- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Restricting inbound access to specific IPs on FTD 1120 using FDM
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2021 01:56 PM - edited 03-21-2021 01:57 PM
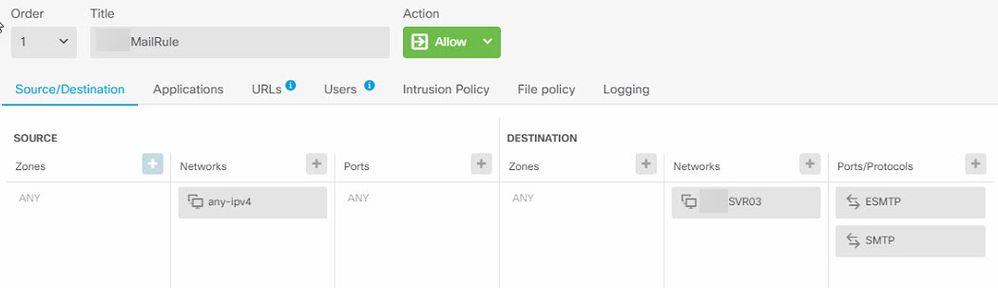
A customer is running an FTD 1120 using Firepower Device Manager. They had ports HTTPS, SMTP and ESMTP open to their Exchange server, and it was accessed due to the Exchange flaw. We turned off HTTPS access, so that the rule currently looks like this:
We are beginning a migration to Office 365 and it appears we're going to need to open ports back onto the firewall for the migration tool, and I want to do it only from the provider's specific IPs. I need to make sure I don't configure this incorrectly, so I wanted to check first. I don't believe I can or want to edit the existing rule, but create a new rule for HTTPS.
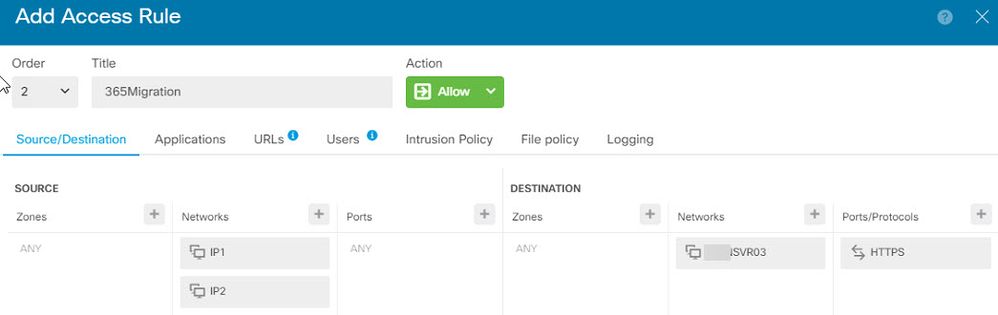
I think in this rule the SOURCE network will consist of network objects I create for the specific IPs needed, the DESTINATION network will be my server like in the rule above, and the DESTINATION port will be HTTPS. So it will looks like this:
Will this rule open up HTTP to the specific IPs while keeping the server protected from the rest of the Internet? Thanks in advance for any help.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2021 01:30 AM
Hi @vtxchris
This rule will permit inbound https from those 2 IP addresses.
Assuming you have a default deny rule then yes you should be fine.
If in doubt, you could run packet-tracer from the known source which should be permitted, re-run and confirm denied.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2021 01:30 AM
Hi @vtxchris
This rule will permit inbound https from those 2 IP addresses.
Assuming you have a default deny rule then yes you should be fine.
If in doubt, you could run packet-tracer from the known source which should be permitted, re-run and confirm denied.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2021 07:48 PM
Hey Rob, thanks for your assistance. One colleague suggested I specify Outside as the source zone and Inside as the destination zone, but does that really make a difference? I don't see that it would make the rule more secure, just more specific.
Thanks,
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2021 01:12 AM
@vtxchris Yes you could add the outside zone, it probably won't make much difference if you are permitting traffic from just those 2 known IP addresses.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2021 04:38 AM
Great, thanks for your help!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide