252 host 8.8.8.2
access-group 100 in interface outside
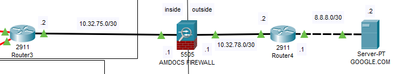
Here is the diagram Im using. Appreciate any help! Thanks alot!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2020 10:14 PM
Have you deleted the old ACL
show access-list to see what you have.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2020 12:22 AM
i actually did show running config and i see that there were no access list command running. Is my new command just wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2020 12:29 AM
Your command "access-group 100 in interface outside" should be "access-group 100 in interface inside".
Note that once you do that, ALL other traffic from the inside to the outside will be denied.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2020 05:51 AM
i am still not getting response from the 8.8.8.0/30 network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2020 06:26 AM
Please share the output of the following command (run from the ASA cli):
packet-tracer input inside tcp 10.32.75.2 1025 8.8.8.2 80
That will confirm the ASA rule logic.
You have an upstream router indicated - is it doing NAT?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2020 04:32 AM
the command is invalid. by the way, im using packet tracer simulator only.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2020 04:19 AM
Friend the Initiate of traffic is Key Point Here,
If the traffic Initiate from Inside to outside
THEN ANY ACL IN OUTSIDE WILL NOT WORK because IT WILL BYPASS IT
if the traffic Initiate from Outside to Inside THEN ACL IN OUTSIDE CAN PERMIT OR DENY TRAFFIC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2020 05:55 AM
mate, if the traffic is from inside to outside, what is the proper ACL to use which can permit or deny traffic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2020 08:41 AM
For example, you have server outside and you have host inside,
You want the host inside only only connect to tcp server outside for specific port BUT you dont want any other traffic from host to this specific server, here apply acl inside will do work and permit only tcp with port and deny other
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2020 10:50 AM - edited 10-18-2020 10:51 AM
As mentioned by Marvin, the access list 100 must be applied to the inside interface in inbound direction, that's to match the source traffic coming from the subnet 10.32.75.0/30 destined to 8.8.8.0/30. If that is in place, I would check the routing on the Router4 to ensure there is a route back to the subnet 10.32.75.0/30. If that is not in place, you need to add a static route on Router4 for the 10.32.75.0/30 subnet pointing to the ASA outside interface:
ip route 10.32.75.0 255.255.255.252 10.32.78.1
Also, I would check if the server 8.8.8.2 default gateway is set to be 8.8.8.1. Similar on Router3, it should be configured with its default gateway to be 10.32.75.1.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: